CompTIA IT Fundamentals (ITF ) FC0-U61 - Full Course
191.36k views66255 WordsCopy TextShare

Technical Institute of America
Here is the full course for CompTIA IT Fundamentals
My Udemy class for CompTIA A 220-1101 Core 1
...
Video Transcript:
if you're thinking about entering into the world of it to become a system administrator Network admin security admin or something like that then you need to start here this is comp's it fundamentals this is a video that covers the entire compia it fundamentals exam it covers every single one of the objectives and in this video I'm going to show you how to pass that test but most importantly I'm going to give you the knowledge you need in order to succeed in the other classes you see I've been teaching CompTIA classes for over 20 years now
I hold over 60 different certifications and I've met thousands tens of thousands of people entering into the field of it and one of the things that a lot of people lack is just basic it skills like do you know the difference between how we measure the speed of a computer versus the storage do you know what's the difference on a computer motherboard what does the hard drive do versus the RAM do you know how software is built do you know what are drivers if you do you know what maybe this course isn't for you but
you should still go through it to see it if there's any gaps that you're missing again this is by the way this course is 100% free you don't need to pay for anything it's the entire course is in this video so what I recommend is before you study your A+ before you study your net plus your Security Plus before you study your cisp maybe you need a brush up on the technology watch this entire course it's about six seven hours so go through it now I did record this course about two years ago and we
have used it to give to all students that takes classes with us because it's just useful for them to learn basic Computing everyone should by the way should know this so enjoy this course as I go through it I have the exam objectives listed below there's some links below for practice exams if you actually want to take the certification exam it's not mandatory but just in case you want another certification I have a link to some practice exams that we did also so enjoy the course and have fun learn in or enter in the world
of it before we get started in this course let me give you a brief introduction to me I'm Andrew Ramel I've been teaching it courses over the last 20 years to tens of thousands of students around the world in my full-time job I was a system administrator network administrator and a pentester in the world of it security I worked on that Blue Team and Red Team in it security right now I hold over 60 different certifications and I teach mostly it security classes you would find courses things like Security Plus certified ethical hack certified information
system security professional certified information systems manager and systems Auditors mostly the courses that I teach but I am happy to teach some basic it Concepts because I believe if you don't have the basic it understanding studying for things like your A+ or net plus or your Security Plus could be very difficult so I'm really happy to present this course let's get started in this video I'm going to be covering the actual exam what's the exam number how many questions you have basically what to expect on exam day when taking this particular certification so I got
a little slide here that I want to go over this information with you so the first thing up I want to talk about here is going to be the exam code now this is an important number right now the exam code for this current um it fundamental exams you're taking is fc0 u61 that is current exam code previous exams was like fc0 u51 would have been uh the previous code to that so fc0 261 why do you want to know this number because when you're registering for the exam at Pearson view the people that administers
the exam you need to make sure you see that code and make sure you select the right exam because many years from now or soon there may be a new exam and sometimes they have two exams running concurrently an old one and a new one and you got to know which one you're selecting okay this exam came out in September of 2018 now that is a good time backwards considering I'm doing this video in 2022 to uh the comp exams can last 3 4 5 years before they're updated we do expect an update to this
exam relatively soon one thing I want to point out though is when you're certified in one exam you're basically going to stay certified basically for life if you keep getting what's called contined education so for example if you're certified in A+ certification uh and you certified in one in a certain series like let's say you're certified in the 900 series but then the 1,000 or the 11,000 or the 12 or the 1100 or 1200 series exam comes out you don't really need to retake the exam again so you should maintain what's called continuing educational credits
so it doesn't really matter what exam you take as long as you take it you're certified uh as long as you keep renewing it you don't have to take the exam again so it really doesn't matter what version of the test you're taking now let's talk about the actual exam itself so this is the 60 Minute time limit and you have a maximum of 75 questions and they're all multiple choice now I want to talk a little bit about the timer here because the timer is important the exam itself is not incredibly long okay uh
most of my students that take this certification is able to finish it within 30 minutes to 45 minutes I've never heard of a student taking this exam that actually ran out of time and I don't think you will too expect to be there for about 45 minutes minutes if you read the question relatively quickly you do all the practice questions in this course I think you're going to be able to finish it in 45 minutes multiple choice now this is important because other compy exams has a variety of questions such as multi you have to
select multiple answers or there simulations or what's called performance-based questions none of that this is a straightforward exam with just multiple choices no fill-in the blanks nothing if you get ABCD you select one of the choices you do need 650 out of 900 now CompTIA uses a scoring system of between 100 to 900 to grade your exam you're going to have to accomplish 650 which is 72% on that test so you need 72% of the 75 questions that they're going to give you in order to pass this exam now that score isn't Rel isn't super
high but it is not very low either you know some exams are like 60% it's not like 80% so it's right there in the middle which I think is a decent Fair grade exam fee this number never comes down this number only gets bigger the exam fee is $134 as of today you watch this video a couple years from now it's going to be much more than that so something to think about uh as time goes on this exam will get more and more expensive as time progresses okay so this is your exam information things
to know about here hey 60 60 Minutes 75 questions all multiple choice you need 72% to pass and if you can get that you're going to H your exam in this video I'm going to be going over a brief description of the six domains that makes up the actual exam now to follow along with me you should download the compy exam objectives if you're watching this on this platform uh I probably would have attached it um as a downloadable link here and the and the objectives is something that you can get from the comp his
website what the objectives does is that it goes through all of the different topics that's going to be covered on the actual test and that's what we're going to be taking a look at right now so here is the six domains that we have and I'm also going to be laying out the course like this so as you go through the course you'll know this is what I'm expecting right now so let's get into this so the first thing up domain one is going to be what's called it Concepts and terminology 177% of your exam
what are you going to learn here well I'm to teach you some basic conceptual terms like what's a bit versus a bite what exactly are uh binary right you have to know binary is a base two or decimal is a base 10 system there actually questions on this you have to know simple not complex Simple Theory on troubleshooting like troubleshooting steps you're going to get questions on that also the next thing we'll move on to his infrastructure 22% of the exam you got to have basic knowledge of of things like connectors motherboards Ram CPU if
I show you uh an SV video connector versus a DVI connector which one supports a higher data rate things like that you're going to need to know you should also have an understanding of certain networking gear like what there's a router does or switch to we're going to cover that in that section the next one up is application and software now there's going to be a variety of application and software that you should be familiar with for example you you should know that a word processing is like Microsoft Word and what we use it for
Microsoft Vio is a diagram in software how does that work and what we use it for productivity software you should know operating systems and all the different forms of it that is out there Linux windows and so on the next thing up we have is software development not a lot of questions here just 12% by other was 18% in software development you got to understand simple concept of how software is made you should understand for example like what is a loop what is a variable when you're programming codes now you don't need to be a
programmer to pass this particular exam but you do need to know certain uh you do need to know certain scripts that are out there and as an entry-level technician or people getting into this you should be able to read some of these scripts like an if then statement that is used in software development we'll cover that database fundamentals all data in today's world is stored in some kind of database whether it's an unstructed unstructured storage or a structured storage something stored in a SQL database also known as a relational database what exactly is the difference
we'll take a look at that in that section at 11% now security is a big Topic in this world comes in as the second biggest domain that you have here 20% you going to need to understand basic security Concepts and basic security controls confidential versus integrity versus availability different types of security control that are out there to help secure like different forms of encryption different forms of Windows permissions and so on you should be familiar with really not complex security stuff but more more basic things add up you get 100% so when you're going through
your exam you're going to get 20% of your questions on security basically you can get 22% of infrastructure so that's what this is telling us when we sit down on the day to take her exam now ITF you got to remember it's not a very uh indepth certification you don't need to get indepth into these things for example security is something you can get indepth into and you can spend a career doing it people that work in software development can spend their entire lives developing en Cod and software in this course I want to get
you a just a basic understanding of what these things are and your exam is basic and conceptual understanding of these topics so don't go study in depth just get a high level overview of what these topics topics are so you can Ace your exam in this video I'm going to be covering notational systems in particularly the numbering systems that we use in technology now in the world of technology we're basically going to use three numbering systems decimal binary and hexadecimal for your exam don't expect really complex questions on this but I do want you to
understand that uh they may ask what's the base of this system oh let me show you what this is and tell me is this a hexadecimal is it a binary or or or is it a decimal so that's really all you have to know so don't bust your brains on this let's get into it let's take a look at it so the first one up we're going to talk about is of course a decimal why because decimal is what we use all of our Lives we have studied in decimal but you're doing math in grammar
school or you were doing calculus in in college it's all based on decimal humans mostly read decimals it's the computers that mostly reads binary and hexadecimal now one thing you have to know for your exam is that decimals are known as a base 10 system now what does that mean well it means that in a decimal systems there's 10 possible combination of numbers 0 to 9 is what they are so in any number that you ever looked at whether it's 1 32 56 1,000 2,000 3,000 1 million and 56 they're all the digits within them
are going to be zero or 0 to n so 0 1 2 3 4 5 6 7 8 9 this is known as a base 10 why because there's 10 possible combinations of digits that are out there the next one that we're going to want to know is what computers read binary code computers read binary and binaries are basically zeros and ones and they read this because of the way the processor works now when I get in to hardware and we're going to talk about processors we're going to show you I'm going to show you
what a processor looks like and why they read binary because they're made of transistors and I'm going to show you that when we get there so binaries are just ones and zeros so when you see somebody writes a binary it's going to look something like this is either going to be zero or one and z or 1 0 0 1 or 0 1 0 00 0 1 0 1 01 now there are ways to convert binary to decimal and back and forth I covered that in the A+ net plus and so on you don't need
to know that here for for ITF but it's something that you should be familiar with coming up later in your career so binary is known as a base two why because there is only two numbers in each binary the next one we have is a hexadecimal now hexadecimal is something that we use for example in representing the hardware address of your computer known as your Mac address hex decimal is a base 16 how do I get that well first of all it's 10 numbers 0 to 9 and then it's a to F so a b
c d e f six letters base 16 so 10 numbers and six letters creates this heximal heximal is famous for displaying very large binary digits in very small number of characters for example showing uh like let's say 2A in B in in a hex can be lots of digits in binary so depending on what you're looking at whether it's an IP address which would be in a decimal notation depending on a Mac address an IP address is your logical address right your Mac address would be your Hardware address that would be in a hexad decimal
we're just looking at just the computer codes what the computer read that would be in binary so these are going to be your three main uh notational systems that you're going to see in all the world of it so once again decimal 0 to9 it's a base what 10 binary it's a one or zero it's a base two and hexad decimal is a base 16 it's the digits of 0 to 9 a to F and hexad decimal is represented you know what we didn't look at the examples on it right forgot that one uh where
is my trusty slide here so things like 226 2A 49f BB AF uh 3 any kind combinations of this that you can come up with so these are going to be your examples out there of the different types of numbering system using technology in this video I'm going to be talking about data representation now when you have a keyboard as I have here on my desktop when you have a keyboard on your desktop and you press a key uh on this how does the computer interpret this well the computer doesn't read letters like we do
it doesn't read K and L and O and and Open brackets closed brackets open parentheses closed parentheses CD at sign and so it just doesn't read any of that the computer wants to know hey what number is that remember computer reads data in binary a computer the processor processes data in binary and again I'm going to talk more about this want to get into the hardware section of this class so how does the computer actually see these numbers well well these numbers these letters numbers and all the symbols on your keyboard is encoded and it's
then fed through the computer in an encoding standard or or what's called a code standard or a standard code and the way that we're going to the way we're going to talk about this is basically two of them there's something called ask key and unicode so let's get into this one of the most famous uh coding standard for encoding things like your letters on your keyboard is going to be ask key now ask key stands for the American Standard code for information exchange it basically supports 128 characters it's seven bits in its default nature but
it could go up to 8 Bits and support up to 256 characters there is a link there that I'm going to show you in a minute I have that link open to show you an Ask key connection table so or I should say translation table so anytime you press a letter on your keyboard ask key will take what you typed in let's say you put the emper sign let's say you put the dollar sign the number five or every time you press that what it's going to do is that it's going to take that and
turn it into a number because it knows that this you know what this emper sign is this number the letter a is this number and turns it into a binary and boom the computer reads it because remember a computer only reads binary now ask key only supports up to 128 of these characters something even bigger is called Unicode now Unicode includes ask key plus a whole lot more in the English language and we use this keyboard that most of us use but other languages such as Arabic Greek more mathematical symbols that's not on this keyboard
is stored in Unicode now Unicode supports very large amounts of digits and can support everything in almost every language that is out there now to make this presentation a little bit easier what I'm going to do is I want to show you guys the ask key table and this is going to be the link you just saw uh on there so here's an Ask key table so this is the ask key translation table so I'm going to show you what I mean now I got this right off Wikipedia so look at this if I type
the on the keyboard if I type the number zero that's represented as the number 48 eight which would then be turned into a binary and fed through the computer so every time you press zero on your you put zero on your keyboard the computer reads it as the number the decimal 48 and reads it as a binary of 48 if you press the equal sign on your keyboard that's the number 61 in decimal if you press an uppercase a it's 65 if you press all lowercase a it's 97 and so on you could literally see
every single uh key on the keyboard is listed here every single symbol we have you can see all these different from the space bar all the way to the shift backspace and so on so lots of different things that are here now for your exam when it comes to knowing these coding you know it's good to know for your exam in real life if you're studying like computer programming in real life you know this is good to know this is good to know uh when you are programming different types of applications or looking for translation
other than that just know the definitions of what they are for your test in this video I'm going to be covering some more codes that you should be familiar with for your exam now you don't need to know how to run codes for your exam or type codes which you should be able to understand it like I said before and one of them is called a Boolean expression now Boolean expressions in coding standards is basically an expression that outputs basically a yes or a no a true or false or one and zero bullan expressions in
the world of programming is basically outputs one of two possible options one or zero yes or no on or off true or false and anything else that can be put out as either one of two outputs so for example let's say there is an application that when you put in your weight and it tells you whether you're overweight or not so I'm 6 feet 220 am I overweight the application would say yes if I put under two if I put under let's say 190 it says no that's all it does yes or no that would
be a bullan expression if there was a a check box to say does this function work yes or no will you execute the function did it work yes okay did it work no that would also be another example of bullan now actually I'm going to take this a step further and I'm going to show you a bullan expression in Java this might Scar the hell out of you and basically what I just told you there is all you need to know for your exam but I just want to show you what they look like when
you start writing codes now you don't need to know this part for your exam if you want to shut off the video right now you're okay to do that but let me just show it to you uh so I'm going to go to Google and I'm going to type bullan example in Java and one of them I found it's called Java bullion at the W3 schools now I'm going to read the code for you and I found one here that's pretty Prett easy and I want to show you because this one includes the integer so
I'm going to go here I'm going say try for yourself and I want I want you to I want you to see this because you're going to have to know how to read Expressions later in the class they're saying that an integer X integer X is a value of 10 let's make this bigger integer Y is a value of none the system should print out it should print basically what happens when X is is X greater than y it returns true that's what it should do because 10 is greater than nine so if you run
this code here should basically return true it already ran it already but it's basically going to return true why because 10 is greater than n is this a true or false yes or no you see if I go in here and I change this to let's say this is eight and I run this well is 8 greater than 9 you'll see in a second here this always takes a while because the website just gets a lot of quotes false eight is not greater than nine but the number 15 that's greater than nine so that should
be true the point of this exercise is that you notice in the Boolean expression there can only be one or two outputs either it's true or it's going to be false that's all this thing does it's either on or it's off it's is the system on or is the system off that's all I need to need you to know for your exam you don't need to go and type Java codes in here although you need to not how to read some simple scripting coming up later in the class and if you enjoyed this one keep
going I'll see you next video in this video I'm going to be covering some basic terminology with you when it comes to using a computer so the four terms that we're going to be covering is input processing output and storage know the definitions for your exam let's get into it so when you give data when you give data to a computer that is called input input is when you sit on a keyboard and you type stuff in more than likely it can also be importing documents or importing data from another system such as a company
you upgrad in a database to a brand new one so it would import data from the old database to the new one so it's when you give or input data into a system what does a computer do with the data well it has to process the data into a format that it can understand and then it will store that data and output that data so it inputs it it processes it and it outputs it and then it stores it so the way this works is let's say you have a document you open up a document
like I'm about to do right now you open up a document so let's open up notepad we give it some input so this is my text and what I'm going to do now is that I am going to Output it now before it can output it it had to process my inputs to know the letters I'm typing remember those ask key things we covered earlier it processed the keyboard uh um keys that I used and it outputed the text on the screen now I'm going to Output it into a physical paper that's why I have
this printer here that's not installed so if I did have my HP Laser Jet installed I would click on my printer I would say print now I'm pretty sure you guys have all printed something before so that would be more of like a physical output if not the output is just displaying on on the screen when I'm done I want to store this data so I would go to file save as and let's say I store it on my desktop is just the word doc okay so by doing that it should appear on my desktop
right here so with that in mind now I'm storing the data on the hard drive so just to do a quick recap app we have when you type data into a computer it's called input in when the computer gets it it processes the data then it outputs it you can output it to a screen can output it to a printer that I have here and then you save it into the computer's memory such as its hard drive if you stor hard drive is going to be more of a permanent storage so you can access the
data later on the most valuable resource that we have on the planet today is time what what do thing I was going to say uh because it is something that is not infinite for our lives anyhow but the second most valuable resource on the planet it's not gold it's not money or currency it is known as data data is the most valuable human created commodity that exists in today's world a company is worth what its data is work a company makes decisions based on its data and that's what I want to talk about in this
video and coming up in the next video of how to secure it so one of the things we want to understand is that data and information are assets to a business and information like what well for example let's say you go to Amazon and you purchase something your name your address your ability to be contacted and sold to your contact information what is known as your pii your privately identifiable info is an asset to Amazon because they can potentially sell something to you the analytics or the data that's being analyzed by Amazon of how you
purchase and what to be sold to you is also an asset to Amazon Amazon values this data a list of customers and their privately uh contact info like emails and phone number is an asset that can be sold and Company's value it the secret information of how a company builds its particular products or redesign a product is an asset and it has a big value to them imagine if all the secret codes got out behind how Windows works like the source code to Windows that would destroyed all pretty much all of Microsoft so data and
information are assets companies invest tons and tons billions of dollars every year spent by Major businesses in order to secure data from being breach I'm pretty sure you've heard on the news about data breaches I'm pretty sure you've heard oh this company was hacked and the data of all the employees were so were stolen their names their social security numbers their credit card data this is going to be massive data breaches that cause companies millions of dollars that they lose you may have heard of something called ransomware if you ever heard of that before that's
