ever downloaded a shiny new program only to realize it wants you to cough up some cash before you can use it we've all been there staring at that paywall you might even have been tempted to venture into the Shady corners of the internet to find a work around but have you ever wondered how these activation mechanisms actually work and how hackers or crackers manage to bypass them programs are written in languages like C++ Java and python these languages are super friendly for humans but absolute gibberish to computers to bridge this communication gap the code gets
translated into machine code a glorious mess of ones and zeros that your computer can finally understand this transformation process is called compilation now this machine code can be displayed in Assembly Language which is basically machine code with a slightly better outfit it's still pretty close to the hardware so instead of highle commands you get to deal with cryptic instructions like move ebx 23 which is just a fancy way of telling the computer to put the number 23 in the ebx register software activation checks come in two flavors online and offline online checks are the nosy
ones they verify your ownership by chatting with a server somewhere out in the cloud you type in your key and the software sends it off along with the unique identifier of your machine the server checks its list and if your key is legit it sends back a thumbs up and your software is activated offline checks on the other hand are more like an introverted puzzle the software uses an algorithm built into itself to verify your key when you enter your activation key and email this algorithm does its thing checking the key against some internal rules
these algorithms can range from simple like checking a basic pattern to brain meltingly complex involving cryptography and stuff that makes you wish you'd PID more attention in math class enter the crackers who make it their mission to bypass these activation mechanisms they use reverse engineering which is a fancy term for taking the software apart to see how it ticks to do this they wield tools like disassemblers and debuggers disassemblers turn machine code back into Assembly Language making it slightly more readable debuggers let crackers run the software step by step pausing a will to poke around
and see what's happening under the hood the process usually starts with the cracker hunting down the activation code Often by searching for tell tail strings like invalid key or activation required once they found the code they study how it works this might involve checking specific bytes calculating a check sum or decrypting some data after understanding the activation process tweak the code to bypass it this can mean replacing critical instructions with noop no operation commands or changing conditional jumps to alter the program's flow with the code modified crackers create a patched version of the executable often
Distributing it alongside the original installer users then replace the original executable with the patched one and they've got a free albeit illegal copy of the software but software developers aren't just sitting around twiddling their thumbs they've got Tricks up their sleeves to make reverse engineering harder code obfuscation makes the code look like a tangled mess of spaghetti as an example I'm going to crack a reverse engineering crackme program just a heads up these crack mes are made specifically to be cracked they're not real programs they're designed for this purpose I'll be working on a crackme
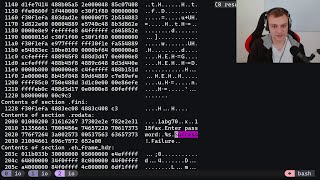
called Pride crack C by Pride it's written in C or C++ and is a 32bit program I'll be using X32 dbg for this if you don't have x32dbg make sure to download it first let's open the program and see what it does it asks for a name so I'll enter Bob then it asks for a serial key I'll enter a random key like 1 2 3 4 5 6 it says false serial key and exits now we know the program uses the msvcrt do system call to handle this let's search for that in x32dbg once
we find it we'll start looking for the right serial key after opening the program in x32dbg I'll search for intermodular calls and find msvcrt do system double clicking on it we find some code related to the serial key check we see a compare instruction checking the user input against a stored value we need to make sure this comparison passes I'll set a break point at the jump if not equal instruction and run the program again entering Bob in 1 2 3 4 5 6 when the breako hits I'll check the values being compared we see
our input 123,456 being compared to a stored value the stored value is calculated using the length of the name and some arithmetic operations let's find out how this value is derived the name length is stored in the eax register and some operations are performed on it I'll use Python to recreate this calculation let's assume a name with five letters like bread the length is five and we add 0xca to it then XO with 0x 3d8 d40f here's the python code to generate the serial key the generated key can now be used I'll restart the program
enter the name Brad and use the generated key it works and that's how we crack this program using X32 DB now here's the serious part using cracked software is illegal and it's risky you could face legal consequences and cracked software often comes with unwanted bonus features like malware plus you miss out on support and updates leaving you vulnerable to bugs and security vulnerabilities so while the technical Wizardry behind bypassing software activation is undeniably fascinating its best to stay on the right side of the law thanks for tuning in and as always stay safe [Music]