How DKIM SPF & DMARC Work to Prevent Email Spoofing
105.55k ยอดวิว2534 คำคัดลอกข้อความแชร์
Thobson Technologies
In this tutorial, we explain how SPF, DKIM & DMARC work to protect your email server from spam relat...
บทถอดความวิดีโอ:
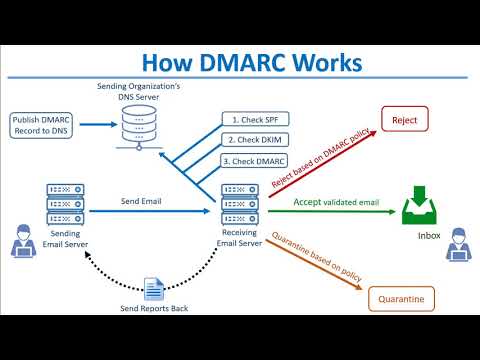
spf dkim and dmarc are three tools that can be used to help prevent spoofing and validate email authenticity for your email service or domain and i'm going to explain how they work and uh show you how to set them up in this uh in this lesson here so first let's talk about spf which stands for sender policy framework before i get started on the diagram that i'm about to show you just from a high level spf is a mechanism that tells servers receiving email servers what servers are allowed to send mail on behalf of your domain it uses an spf record published in dns to do that so when you're setting up spf you'll publish your spf record to dns to the sending organization's dns server and then when an email is sent out from your domain the receiving server receives it and performs an spf record lookup by querying dns for the spf record of the ascending domain to verify whether it came from an authorized sending server or ip address and then if if there's no spf record or if the spf record of the domain specifies that the server that the message came from was not authorized to send on behalf of that domain then the message can be rejected or marked as spam or if it passes spf validation then the message can be accepted for delivery by the receiving email server and then sent placed into the recipient's mailbox now of course there are some caveats and some other details when configuring spf for example when considering things like sub domains or other servers that are allowed to send such as smart hosts and things like that but for purposes of this lesson this will provide a good overview this is what an spf record looks like so for example you can see here the every spf record starts with a v equals that's the version number spf one they're all they're all the same and then now again this is a very simplified version of an spf record there are a lot of other tags and things you can put in an spf record but for purposes of simplicity this spf record specifies the version spf1 the ip address that is allowed to send mail on behalf of the domain example. com and then whether all messages should be sent from that specific ip address or if there are some exceptions based on smart hosts and things like that so there that's where the other there are a variety of other tags and syntax measures that come into play so as i mentioned spf can get a little bit more advanced or actually quite a bit more advanced than that so there's a lot of good information online specifically openspf. org is a good resource for how to format your spf records there are you know as i mentioned there are other tags and mechanisms that are included in an spf record so for example the the vspf that we saw in the spf record that i showed you that's always included but you can also add some other tags such as your mx record tag a record tags and things like that and then the vspf record policy accept reject mark it as spam or questionable or other other tags that you can add so this site here has a lot of great information on spf and how to configure your your spf records so you can refer to this for a more advanced tutorial on spf both in daemon and security gateway can check incoming mail for spf records so in security gateway for example i'll show you what it looks like when an spf lookup is performed on a message so i'm just going to select spf and my reason is section here when doing a search in the message log to pull up an example these are all the messages that were rejected or quarantined based on spf so let's pick this one that was quarantined for example and looking through the transcript we're looking for the part the section where the spf record lookup was performed and that's right here so security gateway looked up the spf record on company.
com and this is the ip address that the email came from this is the domains spf policy right here and then the connecting ip was evaluated against all of the data found in the sending domains spf record and based on that spf record security gateway determined that it was a soft fail this this symbol here this tilled symbol so uh it was quarantined as a result and two points were added to the message score and then spf processing uh ended the next tool to help prevent spoofing and tampering with messages called dkim domain key is identified male and the way this works is dkim is a mechanism that signs all outbound messages from a domain with a specific key uh we'll call it a private key and then a corresponding public key is published to dns to the dns records and then the receiving server can compare the two keys to see if they match and i'll explain in this diagram here so the sending server publishes their public dns key their public dchem to dns and then when the sender sends an email the sending server signs the email with their with the associated private key the receiving server then sees that the message is signed by dkim looks up the dkim record in dns taken from the domain that was passed in the dkim signature of the email message compares the signature in the email message or the dqm key in the email message with the public key published to the sending domains dns record and if they match then the message can be delivered but if they don't match then the message is can be quarantined or rejected based on your policies that you have in place and just to show you a little bit more from a real world perspective on how this works i'll use security gateway as an example here because with it with most mail servers security gate or gateways whether it's mail whether it's whether it's security gateway or mdamon or an exchange server they most of them have the capability of signing outbound mail with dkim and it works by creating a key what we call a selector and a key and the key is published to dns so just as an example i've created a selector in security gateway called test and i've opted to sign all outbound messages using domain keys identified mail using dkim once i've created the selector then you can click on here to view the dns configuration or the public key in other words for that selector and then this is what you will publish to your dns record so with my dns set up here on my dns server here is my dkim record that i've published to dns it's it's a plain text record that you publish to dns so the record name would be dcam it would populate with dkim plus your domain and then you would enter the the text here the key that was generated from your mail server or gateway so now that we've discussed dkim and spf let's talk about how dmarc works because dmarc is a mechanism that kind of ties the two together and allows domain owners to tell receiving domains or receiving mail servers how to handle messages that claim to come from their domain that did not align with or spf and the way this works is the sending organization publishes a dmarc record to dns this dmarc record has i'll show you an example of it but it explains what to do with messages that failed or were questionable as whether they passed or failed at dkim or spf you know for example quarantine the message or reject the message so the sending email server sends an email and then the receiving email server looks at the domain at the sending domain and first checks spf for alignment then it checks dkim to verify if the public and private keys match if it is signed by dkim and then it checks the dmarc record to determine what to do with messages that did not pass spf dqm or both and then if the message is accepted it is uh delivered to the recipient's inbox or it can be rejected based on the sending domains dmarc policy or if the sending domain has a policy of quarantine then the message can be quarantined and also an added benefit of dmarc is that you can specify in your dmarc record whether or not you want other mail servers that receive email claiming to come from your domain to be able to send you back reports providing an overview of how your domain is being used so these are called forensic reports and aggregate reports this is an example of a dmarc record and the syntax that is used for the dmarc record so they all begin with v equals dmarc they have a p equals tab and here's a key of all the different tags down here in the bottom so for example the p equals tag is the policy and this will say reject or quarantine or none an optional tag is the percent tag which tells receiving servers what percentage of messages to handle based on the policy so a good rule of thumb for example when deploying dmarc is to start with a if you start with a policy of none for example you don't need a percent tag but then if you go onto a policy of quarantine or reject then you can start with a smaller percentage as you get more reports on how your domain is being used and then if you need to make any changes to how your domain is being used during this time then having a lower percentage rating here allows fewer messages to be rejected or quarantined at least until you get your domain nailed down tight with dkm and spf and then once everything is configured properly with dkim and spf in other words your spf record is valid for all sending mail servers or gateways or devices that send on behalf of your domain and all of your dcm signed messages are are matched up properly and everything else looks good then you can ramp up that percentage rating accordingly there's an ru a tag which stan which is the a stands for aggregate and that's the aggregate report that is sent to an e an address that you specify here usually it's the postmaster so when you put the rua tag in your dmarc record you're telling receiving mail servers where to send aggregate reports which are reports on how your domain is being used you also have an ruf tag which is similar which is where to send failure reports these are reports for messages that failed your dmarc that weren't aligned with dkm and spf based on your dmarc record and this is the address you can send those failure reports to so as you can see here there are a variety of other tags you can put in a dmarc record so you can find a lot more information on dmarc. org on their website there are lots of tutorials and lots of resources on how to format your uh your dmarc record here's an example of a dmarc record i created for one of my test domains here so again it's got the v equals d mark i have a policy of reject here with an address where i want aggregate reports to go an address where i want failure or forensic reports to go as well so again the dmarc.
วิดีโอที่เกี่ยวข้อง