when hackers come in and lock up or steal the data and then hold the company rents and to give it back to them or not to release it to the public they end up spending millions of dollars on on paying hackers um one of the things that I want to talk about in this one when you're thinking of just data there is something we call digital products what are digital products well digital products are basically not tangible not like a physical product like this phone or this cup that can be sold that reminds when you
take a drink coffee the essence of life um digital products are basically things that you purchase that is stored in a digital format like what well if you download an ebook that's a digital product music if you're listening to Spotify internet radio internet television these are all considered different forms of digital product now anything that anything that you go out and you purchase on the internet that's sent to you in a digital ones and zeros or buy inary format is considered some form of digital product and companies sell that in fact here at Tia we
make quite a lot of money from our digital products this is going to be all the digital courses that we sell on platforms such as Udi or selling it through our own websites it's just an e-learning course that you watch so it's a digital product the other term I want you to know for your exam is what's called datadriven business decisions what this is is that it using facts metrics and data to guide strategic decisions that would align with your goals objectives and initiatives so what do I mean by that let's talk about this a
little bit in a business decisions has to be made when do we redesign a product do we make a brand new product do we redesign the current product is there our marketing strategies working uh should we increase marketing budget should we low a marketing budget should we hire more people should we fire more people anytime of business makes decision are they making an educated decision based on good data for example if they released a product into the market space and it's it used to sell very well and now it's slowed down why did it slow
down was it is it because customers don't like it anymore it's starting to malfunction is it because there's a new competitor in space and it's taking away your sales what's causing people not to purchase the product that's a decision that has to be made what are we going to do are we going to redesign the product and fix the problems that we have or are we going to make a brand new product to compete with a competitor but before we make this decision we got to know what the hell is happening is it the is
it the product is bad is it new competitor well we have to grab data we have to go out and we have to speak to the customers and obtain the data from the customers we have to do research and obtain data on new competitors in in the market space this is called Data driven business decisions it's going to be using all types of facts that are out there or metrics such as measuring customer satisfaction and then make a business decision now the other part here we want to look at is data capture How Does It
capture the data well if it wants to do it for the customers it'll probably call and talk to them or maybe send them a survey it'll collect all of their information it'll correlate this data into some kind of giant database systems and then it will produce a report and the report will say oh customers are dissatisfied or the customers that has it is satisfied but they're leaving to purchase a new product so that would be a Data Business decision now these things are used all over the place all right whether a business is determining how
to guide itself because of stock prices and looking at stock charts if you ever looked at those before that's using good data to make good business decisions in today's world of business guys data drives all business the data of our marketing campaign working the data of what's happening in the stock market we may have to release employees due to recessions the data of what's happening with major world pandemic is it getting worse is it getting better always capturing data and it's from that data we're going to make decisions uh in our business of what to
do next when a company creates certain things whether it's creating a brand new invention creating a new logo for itself or even if even writing manuals internally or writing a book the company has to be able to protect their quote unquote intellectual property intellectual property are things that are going to be owned by the businesses that they're probably going to be making money off of and they don't want me or you to steal it from them for example imagine the iPhone and the operating system that it is imagine some other person just steals it and
puts it on on their device now they're selling something exactly like an iPhone I don't think Apple would be too happy with that so we have to find a way to secure our stuff we should say and then if anybody ever tries to steal it from us or use it without our permission or not giving us quote unquote feedback or Kickback in other words we're not making money if they're using our products or our services our digital products we're going to sue the hell out of them and in this video I'm going to talk of
three things that organizations do trademark copy rights and patents let's get into it you notice I have a book on my desk because I'll get into that in a minute the first thing here we're going to talk about is going to be a trademark now trademark is going to be a way to register your basically sometimes company names logos uh like this company's name and logo is actually registered with the trademark office so if somebody comes out and uses Technical Institute of America and then utilizes our logo as you see there we can basically take
them to court is trying to impersonate us the ITF logo at the bottom is a trademark logo by CompTIA if I try to steal it and claim its minds or make something similar maybe I make another certification come to you can take me down so trademarks when you file a trademark application with the government and your trademark your name your slogan your logo what happens is anybody that UTI I izes that you can sue them you can say you better stop before I take a lot of money from you the next one I want to
show you is called a copyright so copyrights protect things such as original works such as art literature or other created works this is basically going to come out of somebody's mind this includes pictures music files and books this is where most people know them this is my study guide I am the bestselling PMP author currently in the world this book has sold hundreds of thousands of copies to students around the world you can actually find this book on Amazon if you go right now you type PMP you'll see this book is a top selling book
I don't want nobody stealing my book if somebody wants to steal my book and claim that they're me well I'm going to sue them to Kingdom Come how so well as you can imagine I went out and I copyrighted the book and I want to show you that copyright certificate what am I doing here I want to show you this copyright certificate this is a certificate of registration with the copyright office that I filed in 2021 and this is it says the title of work see PMP exam prep simplified it was completed in January 4
2021 and it is copyrighted to me Andrew now you know the year on board so I own the copyright to this book all right so people should if they write books if they create manuals if they have pictures should upload that to the copyright office it's really easy it's like 60 bucks to do this and basically you own the copyright everybody ever wants to take it you can sue them now the next thing here we're going to talk about is something we call a patn now what is a patent a patn protects inventions mostly processes
compositions of matter such as medicine can be patent most tech Technologies most uh medicines that you find most compounds of different types of blends of of different things whether it's making yogurt or it's making the next vaccine they all patents companies when they create new inventions of things that they're going to sell they're going to patent it now patents are valid for about 20 years I believe and then it goes into the public market so let's say I make a brand new invention all right let's say this was an invention that I created that writes
out of thin air like you can go like this and it'll write that's my invention I will own this invention for 20 years and anybody that ever tries to mimic it will have to pay me or I will sue the hell out of them after 20 years it goes into the public domain and then anyone could make the invention uh and you're going to see you're going to see that you see this a lot with drug makers when the drug first when a drug is made the company that made the drug owns the drug they
have 20 years to sell it as much as high as they want as big prices they want because after 20 years it goes to the public market and anybody could make the drug it becomes like then you have those generic brands making the exact same drugs copyrights are generally valid for the life of the author plus 80 years so valid for me it's 80 or 100 years it's valid for you don't need to know this part for your exam but I'm just going over that it's valid for how long I am alive plus I think
80 years trademarks are valid you have to renew your trademark about every 10 years You Ren them many times it's like so that's generally how they're valid okay make sure you're familiar with these terms because don't be surprised on the exam they give you some kind of scenario and they said oh what should the company do are they going to trademark copyright or patn that particular thing in this video I'm going to be talking about storage measurements now storage measurements is how we basically measure how we store data and this is really important for your
exam as you will get a question on it and the knowledge you're going to learn in this video is knowledge that you're going to be using throughout your entire it career now what this video is really about is like so when you pick up something that looks like this and it says one TB on it and you pick up this one here this one says 200 GB I know hard to see but we're going to take a look at these more in depth later and I pick up this one here and it's like oh this
one is 128g like what the hell does all that means is which one here you notice these two drives has the exact same basically physical Dimensions but this one is 1 TB and this one is 200 GB what does that mean how much is this bigger or is this bigger we'll find out in this video and that's what we're trying to take a look at so let's get into this I have a slide here of terms that will show up on your test number one is the storage units now I want to point out something
to you data in the world of it when you store data it's stored as bytes data is transferred in bits what is the difference between bits and B bytes because this is something you're going to hear quite a lot of so a bit is represented as basically a one or a zero a single character a single bit is either it's a one or a zero now that's important to know because a computer reads data as bits it transfers data as bits why because your processor is made up of something called transistors I'm going to get
into the hardware section we'll cover that and the reason that it reads on or zeros or bits is because the one tells the transistor to be on or the zero tells it to be off so computers reads bits but when we store data in a computer we store them as a bite and a bite is basically eight bits eight bits in every bite so if a bit is one or zero then a bite basically looks like this it's basically going to be eight of those bits any combination of them so look I have 1 2
3 4 5 6 6 7 8 eight bits is basically that's one bite so eight bits in a bite now I want to point out something to you this is important to know for the real life anytime you see data con data being listed or storage being listed notice the Big B and the little B on these drives they'll say hard to see this but it says one TB with a giant B Big B that's a bite this is one ter BTE but sometimes you see in data transfer and we'll see this in the next
video it'll say 200 mega bits per second notice that little be so if you're ever reading something and you notice it'll have the little B that's considered bits if it says the Big B it's bytes remember that for your exam the other thing here we want to know is the unit of storage what does it mean well when somebody says K it means kilobyte or kilobits K just means kilo just means a thousand of something notice this a big b so this is 1,000 bytes so 1 kilobyte is equal to 1,000 bytes one megabyte is
equal to 1,000 kilobytes so a megabyte is a th000 kilobyte 1,000 kilobytes is basically a million kilobytes one gigabyte is basically a th000 megabyte this is also known as a billion right because if you think about it a th000 million is a billion so a gigabyte if I have one gigabyte I'm basically saying I have one billion bytes a terabyte what it's bigger than a gig it's a th000 gigabytes so what comes after a billion well a trillion so this is going to be a terabytes a terabyte is 1,000 gigabytes and then pedabytes is really
big nothing much is going to be stored in this yet that's 1,000 terabytes also is one pyte I've never seen a hard drive that big okay uh so we want to know these conversions well and on your exam they may give you something that looks like this to trick you watch they may give you something that says oh this is 4 meab bytes how many bits is this well did you get it did you say 4 million bits nope because this is 4 million btes 4 million btes has to be Times by 8 to get
32 million not Big B but little B I was about to write that Big B there that's 32 so 4 megabytes is 32 million bits did did you understand that why because me is a million okay and it that's 4 million bytes and8 bits in a bite so 4 * 8 let's try one more let's say I give you you know we I don't want to give you too much of big numbers let's say six kiler bytes is how many bits well this is going to be 6,000 bytes * 8 is going to be 48,000
bits easy enough see that they might give you something like this on your exam make sure you know how to do the conversion now I want to switch this up and I want to show you you know when you're looking at this in real life uh when you look at especially like hard drive storage because we store data on hard drives when we store them on hard drives we're basically be using this btes thing and I want to show you when you looking at these things let's take a look at the overhead cam so I
have three things here I have this hard drive and I have this hard drive so this black one and a blue one I want you to take a look at this blue one now this might be a little difficult to see um I know it's a little difficult there to see but it's hard to it's really hard to see that but that's says 250 GB what does that mean well that means that it is 250 gigabytes right this one is very easy to see CU it just p right there on the drive one terabyte see
that Big B we know this is bite because that's a big b this is a memory stick and this one here has 128g so it's 128 gig they're not going to tell you it's bytes but this is basically bytes because it's data storage now I asked you guys a question earlier what has more storage the 256 GB or the 1 TB well this one the one TB has four times as much storage as this you need four of these blue drives to equal one of this black Drive why because this is 250 and this is
basically 1,000 this is 1,000 gigs this is only 250 gigs right because 1,000 gigs is one terabyte so that's where these becomes important so now when you're looking at hard drives in today's world one terabyte cheap one terabyte this is a old spinner type hard disc drives and we're going to talk about solid state and hard dis drives later but one tbte hard disc drive physical big dries not solid state is cheap 50 60 bucks maybe less I have I have one on my shelf for that's 8 terabytes so if you think about it 8
terabytes if this is four times as much as this imagine an 8 terab how many how much more bigger it is than this and this here was a drive from about 10 years ago this one is is from five six years ago and the 8 tab I just bought so we got some seriously large storage even this memory stick at 128 gigs it may sound like it's a lot uh 128 gigs but if you're moving like movie files big movie files like Blu-ray movie files can be up to like 50 gigs pictures uh 4K video
files can be very very large so this 128 is not that big anymore even a terabyte is starting to shrink as the media we consuming starts to especially when store in like 4K video very high definition video I should say okay please review this video again because you're going to need to know these conversions when taking your exam and when working in real life in this video I'm going to be talking about something called throughput Unit now what is that well throughput unit basically is how we measure the speed of data being transferred and I
got a little setup here I want to show you what I mean before I actually get into it let's go back to the overhead cam so I want you to take a look at this this is a sonic wall Sonic walls are basically these are going to be devices that basically brings internet to your to your business so this would be hooked up to the cable providers Network and from here you would connect a network cable you can see this being connected right here network cable this is a network cable pretty long one actually network
cable that is then plugged directly into this notebook's network Port now you could also connect it wirelessly because this is also a wireless device so I want you to keep this in mind so we got this cable that is connected to this Wireless uh router that I have here Al this is also firewall and this is going to give this notebook internet so this notebook has to talk to this device but how fast does the data coming out of this cable can get into to this sonic wall well I'll give you it's basically going to
be 1 gabit per second and we're going to see what that means in this video you know anytime you deal with technology I'm going to put this away here anytime you deal with technology especially when it comes to internet and Network Technology you're going to have to know what is called speed well what I mean by speed is data transfer transfer from one device to the other just like in that setup where we saw how fast would the notebook transfer data to the actual router all the settings can be how fast is The Notebook transfers
data to the actual server on your network so with this I have a slide here of some measurements and this is going to be very similar to what we did in storage units hopefully you watched it that video okay so throughputs basically how fast data travels if anytime you see something that says BPS it it's bit per second and we really don't have anything with bit per second I've never I've never seen something that slow before uh when I started in computer world we started at kbps kilobits per second this is 1,000 bits per second
that's being transferred now what does that mean well let's say you have a file that's 3,000 bits big if you have a file that's 3,000 bits and you're transfering at basically uh a th000 bits per second then this should take three seconds to do right a mega is going to be 1,000 of those kilobits this is just like before K kilo Meg million G Giga T Terra so Mbps is megabits per second gbps is gigabits per second and tbps terabits per second so for example a gigabit is going to be a billion bits per second
and M is going to be a million bits per second in today's world of transfer speeds on a cable transfer cable transfers can be anywhere from a slow as 100 Megs all the way up to what I've seeing 10 Terra 10 gigabits is some of the fastest interfaces I've seen on a wired interface when it comes to wireless you can go down all the as slow as 54 megabits on a old school wireless network to the newer wireless networks of a few gigabits per second so those are going to be considered pretty quick I've never
seen something Traverse a network at terabits per second even on fiber optic networ networks they're going to be a few hundred gigs so I want you guys to understand the storage speed all right uh or what we will call the uh throughput speed of a network because whether you're ordering internet connection whether you are connecting something to a network you're going to see something 1 gigabit connection 2 gabit connection 400 Meg connection you're going to have to see that in fact when you go out and you purchase internet like here I am at files I'm
went to Verizon and I said hey I want to purchase Verizon's files they're telling me that you know what if you the speed tiers they have is make this uh a little bit bigger the speed TI that they come in you can buy 100 100 so it's 100 up 100 down notice Mbps what does that mean meab bits notice it's not a bite if it was a bite it would be a big b not a little B per second so where this line traverses 1 million one zeros per second on this line decently fast internet
connection so at my house right now I'm using a 1 gigabit so I get 9 940 Megs down Mbps every second it actually is that fast it really is that fast so very very fast okay so I want you guys to make sure you understand this rewatch this video if needed uh we will be using those Hardware coming up a lot later as we get more into networking gear I'll see you next video in this video I want to talk about processing speeds how do we measure the speed of a computer basically and how fast
it can process something now before I actually get into that I want to show you a processor so you know what the hell I'm talking about here I have an older motherboard now whether it's an old motherboard it's a new motherboard they basically all look the same they may have different functions or one may be faster or slower than the others but they basically all have the same set of components and on this motherboard here I have a processor right here so I want to take this processor off and I want to show you what
exactly does a processor looks like so here I have a processor and I'm going to go through all of this setup and what processes are and how to remove them how to identify all these parts and another part of this course so let me just take this off here and we're going to talk more about this is an AMD processor I'm going to take this off and this is a processor okay this little device is what powers up the entire world when you think of um devices or what's important to this world here I is
it going to focus there you go uh is it you know when you think of what's important to this world what makes this world go around right now this device everything in your computer will go through this device and we're going to talk about more of what this does but in this video what I want to talk about is how do you rate the speed of this thing how do we know which one is faster so when you see multiple of these devices how do you know okay that one is better than this one and
that is measured in what's called Herz now Herz put this back here so we don't damage it as we will need this in other videos Herz is known as a frequency of electrical cycles per second so cycles per second so if you have a megahertz a megahertz is basically 1 million cycle per second of this processor a gahz is 1 billion cycle per second so basically a gigahertz is 1,000 mahz now in today's world in processing we basically measure them by gigahertz if you go back uh to the old days in the in the 1990s
like when I got my first computer was an old IBM machine in '96 97 something like that was 233 megahertz in today's world we don't have megahertz anymore we have gigahertz so like I Remember by the early 2000s I was up to a 1.1 one gigahertz Athlon processor so that was a th000 megahertz right that was four times faster than my own machine nowadays the processors are rated a GHz 2 GHz 3 GHz 3 and 1/2 GHz 3.7 GHz So when you buy a processor you're going to see that you're going to see let's go
to a website here my favorite Hardware website we're going to do Newegg so new egg is my favorite website when it comes to buyin Hardware so we're going to go to component and storage I'm going to go to CPU and you'll notice whether you're you're an AMD fan or you're an Intel fan these are going to be the two biggest providers of of processors out there uh if I scroll down and we start to zoom in and look at them you'll notice that this one this is an I9 very powerful very brand new processor but
you see it says 3.2 gahz this one is 3.7 GHz this is an i7 3.6 GHz you're probably wonder this one is 3.7 but this here is 3.2 well this has a lot of cores this is six cores this is 16 core we'll talk about cores coming up later but cores just mean that it stores many many of those gigahertz Cycles in there uh you notice this one here is a eight core all right uh this is a six core but notice the gigahertz once again 2.5 GHz so the Hertz matter so when you are
purchasing a processor you if you want the faster machine go with the higher Hertz we'll talk about ches later in the class but if you're comp appearing as a six core Pro two six core processors one is 3 GHz one is 3 and a half GHz 3 and half GHz is faster 3.5 is better than three okay that is how processors are rated in hertz remember in today's world it's gigahertz we don't really use megahertz anymore in the world of processing in this video I'm going to be going over the CompTIA troubleshooting methodology this is
a seriously Hot Topic for your exam expect two three questions on your exam about this and all you really have to do is memorize the eight steps that I'm going to go through and be able to apply them in certain scenario for example one of the steps is identify the problem the next one is research knowledge base the next one is establish the profit CA so the question might say oh the technician has researched the knowledge base what should the technician do next and the answer would be establish a theory of probable cause they're going
to use these exact words on your exam this topic is covered in A+ it's covered in network plus also and A+ the A+ exam actually has pretty much exact same questions so just study in here you're going to use it later and you're going to use it in real life when you're actually trying to solve a problem for a user let's get into it I'm going to go through all eight steps if you have the compy objectives you can follow along with me of course you'll have the slides too so the first step all right
so here's here's the scenario a user calls up and the user says Andrew there is no internet on my computer what can I do well let's see the first thing we're going to want to do is we're going to do what we're going to want to identify that problem we're going to want to gather as much information about this problem as possible all right and by doing that we may ask can you duplicate the product can you go to Yahoo maybe they can take out their phone and take a a picture of their their computer
