SSL, TLS, HTTPS Explained
861.13k views919 WordsCopy TextShare
ByteByteGo
To get better at system design, subscribe to our weekly newsletter: https://bit.ly/3tfAlYD
Checkout...
Video Transcript:
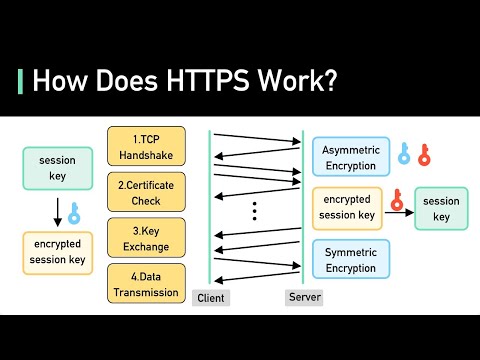
foreign about https that these days most websites require it how does https work we'll answer this question in this video Let's Dive Right In without https the communication between the browser and the server is in plain text this means that the password you enter or the credit card number you send over the internet can be read by anyone who has the ability to intercept it https is designed to solve this problem to make the data sent over the Internet unreadable by anyone other than the sender and the receiver https is an extension of the HTTP protocol we discussed HTTP in an earlier video check the description it would like to learn more about it with https data is sending an encrypted form using something called TLS TLS stands for transport layer security if the encrypted data gets intercepted by a hacker all they could see is jumbo data let's take a look at how the TLs handshake works there are several steps step one just like in the case for HTTP the browser establishes a TCP connection with the server step two this is where the TLs handshake begins the process sends a client hello to the server in this Hello message the browser tells the server the following things one what TLS version it can support it could be TLS 1. 2 TLS 1. 3 Etc two what cyber Suite he supports a cyber Suite is a set of encryption algorithms to use to encrypt data they're receiving the client hello the server gets to choose the Cyber suite and the TLs version to use based on the options it got from the client it sends those in the server Hollow message back to the client the server then sends the certificate to the client the certificate includes a lot of different things one of the key things is the public key for the server the client uses the public key in something called asymmetric encryption in a symmetric encryption a piece of data that is encrypted by a public key can only be decrypted by the private key we'll discuss how this is used in a bit this concludes step two the hollow phase of the TLs handshake at this point the client has a service certificate and the client and server have agreed on the TLs version and the Cyber Suite to use now to step three this is the step where the client and the server come up with a share encryption key to use to encrypt data and this is where the asymmetric encryption come into the picture again with a symmetric encryption the data encrypted on the client side using the public key from the server can only be decrypted by the server this is how the client sends an encryption key safely to the server over the wide open internet all this is done in the client key exchange message the exact detail varies depending on the Cyber Suite used here we use RSA as an example since it is the easiest to understand with RSA the client generates an encryption key also called a session key encrypts it with the server public key and sensor encrypted session key to the server over the Internet the server receives the encrypted session key and decrypts it with its private key now both sides hold the session key and this is where they enter step 4 of the TLs handshake where they use the session key and agree upon cyber Suite to send encrypted data back and forth in a secure bi-directional Channel now you may ask why don't we just use a symmetric encryption for everything why switch to symmetric encryption at all the main reason is that asymmetric encryption is computationally expensive it is not really suitable for bulk data transmission before we close there are two final points I would like to discuss first the handshake we talked about applied to TLS 1.
2 while the latest version is TLS 1. 3 and TLS 1. 3 is supported on all major browsers as we can see in our illustration TRS 1.
2 takes two network round trips to complete this is one of the major improvements of TLS 1. 3 it optimizes the handshake to reduce the number of network round trips to one we decided to talk about TLS 1. 2 because we reviewed TRS 1.
3 as in optimization as with most optimizations it is a bit harder to explain that's why we chose TRS 1. 2 Instead The Core Concepts in TLS 1. 2 still applies to TLS 1.
3 the second final Point we'd like to discuss is that in the explanation above we use RSA for asymmetric encryption to securely exchange the symmetric session key again we chose to RSA because it is easy to understand however asymmetric encryption is not the only way to share the session key between the client and the server in fact in TLS 1.
Related Videos

5:20
What happens when you type a URL into your...
ByteByteGo
360,543 views

43:29
HTTPS, SSL, TLS & Certificate Authority Ex...
Laith Academy
155,929 views

7:38
SSL/TLS Explained in 7 Minutes
Sematext
58,754 views
5:17
Proxy vs Reverse Proxy (Real-world Examples)
ByteByteGo
612,395 views

24:20
Transport Layer Security, TLS 1.2 and 1.3 ...
Hussein Nasser
267,902 views

16:59
TLS Handshake Explained - Computerphile
Computerphile
575,419 views

24:00
Man Insults Keanu Reeves on a First Class ...
Heroic Acts
2,431,681 views

15:27
Donald Trump, JD Vance dance with their wi...
TheColumbusDispatch
5,617,581 views

7:01
I attended Trump’s inauguration yesterday....
Senator Bernie Sanders
2,588,874 views

26:08
Day 20/40 - SSL/TLS Explained Simply - How...
Tech Tutorials with Piyush
10,834 views

27:59
TLS Handshake - EVERYTHING that happens wh...
Practical Networking
138,476 views

10:45
The Weather Is About To Change In A BIG Wa...
Max Velocity - Severe Weather Center
334,881 views

6:55
Algorithms You Should Know Before System D...
ByteByteGo
223,528 views
7:37
HTTP 1 Vs HTTP 2 Vs HTTP 3!
ByteByteGo
362,997 views

13:19
Proxy vs Reverse Proxy vs Load Balancer | ...
TechWorld with Nana
277,609 views

1:18:18
14. SSL and HTTPS
MIT OpenCourseWare
226,123 views

15:33
Transport Layer Security (TLS) - Computerp...
Computerphile
492,355 views

14:25
SSL Handshake Explained | What Is SSL/TLS ...
Simplilearn
90,163 views

12:27
Network Protocols - ARP, FTP, SMTP, HTTP, ...
Practical Networking
2,049,880 views

12:09
How TLS Works?
High-Performance Programming
59,402 views