17:15
How DKIM SPF & DMARC Work to Prevent Email...
MDaemon Technologies
115,910 views

1:14
What are SPF and DKIM?
Google Workspace
197,181 views

1:00:37
#AzureBacktoSchool 2024 - Alan Kinane - Az...
Azure Back to School
56 views

7:21
What is SPF, DKIM, DMARC, and BIMI | Easy ...
Jason Rebholz - TeachMeCyber
3,358 views

14:14
DNS Records Explained
PowerCert Animated Videos
313,880 views

17:37
Microsoft 365 SPF, DKIM and DMARC; Improve...
Jonathan Edwards
57,715 views

47:56
DMARC Reporting & Analysis: What Happens Next
Global Cyber Alliance
20,066 views

26:00
SPF, DKIM, DMARC was never so simple! // E...
Christian Lempa
25,651 views
20:25
Best Practices for Protecting your Mail Se...
Thobson Technologies
140 views

19:36
DO NOT design your network like this!! // ...
NetworkChuck
3,293,361 views

31:12
Email authentication Explained, SPF, DKIM,...
Office365Concepts
6,504 views

22:59
Email Header Analysis and Forensic Investi...
13Cubed
147,939 views

34:46
Enhancing email delivery with SPF, DKIM an...
Amit Nepal
34,021 views
10:13
Lesson 13: How Email Works
Center for Cybersecurity Innovation & Outreach
159,001 views

12:44
Setting SPF, DKIM and DMARC Domain Records...
SellerSmile
875 views

14:32
NGINX Tutorial - What is Nginx
TechWorld with Nana
174,511 views

21:31
12 Days of Defense - Day 4: How to Analyze...
John Hubbard
26,674 views

10:30
SMTP Overview
Learning Forum
11,130 views