and text it to you remember they can't send it because the computer is dead over over email but they can duplicate The Prompt so you could see okay this machine really has no internet can't even go to Yahoo question the user such as asking has anything changed on this machine did anybody install new software was any new hardware added to the machine identify the symptoms such as okay they can't get to a network drive they can't get to the internet or maybe they can get to the network drive but they can't get to the internet
all of these would matter approach multiple problems individually if the computer has multiple issues what if it has no internet but it has pop UPS it could be there it could be the cable is out and the Machine has a virus or it could be the virus disabling the internet approach each problem individually because you don't know if one is causing the other okay the first thing you want to do is identify that problem okay the computer has no internet the next thing you want to do is research your knowledgebase uh internet if probable if
acceptable so what what this means is the best knowledge base is Google if you ever have a problem with with your computer the best thing you can do is go to Google and put the error in there put computer has no internet internet not working map drive not functional if you ever get an error code on your machine what I do is I just Google the damn error code and somebody fixed it at some point and you'll get it from there A lot of times the manufacturer like Microsoft actually comes out with a fix and
they'll just post a fix for you and you can basically install it right there the next thing is establish the theory of probable cause so you go to the internet you see what people said about it you been through the Microsoft knowledge base you saw that okay these are ways to fix it now you come up problem cause okay what's causing it okay maybe it could be the cable is bad it could be the internet is actually down in the office it could be the local switch is not working it could be the router has
some kind of block on it could be the computer has some kind of virus you have to question in the obvious all right consider multiple approaches maybe we'll check the cable maybe we'll check the switch we'll check the router divide them into problems and then go through them one by one or divide and conquer so establish the problem cause maybe we'll say maybe the problem cause here is that the cable may not be working so that's my theory now we got to test the theory if you if you're doing your theory you determine okay everything
on the internet works everybody has internet so it's not the internet connection everybody has connection to the server so it's not it's not a network connection it's something on the machine something local to the machine maybe the person kicked the cable out right so test the theory once the theory is confirmed you confirm the root cause maybe the cable is out uh determine the next step to resolve the problem so test the theory unplug the cable all right plug in a brand new cable and see okay is is this the way to fix it if
the theory is not confirmed establish a near Theory so maybe you change the cable in the internet still there maybe it's malware that step five establish a planet resolved or identify its potential effects so if you change the cable and it works then you're good then you know what to do your plan of action is to permanently throw that old cable out maybe something's wrong ahead maybe somebody broke the cable somewhere maybe a wrath bit it in the wall something happens I've seen that before throw the cable out replace the cable so this is what
you're doing your plan is to replace the cable throughout the old one you're going to implement the solution of replacing in the cable now sometimes you may have to escalate it sometimes not all the time you may have to escalate your problem upwards the ladder sometimes it may be what if the problem was with the switch or the router well if you're a level one technician you don't have access to fix that you may need to call the level three help test or systems admin or network administrators to fix your routers and your and your
servers and so on so you may have to escalate it once you change the cas table you're going to verify the full system functionality and Implement any preventive measures so plug in K make sure it works and then you got to say well maybe he kicked the cable out preventive measure would be to tuck the cable in the back of the machine hide the cable so the cable is not on the floor so the user can kick it out maybe the user kicked the cable so many times it broke part of the head off so
put in preventive measures so if you believe there was a user that broke the cable and put in ways that the user doesn't do that you're going to want to document you're finding your lessons learn and put it a lot of organizations have knowledge bases where you would uh where you're actually going to uh put it into a knowledge what's called Knowledge Management systems or kmss so they have these internal databases that you store oh I had this problem this is how I fixed it why do we do this well because when people later on
other technicians gets the same problem someone else going through your knowledge base is going to be able to fix it so that's why you have document you're find it's the last thing you do on your exam this is one of the most common mistakes is people select this as what to do next document your find okay identify the problem what do you do next document your find it wrong document your finding lesson learn comes all the way at the end after the problem has been resolved you have shown the user that the problem is resolved
the user is happy you're walking away to the ticket's basically closed is is about to be closed you're going to go in there you're going to document it put it into the company's knowledge base okay let's do a quick review before I leave number one identify the problem you're going to question the user you're going to find out if anything change number two you're going to do some research on a problem you just discovered look at the internet research knowledge bases maybe you have internal knowledge bases maybe you look at the manufacturer's website tell yourself
establish a theory of CA yourself this is this is what may be causing it okay if I unplug cables this is what happens if there's a virus this may be what you know this could cause it then test the theory all right you can unplug a cable from another machine to see if that really does something similar all right you can pull in replace the cable tell the user jiggle the cable a little bit so test the the is it actually that if you realize okay that's probably going to be it then establish a plan
of action to resolve the problem Implement fix and putting in the cable Implement Your solution number six number seven verify full system functionality make sure everything works make sure all the internet works make sure the map Drive works and number eight document your finding your lessons learn okay please review this video memorize it's not going to be complex if you memorize the the eight steps here you're golden you're going to be able to answer any of these questions because it's not that difficult um to answer these questions and we've all dealt with problems in our
computers and we should be following these steps and solving problems in this video I'm going to be talking about wired and wireless networking let's get started so why do you want to set up a network right what exactly is a network but by definition an network is basically taking two computers or more and allowing them to share quote unquote resources what is resources well resources defined as things that they share such as data or devices like you can share a printer or you could share those pictures between one users and another you could share text
documents or Word files or PowerPoint information when you share information across the Internet it's a giant Network when you share pictures in your house with your with your friends and your family it's a network so we set up Network to share resources so network is a really simple thing here I have a laptop if I take my other laptop and I take a cable okay and I connect one end of this cable to this switch now this is more than a switch by the way I know it's it's a firewall it's a router it's a
switch but it is a switch you connect this switch and then you connect it to the back of this machine then you take this K take another one like this connect it to another port and then you connect it to the back of this laptop or the side of it I should say now you would have these two laptops connected through this switch and through this switch we're going to allow these this laptop to communicate to this laptop using a wire that would be considered a wired Network now the the other way to do it
instead of having all these crazy wires is to connect them using Wireless networking so this is a wireless access point also but it does allow you to connect a wire tune so if I go into this access point and I configure it and then I join I configure this laptop to join the access point configure this laptop to join the access point this would be considered Wireless communication a wireless network this is probably what you have at your house now that you're listening to me but if you're a gamer and you're playing games right now
you need that low ping rate we should say make sure it's wired I always in anything that's Mission critical I always use wire Network and in my house most of it is wired I'm not a fan of Wireless cuz it's not very predict able but we'll cover that in in another video in this course we're going to talk about how to set up wireless network so that's what we need to know we need to today we need to talk of wired and versus Wireless networking now I don't want to take a look at the slide
here so you'll notice that ctia gave us some exam objectives we're going to talk about wi networking right now old telephone connectors and ethernet connectors we need to know what they are we're going to talk about wireless network and which I covered a little bit and then we're going to talk about Bluetooth and nfc's and see what those are let's get back to this so with the wired Network in most 99% of the connections within your wired Network whether it's at home whether it's uh at work if something is connected into the W that's how
you get network connection such as Internet or access to those servers you're basically going to be using ethernet so ethernet is the standard of the networking I'm not going to get into all of that because not for your exam but the network plus will cover that so I'm going to go back here to my overhead cam and I do want to show you guys um let's get this out of the way here I do want to show you guys the actual wired connection I did drop that I did drop that cable let's pick it up
all right so let's take a look at this so when you want to connect device wired Network and you're basically going to use a cable like this this is called an ethernet cable and ethernet cabl comes with a a head or a connector we call an RJ45 an RJ45 is a standard connector you're going to use this in almost all ethernet cables this is going to be for you Geeks out there cat 5 cat 6 and so on WE you utilize this connector uh this connector is what will allow me to plug in to the
switch here you can hear it click there and then be able to plug it in to my laptop that still has a Nick card now most laptops don't anymore they actually don't come with Nick card is an older laptop and plug it in here so this one would be wirly connected a lot of laptops doesn't come wired anymore a lot of them are just pure Wireless now so like this laptop here this black one it only supports Wireless okay the other thing I wanted to mention here is an older telephone networking so here I have
an old telephone telephone a VTEC telephone that I found lying around and connected to the telephone is a telephone cable the connector on the telephone cable this is knowing as an rj1 and an rj11 versus where is that an RJ45 so an rj11 is actually the connector is actually the same height people think it's why it's not tall or no it's it's pretty much the same height where it's different is the width you can see I how much you can see that but it the RJ45 is a much wider it has more peers in here
than the rg11 so the rg45 is just supports more cables this one supports less cables inside of what we call peers inside of here are copper cables by the way so what I want you to know for your exam is is rj11 telephone cables the it's a it's physically smaller than the RJ45 which is using Data Network and this is mostly used in Old analog phone network and they probably saying do we still need to know this for exam the answer is yes a lot of people what people don't understand is this is still used
in fact this is still covered on your current newest new A+ exam because you see in rural areas where they don't have high-speed cable internet in which case they ran cable lines uh from the cable providers to the houses there they still have telephone cables this is telephone cable is widely used and in order to get highspeed internet across telephone networking you use what's called a digital subscriber line or DSL Internet DSL lines DSL when you have a DSL modem you're still going to need one of these cables to connect that so people a lot
of people in the United States even in 2022 still uses DSL and they still use an rg11 cable that's why it's still mentioned on your exam okay so now uh let's get this all off the desk here no the um rg11 versus RJ45 now the next thing we're talking about is going to be Wireless so Wireless networking I forgot to my out here you're connected right now to a wireless network maybe you're watching over your wireless network at home home okay this is known as an 802.11 wireless network computer network it's you're connected to a
device something looking like this it probably have a bunch of antennas called an access point and what it does is that it allows you to connect to this and share data across this device so the internet is coming in here and all the wireless devices are connected you can all share data going through this device now later on in the class I'm going to go through a whole section on how to configure Wireless networking the other two I want to mention is Bluetooth okay Bluetooth Bluetooth is incredibly famous for things such as Bluetooth headsets everybody
has one of those right you have a Bluetooth headset like an apple airpod or something like that uh but Bluetooth is not just for music or connecting a music like a like a headset to your phone Bluetooth is also going to be used for mouses so here I have a Bluetooth mouse and you can see this is my my good old fashioned blue you can literally see it's blinking blue there um you'll know Bluetooth devices Bluetooth device has a symbol it looks like a a line with couple lines or X's going through it really hard
to see that uh but you can see it somewhere there see see right there so you can know a Bluetooth device now Bluetooth is very good to use it has a has a good distance it's about 30 feet distance going around the device so you know this mouse could work from across the room and still connect to this computer so Bluetooth mouse uh but remember Bluetooth again headsets mouses keyboards are used are done using Bluetooth you can get into your car take your phone paer your phone to transfer music from your phone to your car
infotainment system utilizing Bluetooths use use their popular too now the other one I want to mention is something that maybe you haven't heard of I'm pretty sure you guys have all peered your Bluetooth devices together the other one I want to mention is something called NFC or nfield communication so nfield communication is what you use in mobile payments nfield communication is is a type of a a small nfield actually means that it should there a small distance so let's say this is a reader this is the device it can't be more than 4 in it's
about 10 cm so it's about this much what that means is that the two device has to be really close to each other for them to communicate versus Bluetooth the device can be 30 ft away so let's say this mouse is controlling data on this phone it could be upwards at 30 ft away before before we lose connectivity versus nearfield communication the device has to be very close nearfield communication where do we use this we use this in in in pay in with credit cards on your phone I'll show you guys something I'm going to
log into my Android phone here okay and I'm going to look at some of the settings uh uh on it so where is my overhead C so look at my uh Android phone here uh and in here I'm going to swipe it and you notice I have this icon right here uh that says NFC see that NFC or near field communication what exactly is that yes I know I know it's 11:15 in the night I record videos very late uh NFC nfield Communications um so when this is turned on what I can do is I
can now go and set up like Google's digital wallet so if you have Apple pay you would set it up on your Apple phone you enable the NFC so when I go to a restaurant uh a grocery store somewhere 711 to get some coffee um and I want to pay I just enable my NFC boom I turn it on because I have the credit card setup and the the the actual reader itself the credit card reader where you put your credit I'm just going to tap it with my phone the phone has to be remember
N Field it has to be really close so it has to be let's say this is the reader has to go very close to the device it then transfers the credit card information to the device and boom I pay so that's what NFC is the thing with Bluetooth and NFC is that they're NFC is not widely used but Bluetooth is and remember for your exam that when you're using Bluetooth you have to pair the device generally that means you have to go through a searching process search for the device and then when you find it
you pair it and you generally have to put in a code or pin or confirm that okay so for this one I know it's kind of a long video Wide networking it's going to be Ethernet or some kind of telephone system with ethernet we're going to use this rj45s with the old telephone system we're going to use rj11 wireless networking we're going to cover 802.11 wireless computer networking in another video but don't forget Bluetooth gives you a good range of distance between devices and it's used in a variety of devices NFC is mostly just used
for now most of the time in just payment systems or paying with a credit card in device has to be very close so make sure you know these topics because you're going to be seeing some questions on your exam about this in this video we're going to be talking about peripheral devices and basically how we connect them this whole video is about what can we use to connect different devices to our computers for example what can I use to connect this mouse that I have that's really tied down to the desk there to my actual
computer I have a drawing tablet what can I what can I use to connect my tablet to my computer my keyboard my camera my my webcam my microphone what port can we use now if you're saying USB you're absolutely right because that is the quotequote universal serial bus so CompTIA does give us some things that I want to mention in this video on this the first thing up is USB we're going to cover USB in depth the good thing is for this exam you don't need to go into the different types of USB like USB
1.0 2.0 3.0 and all the different micro mini uh USBC connectors and so on you don't need to know that for this exam what you do need to know is what's USB user used to connect a variety of different devices to your actual computer and there's others you know most people know USB but there's others there's firewire there's Thunderbolt we talked with Bluetooth already and then we'll talk about something called RF radio frequency connectors let's get into it as I have a bunch of equipment here that I want to show you what these connectors are
now the first one is going to be USB the universal serial bus this is a basically a connector on your computer that you're basically going to plug almost everything into in fact when you don't have enough of them ports on your computer you buy a hub USB buses can generally support about 127 devices if you put USB hubs which is you connect a hub to it and then you get more ports now USB let's take a look so on the overhead cam here I have my laptop and your laptop and of course your desktop back
of your desktop will come with USB ports so you can see I have one right here this is a normal USB uh Port you also have what's called this is also a USB port this is a what is known as a USBC Port so they do come in different sizes and form factors we should say but for your exam just know you can plug a lot of things in here whatever you want to plug in a mouse you want to plug in a keyboard board you want to plug in a webcam all of that will
be plugged in to your USB almost everything that's purchased is connected to USBS the other one I want to mention is something called a tunder bolt Port now tunder bolt ports basically compet to USB you find them a lot on Mac not so much so on Windows although some windows has this laptop I'm using actually has oops overhead cam actually has a tunder bolt Port right here you see this port here that's a tunder bolt Port now you're probably saying Andrew how the hell did you know that was a tunder bolt Port really if you
look right there you can see the tunder bolt symbol this is a tunder bolt 3 Port it shares the same form factor as this USBC if you're looking at this and you're looking at this you're like hey aren't those the same yeah they say it's is sure the same port but this is a Tunda bolt USB 3.0 Port uh other Tunda bolt ports that you have you find them a lot on Apple machines so I actually got a back here see some for those of you guys that are going to say I'm an apple hater
that is not true I have a whole Mac right here this is an iMac that we're going to be taking a look at a little bit in well mostly in the A+ class we use I showed them how to configure Mac and this so I have it but on the back of this very heavy device actually it's not that heavy is that I'm old and my shoulders are bad on the back of this device we have a bunch of ports here uh and I want to show you the Thunderbolt port on this one let's go
back to the overhead cam here and uh you'll notice that in the back of this one we have a bunch of USB ports quite a lot this is the symbol for the USB port uh you also have notice these bolts of lightning these are going to be the original um uh tund ports because they share the same form fact was known as the old style display ports that Mac used to have and you have an old you can put ethernet cable in here so you can wire connection this machine all right that was pretty heavy
let's put that back so tunder Bol ports you use to connect I saw I've seen a lot of people use them to connect external hard drives something we look at in another video but that's where people a lot of people use them to connect to the other topic on this list was Bluetooth which we covered already in the previous video the other one I didn't cover that's a wireless connector is called RF a radio frequency now you saying cuz people use that you use it all the time all the time time you're using RF connectors
you probably just never thought about it but here I have a cable box a Fios cable box Verizon right here FiOS actually it says right there all right so you probably say RF yes you use RF for this because in order to control this device you need a remote control right remote control this this cable box is being controlled with this remote control utilizing RF right here so let's go we go back here you see this right here this is the RF connector and when the remote wants to talk to the cable box the remote
also has the RF connector now RF connector needs a line of sight so if this is pointed this way and the control is pointed this way it's not going to talk the control has to be pointed towards the device like this for them to work now they can have a good set of distance between them but the devices has to be pointed to each other for it to work uh that's different than how you would have Bluetooth when you have Bluetooth you don't need that direct line of sight but if you use an RF connector
you're going to need that direct line of sight the one thing here I didn't show you because I don't have a device for it is something called firewire firewire is an much older standard I haven't seen firewire in a minute okay like I haven't seen it in a while so in order to show you the connector firewire I went out and I got Des stop I went out and I got uh Wikipedia article on it so just Google firewire see it's known as the i e 1394 firewire and firewire this is a FireWire 800 this
is becomes one of the last development of firewire this is what the cable looks like so the connector is what this would plug into and uh on here we'll see a picture of what fire wire looks like so this is fire wire on a computer that's what that cable would plug into firewire was mostly used especially a lot for external hard drives if you have a an external hard drive you wanted to connect to the machine and transfer data really fast firewire is one of your better options firewire was when it came out was faster
than USB so if you had a USB drive it would take forever to transfer data but if you have a fire wire would transfer 800 Megs or 400 Megs very very fast versus USB was when it first came out was 12 Megs really slow but it USB got faster and faster you got 3 gigabyte 3 GB USB 3.0 now so it's very very fast and as USB got faster fire wire basically died I haven't seen firewire in forever now Thunderbolt is getting faster competes with USB you'll see some of your Apple devices has it you
notice my this laptop is about a year old this has a Tunda bolt port and it has USB ports on it uh RF is Bluetooth we talked about it's going to be used for things like your mouses your keyboard your headset and then RF is basically used on remote control back in the days they used to have RF on computers to transfer data between mobile devices and computers I haven't seen that in about 15 years but that but it was there well I did have a laptop with it all right so make sure you know
how these peripheral devices are connecting to computers in this video I'm going to be going over graphic device interfaces in this video we're going to talk about the different interfaces that we're going to be using to connect our computers basically to our monitors or maybe connect your computer to your TV there's a variety of different interfaces we can use to accomplish this and we need to know those for our exam so the exam says that we need to know what our VGA or at least be able to identify them that's called video graphics array HDMI
High defition Media interface DVI or digital visual ual interface and display port and mini display port or basically just say display port so let's get into it so I'm going to actually show you some of these interfaces that are out there so we have them I basically have them all on here on my desk and around me got a whole bunch of Hardware around me this section of the course drives me crazy as I have to go through all the hardware with you okay so I got a monitor big monitor right here all right I
got a big monitor right here that I want to tell you guys how are we going to connect this monitor to this desktop now this monitor in the back of it has a port a blue Port this port is known as a VGA what I'm going to do is I'm going to get a very believe me or not guys this is the shortest one I have I have the entire house here a very long VGA cable I will connect it to the port uh on the back of this uh computer monitor and then I'm going
to connect it to the back of this desktop so what I want to do is I want to get on the overhead cam here and I really really want to show you guys the back of the machines so let's go and this monitor is giant it's the smallest monitor I have that's available in the house if we take a look at the overhead cam as you can see you're just looking at a computer there but let's take a look at this we got a big oldfashioned desktop and in the desktop you have a variety of
interfaces that you can use to connect monitors to and one of them is going to be right here this is a VGA video graphics array so you can connect this to the monitor you take that cable I just showed you you connect it right here and then you plug that in to the back of the monitor let's see if I can get this over here right there see that DV it says d sub you would connect that right to the back of this Monitor and you are doing super and you are okay with that so
that would be what we consider a VGA so VGA were really popular back in since I started it I've been connecting with VGA VGA supports good graphics it's about up to 1080p on your display it's not going to give you a high or the best quality display but it's still pretty decent uh and it's still used quite a lot in a lot of connectors the other one I want to mention in here guys is going to be HDMI now let's talk about HDMI cuz it deserves to be talked about HDMI is the most famous connector
you're going to have on a back of a computer to connect to a monitor HDMI it's very unique out of all of all of the uh where's my slide of all of the connectors that is listed here vgh HDMI DVI display port it's the only one that can pass sound digital sound so back in the days we used to connect computers with especially DVI was very popular and and display port was getting popular and TVs mostly used HDMI but as as time went on and on and on uh HDMI became more and more popular because
it was a you could pass sign you don't need a separate connector to connect your speakers and it went from the TV world into the IT world and nowadays basically it's one of the only ports we use nowadays when you're connecting something to a computer to a monitor you're probably only going to use um HDMI or a display port very rarely you're going to still use that VGA although a lot of monitors and a lot still comes and a lot this is this is a brand new monitor by the way it still comes oops am
I showing you the right one it still comes with that VGA port it's a brand new monitor that we have okay so I want to show you guys HDMI now HDMI let's go back to the overhead cam here so HDMI does this computer have an HDMI it better have an HDMI uh so here is the HDMI and you can see it right around somewhere around here we go that is the HDMI port right there all right so the HDMI port on that would plug in using what's called an HDMI cable an HDMI cable you can
see the head of it let's see the screen this is what an HDMI cable looks like basically with the head looks like on an HDMI cable and it would just plug in you plug one end of this to your monitor one end of this to to your desktop or even your laptop has these types of connectors on them so HDMI remers you're going to use this a lot that allows you to pass sound different than the rest of them the next one we're going to talk about guys is going to be what is known as
a DVI DVI ports are not very popular anymore a lot of video cards that are coming out a lot of computers don't have dvis anymore back in the days it wasn't uncommon to have just VGA and the DVI but nowadays you don't really find DVI almost all computers are made with HDMI and maybe a VGA you get so let's take a look at a DVI connector so a DVI don't need that DVI connector in the back of this uh very big desktop is the white one okay so that's going to be uh that one right
there all right so you can see that the the DVI port is bigger than your VGA port much bigger than your HDMI port and it does allow for a digital video versus VGA were more of your analog video signals so this was a DVI port all right now in today's world guys you're going to find a lot of machines with display ports all right a lot of video cards a lot of computers coming out the factories if you have gaming cards because display port is going to give you a can give you a very high
resolution as high as you're going to get with an HDMI and this monitor does not support display port your higher end or bigger larger screen monitor as well so I'm going to put this on the ground here uh we don't need this desktop does not have a display port but what I want to show you in this video is going to be think I forgot to switch myself there all right I'm not redoing this video okay don't ask cuz dealing with these Hardware is raing me crazy uh to show you a display port hopefully you
guys were listening to show you a display port I have a video card and on this video card in this anti-static bag lies a video card now in another video we're going to be doing computer hardware but in here is my video card this is actually one of my older video cards I used to have on my computer this is a video card and this is what you're in in your desktop you give a big desktop this is what you're going to plug in this is what you're going to see on this outside of the
machine this is what you're going to plug your monitor into and this particular one had support quite a lot in this particular one it had supported four different monitors and of course if you're this was used to play video games so it was really good graphics so you had two DVI ports uh um this is DVI this is a DVI come on focus camera Focus I'm never going to get this to focus because that's my luck ah here you go so these were DVI ports that we had uh on here notice an HDMI but look
at this one it looks very similar to an HDMI except it's wider that's known as a display port now again I don't have the cable for it um this monitor is connected Ed I didn't want to disconnect it but display port is still pretty popular I do connect quite a lot of monitors on there not on comment today for your higher monitor to support just HDMI and display port and don't have any VGA on it okay so we're going to talk more about this device coming up a little bit later when we talk about video
cards and so on but when it comes to monitor connections there's quite a lot out there there's also another one called a mini display port which is basically a display port but the connector is just small smaller all right for your exam I want you guys to remember how do we connect to our computer you could use a VGA connector older style VGA connector and A+ we'll talk more about this we'll have to know the pins inside of them HDMI allows you to transfer to video and the sound DVI gives you good digital video display
port is very good it allows high resolution it's still being used popular today and so is a mini display port in this video we're going to be talking about a variety of different peripheral devices that you can connect to a laptop or a desktop and I got a bunch of them now some of them are pretty easy and common you're already familiar with like keyboard and mouse and some of them maybe you've never seen before let's get into it so the first thing I I have is a printer now printers you saw I had a
big laser printer on my desk at some point printers are generally going to be connected to a computer using a USB port back back in the days they used to have something called a parallel port that we used to connect printers but I haven't seen one of those in over 10 years but most of the time you get a printer you're going to plug it directly into the computer using a USB cable uh the other one are scanners now scanners a lot of devices nowadays comes with both uh all-in-one devices a scanner is where you
put the paper on it scans the document or the image and then you could see it in your computer or a picture scanners are also going to be plugged into a computer using uh USB keyboard and a mouse now keyboard and mouse is is unique because although we know them to be USB or you can use infrared or Bluetooth wireless keyboard and mouses back in the days they had they used to have an old connector called a PS2 PS2 connectors are still showing up on computers today and for that reason I have my the desktop
on the ground I want to show you a PS2 Port so let me grab it so I don't want to keep the computer on my desk because it just takes up whatever little space I have let's take a look at the uh overhead cam here and uh you'll notice that now if you see that Port that we have there you see that purple green Port I can't put my finger there cuz I'm holding it up that's a PS2 Port back in the days we used to connect keyboards and mouse to it you would have to
of them one purple and one green one for the keyboard and one for the mouse this one is telling you to dual Port it does keyboard and mouse if you notice it actually shows you a little picture of a keyboard and a mouse there so those are called PS2 ports okay the other things here what else do we have here uh cameras so a lot of times we connect cameras here I have a webcam to a computer and a webcam is basically connected like everything else remember it's called Universal for a reason because it connects
everything there a another USB port connects in to this webcam uh we have external hard drive so an external hard drive once again USB here is a Western Digital this one shows a lot it's like 10 terabytes or something uh Western Digital uh connects Western Digital external hard drive plug it in I get more storage on the computer maybe I could put videos music on it this one here USB also very highs speeed USB USB 3.0 but a very highp speed one by the way this is uh off topic this is garbage this is a
brand new drive that came out the box a few days ago and it's dead out the box Drive doesn't spin it it mounts but when you try to put anything it doesn't work you have to return it go figure Wern digital I thought it was better now the other thing here I have is going to be speakers and display display I covered already in the previous video when we talked about connecting HDMI DVI and so on the other one I have are speakers now speakers people know them as USB you could connect speakers through USB
but a lot of time we connect speakers using audio cable or speaker audio cable and I want to show you that as I have speakers here on the desk I have some brand new speakers I don't want to take out the packaging but you can see they're basically computer speakers and there's a wire that goes from this one to this one but in the back of this one is where you would connect to the computer and in here there is a jack and then it comes this cable this is a audio cable it's 3.5 mm
audio cable that I'm going to plug into the back of the speaker and I'm going to plug it directly into the desktop now the desktop of itself if you move over this the desktop of itself is going to have a connector let's get that desktop and I want to show you to this desktop has a lot of connectors on it but this particular desktop in the back of it has a lot of cables see this right here these all going to be speaker cabl this one has a surround sound system you could connect uh front
speakers back speakers but basically by using these cables basically the green one you'll be able to uh just get music right out of it especially these two speakers this one is a very specialized board it has a bunch of music connectors on it like microphone in you have the the your your normal music out you have another line in and so on and so on so you have a variety of different uh front Channel back Channel and so on on this particular motherboard let's put that down you know what happens when you get old your
shoulder gives out I have like pain in my shoulders all the time getting too old for that's why hard to pick those machines up that's why you young guys are around to do that for me all right so we have hopefully we cover everything here we have our printers scanners keyboard mouse camera external basically everything here is going to be connected with a USB except displays those are going to have their HDMI ports uh but speakers also can be connected with the audio cable I showed you uh printers used to be connected with parallel ports
long re Old Port Mouse and keyboards used to be connected with older PS2 ports okay know what these devices are for your exam and I'll see you next video in this video we're going to be talking about installing the peripheral devices that was covered in previous videos so when you get a device such as maybe you got a mouse or keyboard or speakers uh or or a webcam that you connect to your computer sometime it works and sometime it doesn't actually work and you're probably saying Andrew how is that possible well because it needs what's
called a driver so let's get into this so when you connect a computer when you connect a a device to a computer in today's world most of the time it will work all right most of the time it just starts working right out the box Windows or Mac it say setting up the device and boom it's ready to go and you're ready to use it like this webcam that I'm using I didn't do anything I just plugged it in and all the applications picked it up but some devices doesn't some devices is not quote unquote
Plug and Play So Plug and Play literally means what it says it is that you plug it in and you start playing with it you start using it some device requires a driver installation now realistically every single device that we plug into a computer a mouse a keyboard my tablet my phone every device that's connected to a computer requires a driver installation now plug-in play basically means that Windows found the driver for the device and installed it a driver is a piece of software that tells the computer how to use that Hardware correctly so if
you install a hardware and don't install the correct driver the hardware may never work correctly or never work at all for example if I take this tablet and I don't install the Cor currect drivers the tablet will never work it'll never I'll never be able to write on the screen with it uh if you install for example even when you put in any device that plugs into the motherboard if you put in a this big graphic card that I showed you I can't find right now but somewhere over there if I plug in that big
graphics card I still need to put a driver into it so the operating system knows how to handle that device so drivers are basically software that tells the computer how to utilize that Hardware correctly that's all it is uh and I want to show you that so let's go to the desktop uh where is it desktop desktop desktop where my desktop here we go so here I am at the desktop now where you can see your drivers is by right clicking on your start button and we're going to go to device manager this is a
Windows 10 Box by the way so here I am a device manager and these are all the drivers that are installed on the computer itself if I go here I can see the different classes of devices see if I go to Imaging device you can see I have this uh p992 Pro stream webcam so if this that's this webcam that I'm holding here now if I double click on it and I go to this tab that says see it says not streaming webcam notice a driver it tells me it's a Logitech device it's utilizing the
driver version that it downloaded from Logitech is this version now this is important because what happens is sometime Logitech May release a new driver software that basically tell Windows how to use this device more efficiently or adds more features to it and if you really want the new version you can just click update driver and it can search for it or if you downloaded it you can browse and find it uh but this is driver installation for this exam you really don't need to go in how install drivers just know that there is such a
thing and where do you get drivers all right that's a question where do I get drivers from drivers are generally gotten from the manufacturer's website and I'm going to show you that in this video how do we get a driver so let's say you have a device that you plugged in like let's say my tablet okay now the the the drivers already in there but we'll walk through the steps on how to get it um let's say you have a tablet like I have a waycom tablet all right so if I go to the overhead
cam and I look at it you can see it gives me the model number all right kind of hard to see that there what's the model number there we got CH H uh what is that cth-480 all right so it's a waycom tablet with that number so what I'm going to do here is I'm going to go and the best place to gather drivers is from the manufacturer's website you'll always get the latest driver so I'm going to go I'm just going to Google it I'm going to say waycom t drivers seems like a common
search I'm going to go in here okay it wants me to put this in it wants me to put in the uh just put the model number in there ct-480 we saw was the model number we are going to search for that cth all right OCD kicking in there no typed that wrong cth-480 yep we got the pen it says old one 123 is a pretty old tablet and notice it's driver driver for Mac driver for Windows so if I want the driver I would literally say download driver confirm the download and here's the driver
so notice the driver is just an executable file and to install it I will just click on it and it would start installing okay so here it is I would say accept and it's basically installing the driver for this little device that I have now I've already had the driver in here so I'm not sure if I can cancel this if not I'll unall it later so drivers when you're doing driver based installations okay uh you got to you should get the driver from the latest from latest manufacturer from from the manufacturer the latest version
sometimes when you purchase hardware and you try to install it on the machine it may say install correctly but it doesn't really work so well because it may be Windows may have an old driver for it and sometime Windows just doesn't have a driver at all you got to go do the step to make it work okay now other the ways to to install certain Hardware uh that's going to be utilizing what's called IP based peripherals or web based configuration steps IP based peripherals are going to be devices is that you got to connect through
an interface for example the other day I went I bought a door lock and the door lock is an IP base that connects to the wireless network and I can control the door locks I can actually take out my phone and unlock my door right now those are going to be called IP based peripher a lot of them are known as iot Internet of Things we'll talk about that in another section you would have to connect to the web interface and do a web configuration steps this happens especially when you're configuring things like the wireless
router we're going to be configuring later on the course you'll see I have to connect to it on a web interface and when I'm done then I actually have to follow some steps to get it set up through a web interface in other words there's no driver it doesn't install on your computer at all it just stays out on the Internet or stays on your Network all right so quite a lot of things there I really want you to know the driver installation thing that's something we're going to cover more when you become a real
when you become a technician and you're really doing this work you're going to have to always get drivers sometime it's easy you just plug it in a work works and sometimes you have to go to manufacturer's website and download the driver in this video I'm going to be talking about processors in particular three different type of processors that's mentioned on your exam so there are three kinds of processor you have your arm processor your 32-bits and your 64-bit processors now we want to go over those and you want to understand why you have them and
where they're used so let's get started first one we'll talk about is actually arm processors there are processors are mostly used in phones mobile devices uh small devices like your thermostat would have them um your car will have them your camera will have them uh your webcam will have them almost all Computing devices that doesn't carry either an Intel or or an AMD processor it's probably going to run some kind of an arm processor so they're incredibly popular for smaller devices and um I want to show you a list of War processes so you ever
say hey Andrew is there a lot of these things well here's a list of them that we have here uh so I am Wikipedia list of arm processors and if you know if you're looking at this it's just a lot a lot of processors so this is a uh this is a Samsung and the Samsung using the Snapdragon processor on this particular phone so this is basically running a arm processor processor all your Apple devices also will run these kinds of arm processors I know Apple made a brand new M1 processor but for now we'll
just go with arm processor um the other thing that I want to talk about is what's called 32bit versus 64bit processors so when we look at a processor all right your CPU in particular right so you take take this off here take this out this is our processor and you're thinking of a processor right you want to say what is this made of a processor is made of what's called transistors transistors is like a light bulb it's a mechanical component that basically carries a charge of either a one or zero computers reads binary digits and
the reason it reads binary is because processors are ones and zeros they either on or off those transistors is either a on or off the more trans resistors these chips carry the more faster they can process the more ones and zeros they can intake at any given moment nowadays it's not uncommon to have billions of transistors on a processor this one probably had millions and millions of transistors on this particular processor on all the processor now one thing that we want to talk about when it comes to processors not just the transistors but it's also
known as the bus width or 32bit or 6 64-bit processors a 32-bit processor basically means that it can intake up to 32 bits of data at a time versus a 64bit can intake 64 bits wor of data now this bit matters you see 32-bit a 32-bit processor uh for your exam to put it bluntly doesn't handle a lot of ram if you have an old 32-bit processor and I have a list of them here old 32bit processor like a Pentium 2 really old uh even up to pum 4S penum Pro notice how old these are
um if you have some of those older processors on an older machine then they're only going to be able to handle up to four gigs of RAM now if you have a 64-bit processor 64bit is exponentially larger uh the numbers are too big to talk about in this video but there exponentially larger when it comes to the amount of ram it can hold because if you remember from the diagram I gave you the the ram itself will feed data to the processor if you have a 32-bit bus here it can only take in 4 gigs
of memory at a time but if you're basically using a 64-bit processor which is all modern processors today almost every processor you're going to buy for the last 15 years or so Intel AMD processors they're basically going to support they're basically going to be a 64-bit processor uh and that means it's going to be able to take data from here and put it into here very fast means it supports a lot of RAM for your exam just remember 32bit versus 64-bit 64-bit just means it supports a lot of ram that's what you need to remember
for your exam now not because you have a 3 a 64-bit processor means you're going to get 64-bit performance you're going to be able to utilize all around you have to make sure your operating system is 64-bit you have to make sure that the applications are 64-bit now almost all os's made today are going to be pretty much 64-bit all your applications pretty much are going to support 64-bit so if you have an application that is very intensive like video editing software and it's a 32-bit it's not going to utilize all the RAM on the
machine the way to check this let's go back to my desktop is we are going to right click on the start button we're going to go up to system and in here it says about okay so right now you notice I'm running i7 processor have a lot of ram 64 gigs of RAM and you notice that system type 64bit operating system 64 X6 X 64bit if it was a 32 it' be x86 32bits are not known as X32 they're really known as x86 there's a 32-bit nature so so this is a 64-bit processor on running
on a 64-bit operat I could take advantage 64 gigs of RAM if I had 64 gigs of RAM installed on the machine and I had a 32-bit operating system it would only show 4 gigs here all right because the the operating system can't take in more so the bits matter the 64-bit versus the uh 32bit really really matters on this exam okay make sure you understand that concept for your exam you should get a question on the exam allowing you to differentiate between 32bit and 64bit remember 64bit just allows more memory on your computer in
this video I'm going to be talking about gpus and cooling how do we keep system components cool well as you can tell I have a device here the video card that I explained to you guys earlier this is a dedicated GPU or video card that we would call that would offload the graphics processing instead of having your CPU to which you have this device and this device runs really hot the CPUs run really hot so we keep them cool now before I get into this I want to bring back up my old desktop it's not
very old it's actually pretty new desktop um let's bring back up this desktop and I want to show you guys with the overhead cam how when you're looking at the inside of a computer what are we using to keep the inside cool well we looking look at this in order to keep it cool we're going to use a variety of fans you can see a fan that's right here now this one a little bit hard to see there but there's a fan right here System case fan that's keeping some of the components cool you also
have this processor underneath this is the processor notice you have a fan and you have this giant piece of metal this is keeping the actual CPU very cool you see when it comes to a computer the enemy of a computer is cooling CPUs get very very hot because they're transistors and they basically are like light bulbs millions and billions of them that turns on and off the CPU can get very hot and if it get very hot it'll burn out so what you have to do you have to keep it cool so what they do
is they put this metal piece on top of the processor the processor sits down onto the motherboard and then this metal piece called the heat sink connects sits on top of it and this fan keeps this metal piece cool and the cool coolness of the metal transfers to the processor hopefully keeps it cool if the processor overheats the machine will probably shut off reboot uh for all the machines the processor will die out nowadays do have some good uh fail safe mechanism inside of them now speaking about cooling one device that always needs a big
cooler and you're going to find when you're looking at devices is called GP pus so when you look at a computer and you're determining okay I want to play video games I want to do massive graphic and Graphics processing right you got to show those video games to make sure they look nice having the CPU do all the work to process the graphics can over tax or overburden the CPU and what happens is that Gamers or CAD design ERS or people that does movie editing what they're going to do is they're going to offload uh
their processing from the processor to a device that would literally come in and now for me to install this I got to take all these wires out would come in and would sit into this case and then they would connect everything right here all right so they connect all the monitors here so instead of the monitors being connected to the back of the machine here show you that if you can't remember see all the monitors we got the vvi we got the VGA we got HDMI port instead of instead of the monitor being connected it
be go through here so all your display would be coming out of here this is a GPU or Graphics Processing Unit gpus always carry gpus always carry if you look at a lot of gpus that are out there they're very big some of them are very long they always have a bunch of fans on them all right and on the bottom of these fans are massive heat sinks you can see the heat sink sinks directly through it like right through here there are heat sinks underneath them um if you look at the bottom here you
can see the heat sink that big metal part these fans are keeping that cool and underneath them is the actual GPU so video cards by the these are really called video cards uh but they carry the GPU so why do we want to to do this because that way the processor is not left processing all your graphics the processor has enough work dealing with your operating system dealing with the applic that you're trying to access the internet background all the background applications that you're using so why not offload dedicated get a dedicated processor for it
and let it process the graphic separate the problem again once again is cooling so how do we cool it we use heat sinks and fan the last part about cooling I want to talk about is something called water cooling system in the A+ class we'll go more into this but there is a different cooling system W water cool versus Air cool so water cooling systems basically utilizes components with little reservoir of water that keeps the water cool and it circulates around the computer why would you do that because it's a lot it's more efficient it's
a lot quieter so the computer I have on my desk is a water cooled system and it's a really powerful machine with a good video card but you really don't hear it because the water cool keeps it really really quiet okay make sure you for your exam you understand what a GPU is and how we keep them cool in this video I'm going to be covering motherboards firmware and RAM let's get into it so one of the most important components you're going to find in any computer or the most important component is the systems motherboard
I want to show you what it looks like when it's all set up within the case and then I have one that's already taken out something really simpler to look at and I want to show you the BIOS and the RAM on the machine so let's take a look at this desktop that we have in front of me let's clear up the space here so this desktop that I have in front of me is already built it works was running a few hours ago so hopefully when I finish this video it still works uh but
on this desktop what I'm going to do is I'm going to open up the case now opening up the case here a little notch on the side here we're just going to pull that and slip it out there now there was screws that held it in in the back now if you're really interested in watching me take apart the computer put it back together um changing all the components taking them out putting them back in talking about each component more in depth that's going to be your A+ for this one you just really need to
know what basically they are and what they look like so I'm going to take this out of here and what you can see inside where you can see inside this entire inner working of a computer now it looks like a bunch of ma a lot of mhup of cables that's within there what I want to do is I want to identify some of the major parts on this machine hopefully got a good view there let's go back to the over head cam so this is inside of the actual computer and there's a variety of things
here that we want to be able to identify now this one is fully connected and it's fully working it's fully fully functional all right and then I have a motherboard here that we're going to be explaining to you so right now inside here which you're looking at all these spaghetti of wires this comes out of this device this is known as the PSU or the power supply unit this device lots of wires are coming out of it and wires are plugged directly into the motherboard the it's also plugged into the hard drives uh it's plugged
into the fans this basically device Powers up this entire unit in fact when you connect your power cable you connect it to the back of this device and again to take this device out putting it back in that's going to be in the A+ so the A+ class actually use this machine to take it apart and put it back together 100 times in the class so in this one you got your power supply unit here you have drives this one has a DVD it has a uh has a DVD drive this is the hard drive
on the actual machine itself uh and we're going to be looking at hard drives and stuff like that a little bit later but what I want to look at in this video is going to be a couple things all right in here we have this unit you see this here this is called a heat sink this thermal looking this weird looking big piece of metal here that metal is covering up the CPU of the actual machine so the CPU it lies underneath this here you have your RAM all right this is going to be Ram
so this is easy to pop out all right now again if you want to learn how to take this out and all this good stuff please look into the A+ this is a ram stick all right this is RAM on the machine that we're going to use in order to store our programs to pop this back in here not hard to put in at all you should always change your RAM especially if you have a desktop that's back in here the other the other thing we want to talk about is going to be the BIOS
you notice there's a battery here this is called a seos battery bios battery the BIOS is a chip on the motherboard that stores computer settings like the time and date for example where if you go in you can change the BIOS on the machine change the boot order change um configuration on the processor and so on this little when you do that what happens is is that uh the settings is stored with little battery so if you ever uh if you ever work on a computer where the clock keeps going back you change St you
come back you turn our computer powered back on it goes right back uh to to an older time that's you need to change that battery now that battery lasts a long time I haven't seen one of those die in 10 plus years I mean I've seen machines be running 10 plus years the battery don't die but it's something for your exam uh so you can see a lot of different things so the motherboard is this giant board at the bottom this board that sits into the case the CPU is plugged into it the ram is
plugged into to it the hard drives are plugged into it you have a variety of expansion slots coming up here uh this is going to be a variety of expansion slots you got your PCI expansion slots here so this motherboard it's all fully connected now I want to show you a motherboard that is not connected let's put this one down yes yes I am very slow yes I know I'm very slow I'm old that's why if you're laughing at me when you get old you're going to be the same way and I'm fat that doesn't
help okay so here we have a motherboard now this is an older motherboard and I told you guys this motherboard is 15 years old probably and you say Andrew that's too old well they don't the components don't change all the motherboard form fact the different form factors they all all motherboards will carry Ram they'll carry CPU they'll carry carry some kind of BIOS they'll carry some kind of expansion slots they'll carry uh connectors for hard drives and so on they'll all have those things uh but this and this one is a really simple motherboard I
use a lot when teaching to demonstrate because the old things is just simpler to look at uh so I want you guys to look at this so on this particular one this is your RAM okay this is the ram this here would be your CPU we spoke about this in a previous video this is the cimos okay or the bios of the machine the firmware of the of the desktop this is that where that battery go on you don't have the battery this is where that battery would go one of the things that people ask
me is how does a computer work all right a computer stores data in the hard drive hard drives are connected directly on hard drive connectors in this computer there's SATA connector SATA ports right here your hard drive would connect here uh this machine is older does support older IDE so you can connect older IDE drives here but most of the time nowadays you have SATA connectors you also have solid state connectors we'll talk about hard drives later your hard drive stores your data permanently when you want to Output to a display you want to send
data out to the monitor right it's a VGA a connector this is that old parallel port I showed you guys before serial Port really old so you connect a monitor to this port when you want to access a program it pulls the data through from this port from the hard drive it then flows into the it flows into the ram chip data comes into the ram this is why Ram is important because the it's hold the program that's going to be running and then the RAM and the pro the ram will now send it to
the processor where it's processed and pushes up for display this one doesn't have a video card but if it did uh it can send some of the data to the video card which is generally would be plugged in here or here these are called expansions an AGP slot old AGP PCI slot and then it's outputed directly through this port and you'll see it on your screen so that's basically how a computer works okay it's it's not something that's very complex so watch once again in this view so you connect your hard drive in one of
these ports you say hey can you open let's say you want to open a video game all right so you double click you go to start you open your video game the hard drive is connected here it pulls the data from the hard drive into the ram the ram will now shoot it over to the processor why does it why does it not go from hard drive to to the processor well because the processor of itself the hard drive itself is very slow so it puts it into a chip that's faster to ram ram again
holds all your running programs the processor gets the data processes the data and shoots it out to your video card and you can see it on your screen if you have an attached or external video card it'll then shoot it through that video card here instead of on the Onboard video card that we have here um we spoke about processors in a in a previous video but the motherboard itself this is what they look like all right on the motherboard it's a very simple thing you have what's called expansion slots this is where you would
plug in those video cards your sound cards you have where you would put your RAM all right and this is really easy to upgrade you have your CPU you have hard drive connectors that we're going to be using to connect the hard dve SATA connectors you have all IDE connectors here here you have your seos battery your seos chip itself if you're wondering what this chip is here that's all white this is called a chipset chipset is like the Spy this is they call this a brainer machine this is the spine this is what coordinates
all the action between the ram the CPU and the video display being pushed out there's something called North Bridge and South Bridge you don't need to know that for this exam but that's what it is um so this is a motherboard uh if you want to learn more about this and the one I'm going over is just it's too much for your exam right now if you want to learn more about this type of stuff when you're a technician you're going to have to be replacing these things you're going to have to be changing Ram
especially troubleshooting hard drive or replacing failed hard drive is common replacing failed power supply and computers are very common to blow up at that point you got to get your A+ All right but for this course so all you need to know about these things in this video I'm going to be talking about storage devices and particularly different kinds of hard drives that are out there different devices that we can use to store data I'm talking more of a long-term storage your RAM only your RAM is known as volatile memory volatile memory means that when
you re if you turn off your computer you lose it so here I have our Ram chip so whatever is in this Ram chip if I turn the computer off I lose all the data it's called volatile nonvolatile memories when you turn the computer off you keep the data that's there that's going to be things like your ROM your readon access memory or also your bios which is your ROM remember I showed you the BIOS this is the ROM chip okay read only memory which means whatever is here when you turn your computer off you
unplug it you don't lose it same thing with your hard drive it's nonvolatile so when you plug when you unplug the machine you still keep your data so if you pick up your desktop you unplug your walkway you save something your desktop it's saved on your hard drive so that's what we're talking about in this section this is nonvolatile memory now these a variety of ways to store data one way one way we could do it is by using traditional hard driver a HDD hard disc drive hard disc drives is going to be your traditional
hard drive like I have here this is a traditional spinner based hard drive I call it spinner because there's actual mechanical disc in here that spins for your A+ exam when you get there I'll show you I have one of these where we take it apart and you can actually see the disc and the platters andever everything but know that this is a normal hard drive this here is relatively cheap and you get a lot of storage the problem is is that it's relatively slow comparing to what well I have here what is known as
a solid state dve this is a brand new solid state Western Digital solid state drive uh I say a solid state drive and I'm just going to open it this has not been open this is the first time this has actually been open and we're going to put it in the machine so I want to show you guys how these things are connected um these are connected using uh SATA cables and you connect either of them using the same type of cable solid state drives are very very fast they don't have a mechanical disc that
spins so imagine you want to access data the this has to spin grab it spin grab the data so the mechanical disc is always spinning for the for the for the mechanisms also known as the head to grab the data this is very slow although almost all of our computers have this stuff for our newer machines we're going to have a solid state Dr these are just chips basically like RAM chips that you have on your motherboard and they're very fast if you ever install one of these you'll see a massive difference between your old-fashioned
spinner drive and your solid state drive now I want to show you in the overhead cam how do we connect the hard drive well I again if you want to learn more about this you're going to take that A+ okay so this is called a SATA solid state these are called SATA connectors it's the same connector here and you notice this is a one tbte solid state drive this is a 1 tbte hard disk drive they connect the same way so here's a SATA cable and on this motherboard we have a SATA connector um and
all it is is basically now of course this is much harder in the computer so I'm going to take this cable and I'm going to connect it into that slot have one connected there and then I can now use it to connect to my hard drive just like that it's connected you would need to say the power cable from the power supply or I can connect this little device and you can see the difference in size they have the same amount of storage you're all one tbte this is a whole lot faster night and day
faster than this spinner drive now the problem with with solid state driv is that they're just expensive currently speaking solid state drives are really really expensive a one TB solid state drive 100 bucks one tbte hard disk driver htd spinner drives $30 $40 getting a 2 tbte Drive can be really expensive stylus Day Drive comes in two form factors there is this one what's called a SATA form factor and there's something called nvme nonvolatile Memory Express so I'll show you guys that I have a picture of one here this is an nvme drive it's basically
this is a 256 gig nvme Drive these are the fastest uh you must have an nvme connector on your motherboard but this is going to be the fastest solid state drive you notice it says SSD on it so it's a solid state drive is an nvme solid state drive incredibly fast if you're looking to up your performance on your computer you're going to get one of those if you're motherboard supports it you're going to have to have a re relatively newer motherboard maybe in the last 3 or four years if it's a if it's in
that borderline for four or five years you're probably going to have to have the higher end of your PC back then uh but that's what it is the other one I want to mention is you're going to have thumb drives USB thumb drives store data called thumb drives because they generally the size of your thumb this here we went over already so this is going to be some of the storage devices you going need to be familiar with for your exam in this video I'm going to be covering Nick cards n IC Network inter inter
cards net nit cards or network interface cards is what we're going to utilize to connect our computers to a network whether it's a wired or a wireless network so if you're at home right now and you're just surfing the internet on your laptop on the couch there's a wireless interface card on your computer that's connected to the wireless access point in your house if you're at a gaming desktop and you have a cable plugged into the back of your computer that's plugged into a switch or or your wireless router that's going to be a wired
network interface card let's see the difference so uh here I have the motherboard and you notice this motherboard here has a builtin nit card so this is where I would connect so here's the network cable that we saw earlier this is where I would connect that RJ45 cable into and then I would plug this into the router so this here would be what is known as an onboard niit card now if you want to add let's say your computer doesn't have uh you want to add Wireless to your desktop which is something pretty common and
you realize oh my desktop just doesn't have wireless well you could it doesn't have it onboard laptops generally come with the wireless cards built into the onboard system but a lot of desktops don't in fact they have what's called an add-on card an add-on card would look like this this is an add-on card uh a wireless Nick card that is an add-on and and uh this one here not something super old but I think this is an N wireless Nick cart and basically on the motherboard you would have to have a specialized slot so I'm
not going to go into all the different slots on the motherboard keep that for A+ and you just basically plug it in and you would have the ability to have wireless uh Wireless connectors so this would be an add-on card another variation of an add-on card instead of having to go plug it into the motherboard is something that looks like this this is a US B add-on Wireless nit card so this here would just plug directly into your desktop or if your laptop doesn't have wireless and you want to add Wireless to it this would
be the way to go you can see that this is a relatively pretty small device it's a TP link I bought this device to to teach my ethical hacking course with uh because it's one of the only devices that Ki Linux picks up take my uh Security Plus I talk about this this was my C Class okay so you have different type of niit cards you have that wired niit card you have the wi L Nick card right connects to wire Network you have them can be on board built onto the motherboard or you're going
to have to get some kind of an add-on when working as a technician you should understand different kinds of internet connections that are out there like which one is faster DSL versus cable or versus fiber optic which one allows you to work in a rural area versus the other one so captia gave us a variety of different uh internet connections that we should be familiar with now you don't need to worry how to set these things up or configure them for this particular course look at more of that in the A+ but let's take a
look at it so we got fiber optics cable DSL and wireless internet now when it comes to internet connections the first one up you have were dialup internet connections like I connected on my 56k modem using a good old fashion telephone system back in the 199 90s the 56k was really really slow in fact to download One MP3 would probably take me 10 15 minutes nowadays take seconds so we have evolved from that all right so we we don't have those kinds of old internet connections anymore what happened was one of the to get broadband
internet broadband internet allows you to run multiple signals on a single cable broadband internet one of the first ones that came out was known as DSL or digital subscriber line so DSL is basically internet broadband internet or high-speed internet that basically runs on good oldfashioned telephone wires or telephone line DSL was widely available because basically if you had a telephone line run into your house you could have gotten DSL it wasn't very slow but again it wasn't very fast DSL was in the megabits you could have got DSL 2 megabits 3 megabits 4 megabits 6
megabits down and your upload was pretty slow at around 1 Meg or so now another widely available internet connection that came out was cable internet because so many neighborhoods and houses already had cable lines run into it I'm talking coax cable like cable TV people were able to get internet through their cable TV I remember having Time Warner Cable internet connection this was a lot faster than DSL uh it was relatively cheap as it was going through your cable provider then came the fiber optics such as Verizon's files Google Fiber and so on this allows
you to get hundreds of Megs and gigabits of internet connection for example in my house here I have the FIOS internet connection FiOS Internet basically goes at for me 1 gbit for businesses you can get multiple gigs when it comes to other other types of internet connections we're going to have wireless now Wireless is great because hey there's no wired connected to it you're already familiar with this because you're familiar with cellular Wii cellular Wireless this is what you're going to have in your 5G 4G and 3G networks this allows you to have from a
few Megs in 3G and 4G to gigabits of Connections in your 5G cellular network that you're probably going to have on your cell phone at Japan your cell phone provider at another one you're going to have is radio frequency now radio frequency this one is going to use antennas where you have you must have an antenna in your house and the provider has an antenna facing each other and you're able to communicate and get internet this way I haven't seen much of these implemented I saw few of these implemented in business in New York City
we have antenna placed by the window and all antenna placed by provider able to connect getting popular satellite internet now satellite internet has been around for a while and it's used in really rural areas in where you don't have any cables you don't have any major distribution points or access points to connect to like you would on need on sell your or cell towers as long as you as long as you can see the sky the um the antenna can see the sky it can connect to the site and give you internet reg generally it
was considered very slow but nowadays we're having satellite internet that is getting faster and faster for relatively a cheap amount so this means that you can probably get any internet anywhere that you can pretty much see the sky and there's a lot of satellite services that are coming out that's going to basically allow that okay so these were some internet connections that you should be familiar with one of the first Broadband was DSL random telephone lines you had one that ran on cable lines such as your cable connections then you had one that run a
fiber optics cable fiber optics cable gives you the fastest connection out there as fiber cables which uses a glass or a copper core are very very fast cable then you have the variety of different Wireless some cellular that we use in our cell phone some of us that live in rural areas may have a satellite connection or even a radio frequency in this video I'm going to be talking about storing data but not locally storing it like you would on your hard drive I'm talking externally from your computer let's get started so you got a
computer you got a bunch of data in it you got it on your hard drive right your hard drive you got a two terab drive you got a bunch of pictures you got music you got videos and you say to yourself okay I don't want it on here I want to store it somewhere else maybe something that's more uh redundant that they want Drive failed you'll just lose all your data uh so in this situation we're going to use a couple of devices we can use a Nas or a file server or even we can
even store it in the cloud in which case we store it on somebody else's Network let's get into this so couple of terms here we have to know Nas file server and Cloud storages let's see if we can differentiate it the first first thing up we're going to talk about is something called a NAS network attached storage okay NAS network attached storage so what a Nas does it's basically a box that's connected to your network that's just a dedicated storage device it's like connecting a hard drive taking a hard drive and plugging in network connection
into it it doesn't have an enclosure for it um I have in my network something called a sonology box I'll show you guys what that is in a second is basically a box of hard drives that I connect to my network and I store all my pictures and my movies and my music files on there so it's not on any computer that way I can access my movie files or my uh music files from any computer in the house another one is a file server now file servers are really going to be used by businesses
in a business they're going to have a big tower computer and I'll show you guys one of them that they put hard drives into and they all the people in the office shares data from that particular computer known as the file server this machine is serving up files to everybody now technically speaking a Naas is is a is a smaller file server but the file server is a is going to be a dedicated real full-fledged computer server versus a n just a really dedicated storage device another thing that you can store data on is going
to be CL cloud storage now it's 2022 and you're probably using some kind of cloud storage to store your data for example you may be using Google drive to store data on Google's Cloud Network or you may be using my favorite one is Dropbox that I used to store all my data in and these are pretty much free that you can use to store data in so you're thinking of all these types of storage you have to think okay do I want to keep stuff on my computer no you want to offload them to something
like this so this is a Nas and this is going to be uh a analy to this Bay nas dis station so this is just a box it's not very big it's actually a very small box and at the back of it it basically carries as you can see just a box of two hard drives in it and it carries a couple ethernet ports on there that you can use to connect your computers to you connect your network to and then your computer would then connect to this to store data I use this to keep
all my pictures and my music files on and my movies see if I'm sitting at this machine I can watch a movie if I'm going to that machine I can watch a movie right off the nas in the house the other one is going to be a file server so a file server is basically a server computer that you purchase from a company like Dell these machines are going to be dedicated machines that's going to use to serve files on your network they're going to run a server operating system and they're going to have a
bunch of hard drives configured in a highly redundant array if you want to use things to store your drive in one of those Cloud storages you're going to use something like Google Drive in order to store data on the cloud byway when people say cloud they literally mean somebody else's Network a lot of times when we say oh we put my data in the cloud there's not many big cloud providers there basically three AWS is Amazon Google cloud and Microsoft is yours Cloud so Amazon controls the network Microsoft controls a network and Google controls a
cloud Network so people say all put my data in the cloud it means basically you're storing it in Microsoft Network or AWS Network or Google's Network so when you use things like Google drive or you're basically storing in Google's Network Dropbox for example runs on AWS or Amazon's Cloud systems so I'm basically when I use dropbox I'm basically storing my data in Amazon in this video I'm going to be going through a variety of different devices that you should be familiar with for your exam now most of you that have used the world of computers
or play games at home probably already know most of this so let's knock this out pretty quickly now if you don't I will be going into it so the first thing I we want to know is basically the purpose of mobile phones nowadays things like mobile phones are really just handheld computers mobile phones allows you not just to make a call but send text messages check the internet and can basically do anything your desktop or laptop can do just on a smaller screen so mobile phones are absolutely great because it seems like a lot of
us can't get off of these devices but these things are really just general purpose computers with the ability to make a call nowadays following this up is we're going to have tablets so here I have a Windows tablet now tablets basically are giant mobile phones for example if you have an iPhone or an iPad you'll notice the iPad is basically a large iPad a large iPhone you have an Android tablet and an Android phone such as this this is an Android phone basically it's just a large phone except it doesn't have the ability to make
calls this is a Windows tablet so it's just a smaller version of what I would have on a desktop Now laptops laptops are of course going to be basically like desktop computers except they're smaller laptops are going to run generating a lower power mode but they're going to allow you to do basically everything you could on a desktop except it's portable it comes built with a screen bunch of connectors but it's probably not going to be as fast and it's probably going to if you want the speed of a desktop you're probably going to spend
a lot more money when you're working in businesses today you're probably going to work on what's called a workstation in a business you have what's called servers and workstations a server is basically a device that will serve the data or process the data for you and there's a variety of servers in businesses nowadays you have database server you have file server you have a print server you have a web server and these are dedicated servers that serves up different things for example a database server will run a database a file server will give out files
to everybody on the network a print server will have a bunch of printers connect to it so people can connect it that to print to different printers so servers basically serves the data in the network now workstations is where the user sits and gets work done it's basically just a desktop computer generally with a specialized operating system such as not Windows home but Windows Pro would be installed so could be managed more efficiently in a business Network the other one here we have is going to be gaming console the gaming console such as your PlayStation
one you know the last gaming console I had was a PlayStation 2 and after that I really didn't play much games after that it's called console games my son still does but gaming console nowadays such as a PlayStation 4 PlayStation 5 or whatever number they're up to are as powerful as some of the most powerful desktops that are out there in fact they are fine in one can be difficult but gaming console now is a basically high-end computers at a pretty cheap price they come with massive massive GPU in them and they able to display
and process Graphics very very fast all right these are going to be some of the devices that you should be familiar with for your exam in this video I'm going to be talking about a term that you're probably going to hear a lot of in the coming years it surrounds you and you need to know it for your exam and that's called iot also known as The Internet of Things iot devices are basically any device that can connect to the internet if you think about this around you right now what doesn't have an internet connection
iot basically refers to every device that connects to the internet such as what well if you think about it your thermostat if you have like a nest thermostat you can connect to the internet I have the nest thermostat I can turn up and down my uh temperature in my househ it your security system if you have an ADT system you can turn alarm and dis alarm your modern cars all have IP address Tesla cars can download updates from the internet IP cameras you can access your your your camera system from your phone streaming media devices
even medical devices such as x-ray machines can be monitored or or can actually do work remotely on an internet on some kind of network connection so there's going to be a variety of home automation devices your appliances your fridge connects to the internet can you think of something that doesn't connect to the internet things like what your toothbrush there is such a thing as a Bluetooth toothbrush brush your shoes there's even a coffee cup that has Bluetooth to monitor the temperature all of these devices that are now connecting to the internet to become more quote
unquote connected means that they could be managed accessed and monitored remotely which is great because now I can turn off that lamp over there because I don't want no more light without getting up uh I can brew coffee in the morning by just going into my phone and say brew coffee I can turn up and down the store over not stove the uh the oven in the stove for my phone now what this mean this is great because it allows more connectivity and EAS of use in life but with this comes a variety of complex
technology because some of them will run on Wi-Fi some are run on Bluetooth and then there's a variety of different kinds of uh iot protocols we'll cover in another class but it also brings a lot of security problems because if all these devices are becoming more connected to the internet it also means that more hackers can access that back in the you know I drive a pickup truck big old pickup truck it has no Connections in it has no remote connection and no hacker can hack my car but if you're driving this brand new Tesla
car which are always on internet connection can somebody hack into your car and run you off the road they can't do that to my big old pickup truck because well it doesn't really have any internet connection on it versus the modern cars that do so this is of course going to Pro create some kind of security issues as we go forward in the future but for your exam right now just know what exactly is iot on my desk I have a wireless access point and a switch combination this is my sonic wall we've been using
throughout this course this is also again once again it's a firewall but it also is a switch it is a access point so if I take this network cable let's plug into this device and I was to plug into this laptop I get on my other laptop and I plug that in to this device now I have two computers that can communicate when you set up a network something small like this and again I can have uh wireless devices talk to it maybe I have a another wireless laptop or a tablet so I would have
my my laptops I would have my tablets maybe my phone can connect to this and we can all share resources like files or pictures or movies or something like that within my little room here within my ual little house when you set up a network within your house within a building within a single building it is called in the world of technology we call this Alan now Alan known as local area network is basically a network that is defined as something that is limited to a single building so a network within a building within a
floor within your house would be considered a local area network so Noti this term for your exam local area network now the opposite to a land is known as a wang wide area network wide area networks is networks that spans the entire Globe it's large corporate Network so let's say you have a you have an organization that has a building in New York and you have another one with one in Texas and they connect these these two buildings using some kind of lease dedicated line hosted by an ISP or some kind of uh line provider
and now you have people in New York talking to people in Texas uh like they're basically in the same network this is known as a wide area network if you're saying to yourself well I have a a land because I have a network at home have I ever used a wang well one of the biggest wangs out there or again why network is the internet the internet is the world's largest wider Network a wang is not limited to really any boundaries it's as wide as your imagination it's the biggest Network we have the internet is
a Global Network it is not a network that is confined to a building or to a city to a state or a country it's basically the entire world so know that term for your exam a land is confined generally to a single building versus a wide network has really no boundaries and it's basically a Global Network in this video I'm going to be talking about a pretty interesting topic and something that you're probably all use already or you are using it because you're watching me on some kind of streaming media and that's going to be
the basis of packet transmission and what this is is how exactly does data transfer between a network device and a computer or between a computer to a network device and to another computer how exactly do we get internet well it's a pretty complex topic and I'm going to try to keep it real simple just enough for your exam in this video so the first thing we want to talk about is what is used to transfer data well in the world of technology we use protocol okay a protocol is defined as a set of rules that
people will follow or the computers will follow in order to communicate so a protocol is basically the language we are speaking it's the definition of the communications that's happening between me and you right now I'm speaking English and you're listening to me in English we must all follow the rules of English English that this word means this and this sound means this that way when I communicate you can understand in the world of communication the protocol that we use that you guys should be familiar with for your exam is going to be tcp/ip transmission control
protocol Internet Protocol tcpip is going to be the protocol that we use to communicate between computers all computers in this world right now every single from your laptop desktops to your mobile phones to your iot devices they all run this protocol that's how we can communicate think about this if you're speaking German and I'm speaking English can we communicate let's say I don't know German you don't know English we probably cannot communicate we can't speak communicating but if I know English and you know English and I speak English and you speak English we can communicate
tcpip is basically the language that we we communicate in the world now tcpip is known as a protocol stack it's not actually two protocols it looks like it's to it's transmission control protocol and Internet Protocol well the the well these two Protocols are basically made up of many other protocols that we use in the world of communication this will cover more in in courses such as Network plus and a little bit in A+ but we really expand on the we're really going to expand on the concepts of TCP and the concepts of Ip in those
courses but for now just remember that we communicate in today's world computers communicate to each other using a protocol named tcp/ip or transmission control protocol interet protocol to elaborate a little bit IP the Internet Protocol is responsible for routing of data this particular protocol is what we're going to use to Route data across the internet okay across your network it's going to allow data to go from your internet service provider from Google's web server to your internet service provider to your house it basically routes data IP is famous for giving you an IP address a
logical address assigned to all host on a network transmission control protocol this one does quite a lot this one checks to make sure when your data receive comes to your machine is Reed good if there's any errors it it's going to be able to fix it and there's a few more things but that's basically the gist of it so just remember the basis of packet transmission is going to use a protocol called tcpip and when data is traversed in a network they're called packets so what leaves the port is called a packet so packets leaves
the port onto the cable and the packet arrives on your machine in the world of technology we actually don't we we actually don't say data is Traverse in network packets are Traverse in network when you look at Network scanners these are going to be software and devices that actually looks at Network traffic and actually go in and see the network traffic itself that's going to be uh something that's looking at a packet right they don't say data they say packet analyzer protocol analyzer all right so don't forget guys we use tcpip to communicate on our
Network it's the protocol of choice throughout the world if any device wants to communicate on the Internet or in a network they must have tcpip installed which almost every computer on the planet do and in this video I'm going to be talking about device addresses IP addresses and Mac address let's let's get into this so I have my phone okay I have a wireless access point that I have here and I have my laptop okay so you can see the setup here so let's say my ACT my lap laptop is joint to this access point
so this access point basically allows the lap this is the wireless network receiver and the phone is also joined to your wir so you probably went into places before where you oh can I join your Wi-Fi uh to take your phone and join the Wi-Fi but let's say my laptop is also joined to the Wi-Fi okay but let's say I want to share data so I want to send some data from my phone to my laptop all right but let's say there's 10 other computers let's say there's 10 other machines that's joined to this wireless
network in order for data to know where it's correctly going there has to be some kind of addressing scheme think of when the post office sends you sends you mail in order for the post office to Route the mail correctly to you you got to have some kind of address right you have a house address in there so in this setup in our Network in today we must have addresses now in the world of it we have addresses and we basically have two kinds of address we have what's known as a logical address a logical
address is an IP address or Internet Protocol address we spoke about ite IP previously was part of the TCP IP protocol stack that we're using to communicate in a network computers will also carry what's known as a hardware address Hardware addresses are basically known as a MAC address or media access control that's that's a number that's assigned to your Nick card By Your Man by your manufacturer now I don't want to get into the specifics of Ip addressing and Mac addressing in this course but it's something we get into in A+ and especially in network
plus and things like Cisco but I'll give you the basics of what they are in this video so once again every device in a network must carry an IP address or Internet Protocol address every device must also carry a MAC address within the network an IP address is known as your logical address C and this is known as as a physical p h y s i c a physical address an IP address is something that we assign okay as the administrators of the network we assign the IP address the MAC address is assigned by the
manufacturer of that machine or that particular nit card every single computer or Computing device that's built in this world carries a unique Mac address that's assigned by the manufacturer so for example let's say Samsung this is a Samsung phone let's say Samsung made this phone and on this phone there is a MAC address for the wireless niit card built inside who assigned the MAC address Samsung did but the IP address that the phone gets within my network is assigned by my networking device as your career GRS up when you become a network administrator you will
determine your IP address and scheme and in this video I want to show you what does an IP address looks like and what a MAC address looks like so an IP address an IP address is basically on IP we should say version four address okay want to point that I could this version four and version six addresses for this video I'll just keep it to version 4 cuz that's what we most mostly still use especially in internal networks all the version six is really starting to replace it but for an IP version 4 address it's
basically going to be four numbers and it's represented as X XXX dox and each number is between the numbers of 0 and 255 if you really want to know why take my take the network plus class and A+ I'll explain that to you in more detail so an IP address basically looks something like this it'll be like 10 20301 that would be like an IP address so and again this is something that your company is going to sign or if you're the administrator you're going to be assigning it there's ways where you you can manually
assign the address that's called a static IP address and then there ways where you have something called the DHCP dhp the dynamic host configuration protocol this is a particular protocol that's configured by an administrator that automatically assigns IP addresses to your network network devices so if you're at home right now and you just connected to your wireless network and you already got an IP address that's what's giving you that IP that protocol called DHCP the other one is going to be a MAC address so an IP address by the way is a 32bit address a
MAC address is going to be the uh Mac address is going to be a 48-bit address it's written in a hexadecimal and it's written as digits uh each one of those X represents a hex can you remember from the beginning what those hex were can you remember that all right so it's a 48 bit address and basically you're going to have uh let's see 1 2 3 4 five 6 7 8 8 * 4 is 32 we'll do x one more time and x x so it's a pretty long address it's actually broken into six
different p peers of numbers so you have one perer here one perer here one perer here one perer here one perer here one perer here total it each one of these X represents four bits now you're probably saying Andrew what the hell is all that can I see it well I'm going to show this to you in I'm going to show this to you on my computer my actual IP address and my Mac address so let's take a look I am going to go now you don't need to know commands for your for your exam
okay okay uh you do not need to know commands for your exam once again but you will for other certification so I'm going to do ip config slash all okay so now I don't really want you to worry too much about commands here for a second but I do want you to notice that on this computer I am connected to the FiOS home router so I'm connected to my files I have my IP address no notice 192168 1.80 this is a preferred it says preferred because it's a static IP that I put I manually hand
type this in but you notice that I also have this Mac address so remember I told you it's basically six pair of hexadecimal numbers see see it here so notice you have 8881 59 29111 C this is going to be my uh Mac address or my physical address on the actual machine machine so and if you have multiple Nick cards installed it's going to give you one for all of them remember we looked at that TP Link adapter uh Wireless Nick card in a previous video so this one it's not really configured yet but I
do have uh notice Wireless it's the TP link and notice this one also has an address it's not connected to any network so it doesn't have a and because it's not connected it does not have a IP address so it needs to be connected to have that IP address I don't want you to worry too much about the actual um uh formatting of these numbers or exactly how to type in IPS that we're going to get to as we move up in our career but I do want you to understand that devices on a network
must have an IP address logical address assigned by the administrator generally within the network and the MAC address is assigned by the manufacturer it's not something you're going to sign I've never really had to assign one in my 20 plus years of doing this it's given by the manufacture and its deer as the physical address in the previous video I told you that every single device on a network must have an IP address did you also know that every single web server on the internet also has a unique IP address assigned to them and when
you want to access a website you have to know that IP address isn't that so is it probably not right because you're saying I don't know any IP address to any websites well your computer does you see in order to access any website on the internet you must know its IP address or at least your computer must know its IP address in order to access any resource on a network you must know its IP address or at least again your computer must in this in this video I'm going to look at something we call DNS
domain nameing or domain name server some people say domain name server some people domain name and service domain name server service there's a variety of different meaning let's just say domain name server for now Dess is a service that's used to translate between a more more more than likely a domain name and an IP address so when you want to access something like google.com your computer doesn't actually need to know what is Google's IP address or you don't need to know it because your computer will then use the service to find it you see this
is called URL to IP translation the URL or uniform resource locator is HTTP uh HTTP uhon ww.google.com that is Google's URL your computer will take that URL give it to the DNS server the DNS server say oh you're going to google.com here's the IP address and then your machine goes right to Google so your computer doesn't and you don't need to know IP addressing why because we use DNS to turn those URLs into IP address I'll show you what I mean so let me just exit this here and uh let's go back to my desktop
where's my desktop here we go so at my desktop here at my desktop I'm going to go to my command prop I want to show you something watch you see if I ping google.com now ping is a command that we use when we are trying to determine if a host is alive I want to show you something notice when I pinged it it didn't give me google.com it gave me an IP address you see this right here that is the IP address of Google if I copy this contrl C and I open up a web
browser okay I have Edge open here all right if I open this browser and I go to uh I just put that address notice I'm just typing that address in there then what am I going to see let's take a look notice it's Google did you see that so watch again I go here paste that address in there I was just going to go ahead here and press enter notice it's Google so this is every time time we access every time we're on a computer and we go to a URL yahoo.com google.com bing.com amazon.com anytime
you go to any one of these URLs you're basically go to its IP address now the service that's translating between that IP address the the the domain name and the IP address that is DNS all right so know for your exam DNS is when we're going to translate between domain names and IP addresses in this video we're going to be talking about protocols so earlier I spoke about the main protocol that we're going to use to communicate on our network tcpip is the main Suite of protocols that we're going to be utilizing to communicate within
the network now I do want to point out tcpip is not just two protocols it is the name of the suite of protocols in fact in the world of technology when you want to communicate remember protocol means speaking the same language when you want to communicate to do certain tasks like transfering a file you'll use something called FTP file transfer protocol when you want to just transfer a web page from one computer to the next you use the hypertext transfer protocol or HTTP when you want to send an email you'll use a simple mail transfer
protocol to send emails in other words anything that you want to do on a network of sharing resources whether it's sharing a print job to a printer a file to a user connecting to another user's desktop if making a phone call using a VIP or Voiceover IP uh uh computer or software you're basically going to have to get a protocol to do it now in this video we're going to talk about four protocols that we should be familiar with for exam that you're pretty much going to use all the time and there's two tasks we
do all the time on computers nowadays we surf the Internet and we send emails so we're going to look at uh a protocol used to transfer page HTTP and protocol used to send and receive emails so the first thing I will take a look at is what is known as HTTP the hypertext transfer protocol this is a protocol that you have on your computer and so does a web server so Google have an HTTP server or basically a web server we should call it so this server has web pages on it and you want the
web page so this protocol allows that web page to be requested and transferred from from that web server to your web to your workstation so the hypertex transfer protocol basically I you transfer web pages now when you go to a website you always want to make sure you're using https if you're using HTTP website it means it's not encrypted that means anything that you do on that website hackers can see it so if you're going to a website that doesn't have an https we'll take a look at I'll take a look at URLs in a
few minutes when uh after I come off with this slide but I'll show you guys what I mean when I say we should always look for that https https means secure so it's a secure version of it now when it comes to emails these these three here are email protocols all right pop three a post office protocol and IMAP internet message access protocol POP 3 and IMAP are both used to receive emails so you must configure one of them in order to receive emails from an email server so the email server configured with IMAP or
pop 3 and you're going to configure your computer to join and receive emails from that email server now POP 3 is the really old one okay really old no one really uses that because it doesn't synchronize with the web server it just takes all the mail and then there's nothing left on the server in today's world we almost always use IMAP when setting up emails uh IMAP allows you to synchronize with the web server so you can configure IMAP on this machine to an email I can configure IMAP on my phone that way if I
send an email here I can see the send items here if I check an email here it also tell me a checked here if I was using POP 3 if I download all the emails here I'll never see it here because all of it is here so we don't use pop 3 we use IMAP when setting up emails to receive emails if you want to send an email that's another protocol simple mail transfer protocol this one allows you to send emails so when you're configuring an email client I'll show you in a minute you have
to configure either pop or IMAP and of course an SMTP to send there's only one send in protocol but there's two receiving protocols so you need two different protocols one send one to receive um you know there's one thing I tell my younger students is in the world of it oh my God there's so many protocols that are out there it's going to drive you crazy before we go though let's take a look at some a little bit of a Hands-On a little quick lab here to show you these protocols belong so the first thing
I want to talk about is when you go in to a URL so if I go to yahoo.com and now it doesn't want to show me the full URL until I click on it but I can see into this URL I can see right here it says https you guys see that this means that this one is secure um this you want to make sure that when any website you go to is secure so if I take out the S it'll go right back because this SES default to that if you ever go to a
website that doesn't have an https on it uh a lot of times the browsers will give you an error it'll say something like oh this site is in secur sure you want to go there and you shouldn't almost all websites on the internet nowadays should have an S at the end of its HTTP that means it has a certificate installed and the certificate is going to help with the encryption process needed to encrypt the data between you and that website the other thing here we'll take a quick look at is configuring mail so I'm going
to go to start open up my control panel and in my control panel I have this thing called mail now I do have a few email accounts that is configured on this machine this is how we would set up like Microsoft Outlook by the way so if I go here uh I have two I have instructor instructor one so I'm going to go here and I'm going to say new and I'm going to say I want to manually set up the the email CU I want to show you that it's going to access at SMTP
notice it says pop or IMAP notice you can't select both because how you receiving your emails is it pop or IMAP a lot of times the email service that it's sending out it's giving you the email will only support pop or IMAP now most of them pretty much support IM app really nobody uses pop anymore so when I click next I now have to put in my my name my email address is it a pop or is it an IMAP okay so if I select pop if I select IMAP it wants the name of the
server so this would be like im. server.com and then SMTP notice I have to put in the SMTP this is going to allow me it says outgoing do allow me to send email so if I configure the income incorrectly I'll be able to receive the email if I don't configure the outgo incorrectly able to send anything and vice versa too so you would put in SMTP dos server.com this is just some madeup names and then you would put in all this information click next and it'll set up the email for you you know working in
it protocols drive you crazy because along with protocols will come port numbers and then that drives a lot of younger it folks crazy because so many protocols so many port numbers that we have to know but we'll cover more of those in later certifications but for now these are the four protocols you need to know for your exam when you're working on a network you're going to have a whole lot of devices that creates a network whether there're switches routers firewalls modems and so on that you're going to have to set up a network and
in this video I want to talk about these devices and give you a brief overview of what they are sometimes we'll I'm look at some business end devices and look at some home devices also let's get started so the first thing up I have is I have a list of devices that I'm going to talk to you guys about the first one up I have is considered a modem so a modem is also it stands for modulation modulator demodulator modems originally Were Meant to convert analog to digital and digital to analog so you would get
a 56k modem a 56k modem is an old device back in the days in the 1990s when we connected to the internet using dialup actual telephone lines the data coming through the telephone lines were basically nothing more than analog signal the modem would then translate that analog signal to digital signal for the computer to read is computer can only read digital so that's for the word modem modem is not actually a word It's actually an acronym intial modulator demodulator analog to digital I'm back from digital back to analog now noways though we use modems like
cable modems technically a cable modem is not a modem but nowadays when we say modem it's just the box that's used to bring the Internet to our house from there we can then split that traffic up there we would use a router routers are used across the internet in order to connect dissimilar networks and use inside of large organizations to connect dis similar networks in a business today we're going to have many networks that are set up you may have separate IP network for sales a separate one for accountant separate one for management separate one
for it uh it management so you have a router to connect them now routers can a lot of you guys may think of a router as the modem that you get internet from well that device that you have at home is a combination device a lot of you guys have a device that looks like this like Sonic W this is a router it is a switch and it's an access point switches allows you to connect computers together a switch basically passes traffic from one port to the next see if I connect one computer here and
I connect another computer here the switch allows data to Traverse um the the network cable into the device and then back out into the next device so the switch allows them to communicate an ACC a wireless access point is basically a switch a wireless switch it allows computers to connect through these teners and it allows them to communicate this device is basically a 3 in one but this device is also a firewall because firewalls are used to protect your network from people breaking into your network you need firewall so hackers coming through the internet they're
going to hit this device this device is going to say you know what you're not you're not coming in here I'm going I'm going to block you out now these are combo devices these devices do them all it's a small business device you put it in your house has a has a router built into it so you can connect that Wang of the internet to the Lan of internally it has a switch so you can connect computers to it it has an access point so you can connect wireless computers and it has a firewall to
protect your network the all-in-one device right okay so those are the descriptions of the devices that you should understand router connects dissimilar networks a switch a logic to connect computers within the same network and access ACC point is basically a wireless switch allows wireless devices to communicate and a firewall will protect your network now before I leave this I decided to show you guys something I said that this sonic wall is a combo device right has many different functions a router to switch it to firewall but in big networks you don't have anything like this
in big networks you have dedicated routers dedicated switches and I have some of those Enterprise class equipment right here and I want to show you this bad boy now this one is a older device but this is a Cisco 2800 series router and this router is what you would plug in your internet and then it would bring Internet to the internal organization this thing is massively heavy incredibly heavy too heavy for my hands this is what it looks like it's an old device but trust me they haven't gotten much small so this is a if
you've never seen a Cisco router this is what they look like 2800 series Cisco R notes it has a power thing there it has an Ethernet port on it but it's in the back where all the magic happens this is where you plug in interfaces now we do use this to teach our Cisco classes uh but this is where you would plug in the internet line so this one can support a variety of and you can see this interface right here uh could support a variety of um Wang lines different kinds of Internet lines would
come in here and this router can support many of them as you can see we have many slots not being used there a variety of different internet lines can come in here and the organization we get internet that way see if you have never seen a Cisco router they do come smaller and they come a lot bigger some of them looks like a fridge uh like those double double door fridges some of them looks like that so and this is actually a small to midsize business router now a switch oh that think is heavy a
switch when you're thinking of a switch I showed you this one this one only has a couple of ports on it in fact this one has about four working ports on a switch and there's a couple other ports there one has a console port and a couple of Wang ports connect to the internet but in a business you need a lot more ports than that right in a business you're not going to have four machines you're going to have 50 machines well here is a how many ports is this one 24 port uh Cisco 2900
series switch I believe yeah this is a 2900 series Cisco switch something like this would retail when they're brand new we probably retail for a few thousand dollar the so so would be the router they're retail for a few thousand and you can notice all of these ports and they're highly managed you can really configure these uh in there so in big businesses this is what we're going to use to this is what we're going to use to manage our systems now if you really want to learn to configure these kinds of devices especially these
Cisco devices Cisco routers Cisco switches that you're going to learn Cisco take your CCNA uh your CCNA CER great certification to get that your it career progresses but before you do that get your network plus so you can get your basic concepts of understanding how networking works and then you can go in and study how to configure these giant monster devices that I'm standing next to in this video we're going to be talking about Wireless and in particularly the different kind of Wireless standards that are out there and if you're currently using a wireless network
how are you going to secure those wireless networks so what I have here is my sonic wall this is sonic wall we've been seeing all the time this sonic wall is a firewall but it does have an access point built in and it does a lot for wireless connections onto it right now it's powered on as you can see and uh I'm actually connected to its web interface and I want to go through some of the wireless settings with you and I want to show you what your exam wants you to know uh about configuring
these kinds of devices now for this exam you don't want to go in depth into this this is going to be much more covered in A+ but I do want to review some of the uh settings with you and I do want to review some of the things you should know for your exam so let's take a look at the exam of objectives so the first thing up is you should know that wireless network is based on the i e itle e is the organization of where we make all types of standards for electrical equipment
I 80211 80211 specifies the standards that we use in Wireless networking 802.11 comes in a variety of types you have a b g n AC are some of the standards that are out there for example the wireless standards of a and B are very old A and B uh for example B was 11 megabits which is very slow G was 54 megabits which was getting faster and you had a few 100 Megs on end depending on the connection and you can even get over a gig on AC it's very fast a lot of us connected
to wireless networks here in 2022 if you have some kind of a newer device that's been around in the last I would say four or five years you're probably going to be using n and AC you'll see that when I get into the configuration of this device you can select the wireless standard you're using generally the new the standard that allows more speed more bandwidth through the line as 11b was only about 11 megabits which is very slow but back in the days you didn't had really fast internet if you go back 20 years ago
fastest internet was about four Megs 3 Megs on a DSL cable modems were 6 Megs 10 Megs so if you had 11 megabits on your Wi-Fi it was fine they are going to come with speed limitations again depending on the standards if you use an older standard like n versus AC you're going to get a slower speeds interference and attenuation so attenuation is the longer you go away from the access farther you are away from the access point the slower your speeds get attenuation sometime refers to cables the longer a network cable is the slower
the speeds get say it just takes longer for the data to Traverse that longer cable same thing here with wir us if I'm like my notebook is directly underneath this uh access point it's going to get a full uh connection with a very high speed but if my notebook is very far away from this access point it's going to be a very slow speed so you want to be closer to it all types of things can interfere with wireless signals such as a concrete wall brick walls are are major things different types of machinery and
interference can affect different kinds of Wireless standards so you don't want to get too you don't want to put too much obstacles in between it so if you have your access point on another floor and you're directly on top of it like let's say somebody's upstairs and trying to connect to this they're probably going to get less of a signal than somebody standing 20 foot away on the same floor even though it's only 10 ft up because of the the the the floor of itself to get past for the signal to get through the flooring
because there's multiple layers there sheet rock there's there's a concrete could be there is uh thick pieces of plywood and all types of floor and material okay so that's going to affect the signal the other thing here we want to talk about is how do we configure our wireless network now one of the things is we should understand is something they call the Sid the SSID the security set identifier when you click and you join a wireless network that is called The Sid so when you click and you see the wireless network name that's the
Sid okay the Sid is just basically the name of the network you want to change the Sid now I didn't change the sit on this one you're going to see that change it so you can be able to identify it and your users should be able to identified change the default password on the router the the access point uh that you're using because the default password on this I think was admin admin uh or it was admin and the password was passord so if you if you're talking good security here and you can have the
best encryption but if you have no real password on your device they'll just log into the device and change your encryption so you don't want that when you join a wireless network you must use some kind of encrypted session encrypted sessions ensures that the data that's transfering between me and my computer the data in the air is fully encrypted the there's any bad guys scanning the Airways what they could do is they can decrypt your traffic they can actually go in there and say oh this here I'm going to decrypt this traffic and I'm going
to read your data so they can steal all your information your credit card data your username and passwords to different websit so you don't want that so you want encrypt the data now how do you do that well if you leave it in an open method that's going to ensure that everyone can read your information but sometimes you can connect to open n works and then join and then it becomes an encrypted Network a captive portal is a very popular thing if you ever been to a coffee shop especially in hotels you join the network
and you get that popup screen that says welcome to Sheridan's Wi-Fi and in order to do it put your room number in put your put your uh last name in and then you can join the Wi-Fi for free or sometimes they may even charge you to say hey in order to Jo a Wi-Fi you got to passay us that's called a captive portal and that's just some form of authentication identifying you or giving you some information but what we want to do is we want to encrypt it now there are basically three main encryption protocols
that you're going to use and there is a fourth one that I'm going to add here that's not listed in your exam objectives it's called wpa3 so let's go through them the first one is wired equivalency um privacy and WEP was one of the first wireless encryption protocol that we had when we created Wireless when I remember early 2000s a lot of people had Wireless and the moment Wireless would come out and people start utilizing it they needed to be encryption so people don't steal people's data well they created WP WP was cracked almost the
moment it came out there was problems with its initialization Vector the the encrypt part parts of its encryption basically that allowed people to break into your wireless and steal your data steal the passcode to join your wireless network and nowadays it's really easy to crack in fact if you take my Security Plus class there is a video where I show you how to crack rub web we just like that in about 40 seconds there's a lab I do is a video of the entire lab where I en web here on this on this router uh
access point I connect to it I use Ki Linux and just a few commands and I show you how easy it was to crack a very big web key don't use web when web was cracked WPA came out and WPA is a much newer standard much better than web harder to crack now WPA was basically the original one was a fix of web it didn't didn't last very long as they eventually would make WPA 2 this has been around for a very long time and it's still being used widely today it utilizes a type of
encryption algorithm known as AES or the advanced encryption standard which is technically unbreakable in today's world uh WPA2 has been around for a long time 99% of us is probably utilizing it but I want to point out that there is such a thing as WPA 3 which is the upgraded version of WPA 2 so in today's world we want to make sure we're using WPA 2 and or WPA 3 so let's take a look at the configurations of a wireless network I always like to show you guys more of a Hands-On approach let's I've already
logged in to this device all right I've already logged into this device and uh here I am at this sonic wall where is my here we go so here I am at my sonic wall so I'm going to go to admin I'll put in the password I'm not going to tell you what that is that's a secret like you should never tell your password so this is this actual device this is what its interface looks like when you want to configure it now when you come to configure it I am I'm just going to go
to manage I don't want to show you the overall set so when you first log in it comes into this uh monitor interface in which case you can see how many people are connected to it you can see the throughput how much data it's sending and receiving I'm going to go to manage and I'm going to go down here to wireless and we're going to go to basic uh Set uh base settings and in here we can see that the the radio Ru so right now it is an access point it's allowing people to connect
to it and then gain an internet if I did have an internet connection connected to it the wireless setting so we're going to enable the wireless radio adapter so these antennas can work and you notice the radio mode and this is what I was telling you guys about this is going to be your wireless standard so you can see how you could select uh now there is frequency channels that I'm not going to get into in this course 2.4 and 5 GHz but you'll notice you have n g and b g a uh you have
n GB you have uh a AC only 5 GHz AC only uh this one also supports n a and AC so variety of different standards you can select depending on the channel that you want to go with uh for now I'm just going to leave it as more of a mix NGB connection if I had Wireless AC adapters in my house I would have probably just gone with the 80211 AC uh the other thing here I want to point out is the sidn name so this is the name of the network you notice that when
I want to join when I want to join the wireless network and I click on where is my wireless network here we go go you'll notice how it I joined this wireless network says sonic wall C55 notice it's the same Sid so your Sid is going to be the name of your actual Network in here I can go to security this is what we were talking about before we were talking about the encryption of the data so the authentication type you'll notice you have web you have you have open and I said you don't want
open open is basically going to allow anybody to join your network and just steal your data because your data is not encrypted anyone can just join it WEP was said was cracked and there is WPA2 so most at home we're going to use WPA2 what's not as a pre-ir key notice this one doesn't even have an option for WPA as it's not really used anymore why do we still have web well you see a lot of wireless routers access points still support web why well because web was actually is actually used on really old Legacy
devices and all Legacy devices doesn't support WPA or WPA 2 so a lot of them still have WPA uh we installed okay so you can actually go in there I'm going to put wpa3 this one does not support wpa3 I said so this on your standard and this would be a pre-ir key this is where I would put in that quote unquote Wi-Fi password you guys call it this is known as a pre-shared key that people would need to join the network so if they know that key they can click on your network and they
can put that key in but you should have at least WPA2 on it okay so this is how this is a good introduction here to wireless configuration wireless access points and things we should know about Wireless standards and how to keep them secure in this video we're going to be talking about operating systems different types of operating systems and what will the operating system do for your computer you see every time you use a computer whether it's something that's your mobile phone something as your big desktop your laptop your tablet or any B basically any
kind of device that carries a CPU in it they will require some form of an operating system now there are many different types of operating systems out there that we need to know for our exam and they're going to pH into a couple categories the first thing up we're going to have is the one you're probably using the most of is you probably spend too much time on your phone ever heard that before is your mobile operating system now mobile operating system is going to be things such as your Android operating system that you're going
to have on your Android based device like I have a Samsung device you have your iPhone Os or the basically operating system that powers up on iPhone this are going to be the two most popular uh operating system when it comes to mobile devices uh the other one here is going to be workstation oper operating systems so workstation operating systems is what you quote unquote use to get work done now at home you're probably going to have some such as Windows 10 home edition at work you're probably going to have something called Windows 10 professional
or Enterprise Edition what this is is that this these version of Windows such as Pro and Enterprise adds more functionality to be managed in a larger Network such as joining a domain um server operating system this is going to be such thing as Windows Server 2003 really old server 2000 2008 uh 2012 2016 and so on so you have all these different versions of Windows server but server operating system is not just on windows by the workstation operating system is not just on Windows you also have your Mac OS 10 that Mac users use on
their workstation other server operating systems that's not Microsoft based is going to be things like certain versions of Linux like Red Hat Linux Enterprise red hat is a famous one uh you also have have a different versions of Unix or free BSD or BSD is a very popular Unix operating system that powers up a lot of different servers that are out there so server operating system uh is going to be things they come in mostly a lot of times in variety of Windows Linux and Unix uh it's going to it's how you're going to get
these operating system for your workstations you're probably going to have mostly Windows and Mac OS 10 for your operating systems for your mobile devices you're going to use things like Android and of course if you're using that iPhone you got your iPhone OS uh embedded systems so embedded systems are basically going to be operating systems that is built into the computer that boots it up and this is not something that you're going to be installing let's say you get like an ATM machine or you get uh something like an old like a washing machine or
a brand new fridge that has operating systems built into them there's going to be embedded OS I know an ATM machine that ran an embedded version of Windows uh on there so embedded OS is basically embedded into the computer's quote unquote the RAM chips on them in other words they're not they're not really like on a hard drive the other one we have is firmware so firmware is basically going to be a bios of your computer so your bios of your computer when you put it on you can go into the Biers and change the
setting the Biers the firmware is really what's talking to that lower level hardware and your system talks to the BIOS in order to control the hardware another type is what we're going to have in cloud-based systems and if you do virtualization a hypervisor hypervisor based operating systems is something that you install on the hardware like you would on Windows and then put virtual machines on it famous things of this would be things like VMware ESX would be a famous uh hypervisor based operating system you can also download Microsoft's hyperv Standalone so what these are these
are basically operating systems that you install on your big server boxes and then you put virtual machines on them so these are some different types of os's now when you're thinking about an operating system what does the OS do well all operating systems are going to do a variety of task basically everything that's listed here that's going to include interface is the interface between the applications and the hardware so the operating system sits between all the applications we're going to be using such as your word your browser uh Excel PowerPoint and the hardware itself so
the operating system is like that middleman between the applications and the hardware it's allowing the application to utilize the hardware so let's say you're a gamer and you're playing your games your game requires direct access or good access to that video card and that heavy duty CPU and RAM that you have so what you need is you need the operating system to control that access if the operating system is giv problems you don't have the right OS maybe you have a 32-bit OS you can't access all the hardware it's going to do dis management it's
going to allow us to manage our hard drive ability to plug in a hard drive and format that hard drive it's going to have the ability to partition those Drive connect drives and access files and folders from different drives that we have that were plugged into our computers now we did review hard drives such as solid state drive and magnetic media drive such as a normal hard drive um and the operating system is going to allow us to to mount those drive and use them Process Management and scheduling so Process Management and scheduling is going
to be when we have all these different processes or tasks that we have running we can go go in and kill those tasks if needed the operating system should have the ability to stop a task let's say you open something like notepad you don't want it anymore there should be somewhere in the OS to go in and kill it right at the conclusion of this video I'm going to show you some of that uh application management the ability to install application and unin install application you probably installed a few apps on an operating system before
even if it's just your phone and then you would just hold it press on the app hold it and then say on install memory management one of the main things the operating system should be doing is managing the memory effectively now I talked about 64-bit versus 32-bit operating system as 64-bit can handle much more memory than a 32-bit one could good memory management is essential to you to correctly utilize all the ram that is in your computer now operating system is back back in the days wasn't very good at this we had to manage page
files and things like that but today they're pretty good every time you plug a device think of plugging in a mouse a speaker a keyboard into your into your uh computer the operating system is going to make sure to get those drivers you might have to install it and manage those devices another thing operating system should be doing is Access Control what this is is ability to control access to files and folders now on a corporate Network you might go to a server and try to access one of the files and the operating Sy be
like nope you don't have access to this type of information operating systems has the ability to encrypt data when I get to file formats I'll cover that and by being able to encrypt the data on the dries anybody that steals the machines or or if a hacker tries to get into the machine won't be able to get it because it's encrypted so it does do access control which is controlling the access between the users and the objects which is basically denied me access to the folder and of course encryp in the the the folders with
good encryption all right so these are going to be some of the things that we want to be familiar with with operating system when it comes to your exam be familiar that there's different types of operating system and it controls all access to the computer including managing your Hardware such as memory and all the applications that's installed in this video I'm going to be talking about file systems and features now when I talk about file systems I'm talking about the AB ility to quote unquote format a storage device such as this memory stick or an
external storage device or an internal hard drive and be able to utilize it when you when you first purchase uh a hard drive like right out the box when you first get it and you mount it into the computer you can't actually add data to it you have to first format it into a quote unquote file system that the operating system recognizes and can store data on without formatting it you can't store data now most of of these jump drives or USB sticks that we purchase already comes pre-formatted but when you purchase one of the
bigger hard drives like I showed you the one tbyte drives that I showed you in previous videos If you use one of those drives you're going to have to format it in order to use it now the way when we format it we're basically going to select a file system and depending on the file system it's going to depend where it's being used and if there's any limitations so in this video I want to briefly go over some of these file systems with you so some of the file systems that we have uh if you're
on a Windows box you're basically going to use NTFS is the default one which we're going to be using today the new technology file system is a is a file system that's been around for quite a while in the 1993's I believe NTFS allows you to have very large partitions or dis sizes and allows you to have security such as it's going to allow us to encrypt files compress files and set permissions on files so in so when you format something as NTFS it doesn't give you the option to compress it which makes the file
smaller on the drive encrypting it if when data is encrypted anybody that steals your drive and tries to access it wouldn't have the opportunity to it allows you to set permissions on the file permission so hey Bob can access it but Mary can't journaling NTFS will do this too because it's going to allow to track changes that's happening on the drive and be able to revert back so journaling just means ability to track changes certain file systems such as ntf such as fat 32 another file system format that was popular for lower versions of Windows
I think Windows 95 98 Windows uh even up to Windows XP fat 32 is pretty common but fat 32 is a file system that's highly compatible with a variety of different os's you can format something as fat 32 and use it on a Mac use it on a window but the problem with fat 32 is that it has a a lot of limit patients it doesn't support this spaces of more than 32 gigs so we can't use that here because this this is only this is 128 gigs uh so it does have a limitation of
a file of the this size of 32 gigs but it also has a limitation of the file size of only 4 gigs you can't have a file bigger than 4 gigs if you have a a DVD a Blu-ray movie that's 10 gigs you can't store it on a fat 32 so it does have limitations and some of them will follow naming rules like when you're naming a file on on that particular uh drive or that particular file system format you may not be able to use certain characters so some of them does have this so
going back here to the file system NTFS is really just a windows thing all right you can use this in Windows and this is mostly going to be used on Windows servers Windows workstations because it has compression encryption permission all on there and allows you to set security fat 32 you can use this on Windows and on Macs you can use this for it does have a lot of limitations it doesn't support anything more than 32 gigs in in phys in size and it doesn't support file size individual files of more than four gigs to
overcome these limitations they made a newer thing called xat X fat is very popular because it basically removes the limitations of fat 32 and it still allows you to Interchange between Windows and Mac if you're on a Mac machine you're probably going to have the hierarchy file system by the way fat sensor file allocation table uh the hierarchy file system is mostly going to use on your Mac OS this is generally for Mac OS extended 4 is going to be Ed on Linux OS if you have your Linux box that you're using l i n
uh let's just put Linux OS here so on your Linux OS you're going to have that extended for now what I do want to do is I want to show you what I mean by format the drive and I want to show you before I leave this video uh some limitations when you're using something as NTFS versus fat so I am going to plug this in so the desktop actually sits right on my table here and I am going to plug this uh USB stick all right you guys can see our M there um okay
so I am going to go in here to this is I'm in the explore here this is the the drive that I just plugged in there okay this is that uh lexark USB stick that I plug 128 gigs it comes out of 117 I want to show you guys something when you want to use a drive format the drive erases it and prepares it to be used to install file and folders I'm going to right click on it and I'm going to say format and you'll notice it's going to give me two formats it's going
to give me NTFS and X fat now it doesn't give me uh fat 32 because this partition this capacity is at 117 if it was under 32 or 32 it'll give you that option if I go in here and I say xat quick format I want to show you something this should it be really quick look it's formatted already so now it's an X it's an xat format of Drive how do I know it if I right click on it and I go to properties you'll see it says xat if I open this and I
create a folder test folder I'm going to right click on this and I'll go to property I want you to notice something it has three tabs General sharing and customize if I go to advance I just have compression is not checked but I can encrypt data on it but notice it's just three tab Sharon General and customized all right just watch me bear with me here so I told you that xat is the upgrade to Fat okay now watch what happens if I format this to NTFS I'm going to say herey let's format this to
NTFS now if you're using a Windows box all especially like Windows 10 all your drives are pretty much already formatted as NTFS click okay click on close here I'm going to right click on this I'm going to open this up notice by the way when you format your drive it erases everything It prepares it to be readr so don't go format and driv you're going to lose all your data let's create this test folder again I'm going to right click properties and I want you to notice a new tab pops up see now we have
a security tab now we can go in and set permissions I can go in here and say well I don't want everyone to access but I want Bob to access and not marrier only Bob alone so you can set permissions if I go into the general I go to advance you notice compression is now available and I can also encrypt it so what this is showing me is that the file system that you're using really can help determine a lot of the features that you're going to get with certain file system you're going to be
able to get things like encryption compression and security while using NTFS you may not get those in other file systems in this video I'm going to be talking about file management so when you manage a computer when you're using a computer you should be familiar with what is known as file and folders management because using a computer on a day-to-day basis you're going to generate a lot of files you're going to save pictures you're going to save music files you're going to save Word documents you might save your home homework in a text file or
something like that and you should be familiar with things such as folders also known as directories file types extensions and permissions on them so this is a quick video on this so if you ever made a folder you've done this so in this video I'm going to show you hey what's a folder and how are we going to make it then I'm going to show you file extensions and the EX file types and extensions that you should be familiar with and then the permissions of how to set them so let's go into this uh on
here and and oh you know what we'll just do it at the desktop here where am I here we go all right so I want to just create a folder so when you're looking at a desktop you go ahead you make a folder uh let's call this my homework folder so homework folder so let's say you have a folder so a folder is basically a container that's going to allow you to store files within it store folders inside of folders so if I go on here I'm going to make a folder called homework and then
I'm going to create a new folder inside of it called math homework in here I'm going to have all my math homework now in this folder when I open it you can create files so in here you can save files so let's say you're using a Microsoft Word document and uh this is homework this is math homework and I could save this if I know how to spell homework would help right so I'm going to go ahead and save this file save as go down here to browse and we're going to select the desktop where
we saved it and here we have the homework folder and here we have math and we'll say okay uh this is a math homework save so I'm going to close this out so in here you notice you saw there if I double click on this I go to math and here's that math homework document now this is basically what a folder does this is what a directory is it is a place where we are going to store files now in here you're going to have variety of file types now I have already file types put
on to see the file what's known as the extensions if I go to view okay you see right here there's something that says file name extensions this is something you're going to want to be familiar with as your career grows so if I go to file name you notice it doesn't Now by default this box is not checked so if I go in here and I check it you notice that the extension of a Microsoft Word document is d ocx as your career starts to grow you're going to become more and more familiar with the
different uh extensions that are out there for example if I make a new Excel file uh where is Excel somewhere around here you probably saw that before I did here's a new Excel file. xlsx is an Excel file if I open this this here would be an Excel IF I make a text file that would be a.txt so as your career progress you're going to have to start to learn file extension so the moment you look at a file without having icons like we have on these because sometimes you may be looking at them at
a command prompt and you're not going to see an icon so the moment you look at a command prompt you can say oh okay so that is a text file that's a Word document that's an Excel file that's a Microsoft Project file executable programs are going to be like aexe so aexe is a program an application that you're going execute you see if I go to things that I have downloaded on this machine you'll notice the wcon tablet driver we downloaded before is a.exe so that would be a file an executable program now one thing
I do want to mention to you guys is when you're setting up on larger corporate networks uh what they do is they set permissions on the file so Bob can access it but Mary can't to do that let's say you want to set permissions on your on your math folder uh maybe only you can access it so you would have to right click on it you would go to properties you would want to make sure that if you're stored on NTFS if you remember in the previous video we talked with file system format if you
don't have NTFS you can't store it so I'm going to go to security and in here you can set permissions now I'm not going to set it this is something I teach more when I teach Security Plus we'll get into this but just know you can set permissions on these folders and when Mary logs in and she tries to double click on it let's say access is denied this is mostly done on a file server that's been shared across a network by the way so the thing here I want you to get out of this
remember folders are used to store and manage files on your computers including all the folders when you have a folder in there you should be familiar as you as your career starts to progress you should become very familiar with different file extensions now your exam doesn't have a list of them that you need to know but as your career progress you're going to know docx okay that's word. XLS okay that's the Excel file that EX see that's an executable file that bat is a batch file script in file you're going to eventually learn these things
and then eventually hopefully you get up to the security part of it and you start setting permissions on folders for an operating system to stay running you're going to have to have a whole bunch of little tiny programs that's running behind it in order for it to run properly or in order for it to do all of its function an operating system is not just one giant executable file that just runs on your computer in fact it's a whole bunch of little programs that's running in the background of your computer all the time even if
you think you know your computer is not doing anything I'm not using it I'm not downloading anything I'm not on the Internet or anything it's still utilizing a ton of resources in order to keep itself running those little programs that are running more than likely is going to be a service services are basically little programs that we run in the background of our computer in order to make certain things work make the OS does its function every time time you go to file and you say print uh there is a service in the background called
The Print Spooler that controls access to all the printer if that service isn't running you can't print anything but it's not something you start or you're installed it just comes with your operating system also related to Services something called a process this is going to be a small program that's running so if you open like Microsoft Word it'll create a process with word or if you open like notepad here to process notepad sometimes these Services themselves run a variety of different process proces now the operating system will manage the drivers and I went over this
with you when we did Hardware when we install actual um when we install uh Hardware into our computer we have to install the drivers I did go over this in the hardware section one thing I am going to show you right after I'm done here is going to be Utilities in particularly the task schedule the operating system has a variety of utilities to manage itself one I showed you earlier was the the utility of device manager does have a variety of command line utilities and I want to talk to you about task scheduler this allows
you to schedule tases on your computer to run a specific time and then the last thing here we'll take a look at is interfaces anytime you use a computer there's generally two interface the graphical user interface or GUI GUI now things like Windows and Mac is famous for having really good GUI Linux on the other hand doesn't have the best gooey out there and misses a lot of functions depending on the Dr of Linux by the way so they have they're very good at their command line now Windows has a command line Mac OS has
a command line all your different versions of Linux and this even Mac technically is a Unix operating system so command line is going to be that black screen with white text so I want to show you guys a couple of uh I want to show you guys a couple of different applications that um especially like task schedule or where to find services and processes in your operating assist you better understand what I'm talking about where is my desktop so here we go with my desktop so what I'm to do is I want to show you
guys the first thing up your services so your operating system runs a lot of services to get that I'm going to right click on start I am going to go up here to computer management now this is going to take a couple seconds to open there and I'm going to go to services and applications and you see services this is all the services that windows hasn't it you see it says running this computer is not really doing I'm really just running PowerPoint and a video software um video editing software on it and you can see
all of these different services that are listed here and as your it career go on you're going to learn more about them and you're going to learn specific information on different services that are out there so the one I was talking to you guys about it's like this one the principle there and if like right now I wouldn't be able to print because the print spool is turned off now I disabled this thing for a reason in a previous class I was doing um so this is a service that you can rightclick I can go
to properties and reenable the service and automatic means that when I restart the machine is going to start and then I can go ahead in here and start the service so now I'm running a service that I have now I talked what processes processes I'm going to right click on my task bar and I'm I'm going to go to task manager this is going to show me all the processes that we're running so like right now I have Chrome open here you can see it is a process here so I can go in here and
kill this entire process I can right click and say end task and just there you go it's finished um and here are all the different processes that I'm running within the computer itself so this going to be my task manager now the other one that's mentioned in our book is something called task Schuler so I'm just going to go start typing in there but when you're looking for an app in Windows the fastest way to do it is just go to start and start typing it task scheduler this is a software that you can go
in here and you can create a task and what this does is that it's going to allow you to create a task to run at a specific time so you can have a certain application execute at a specific time and date of your choosing so let's say you want a certain executable maybe because it cleans up your operating system to run 2:00 in the morning you can go in here set this up and you can allow that task to run you leave your computer around at 2:00 in the morning so you have to be up
for it maybe it takes a long time to run the other thing that was mentioned in this presentation was guy so what you're looking at is a graphical user interface if I go to start and I say run I say run and I type CMD now you could have gone to start and type CMD I'm just so used to want to run and I press open this is the command prompt so from here you can do a variety of things like you saw me run ip config and I can run a variety of utilities on
this computer I can pretty much control most of Windows from it so that would be a command line all right very good so quite a lot here was covered Services processes drivers utilities we looked at a few and the interfaces so remember when using an operating system don't think it's just one big program it's a whole lot of programs that's running in order to keep your computer running efficiently in this video I'm going to be talking about different types of software in particularly we're going to take a look at productivity software collaboration software and business
software let's get into this so as you're using your computer on a daily basis you're basically not really using the operating system much you see operating systems are more like storage containers and ability to manage applications there really two of its main functions it stores your data for you and it's going to manage your applications as throughout the day today we interact with these applications that's what we're using so for example what are you guys using most of the time you're perbly on a web browser somewhere such as the Chrome web browser or or Firefox
web browser that you're using to surf the Internet right but there's a lot of other software that we use to do work for example productivity software so productivity software going to be things like Microsoft Word Microsoft Word standard word processing software that you can use to type documents spreadsheet software like Excel allows you to do calculations and functions on it presentation software like PowerPoint that's going to allow you to basically create an entire presentation to present the audiences like I'm doing right now uh the other one is going to be visual diagram and software like
Microsoft Vio Microsoft Vio utilizes something called stencils the like templates you're going to use to create visual diagrams I'll show you what that looks like in a second collaboration software well you have to collaborate you have to talk to folks around the world you're probably going to be using an email client like Microsoft Outlook we also have webbased email client like Gmail conferen in software you guys may have heard of Zoom or go to meetting that way you can connect and view each other's camera and have a conference with each other instant messaging software like
Facebook Instant Messenger who remembers aim very long time ago AOL Instant Message and software online workspaces similar to how you would have like Zoom software and document sharing you can do this with cloud services like Dropbox this allows you for me to create a document and then send you a copy of it or share that document other software you can have is what's called business software like database software now coming up later in the course we do have a section on databases and I'll show you a little bit of Microsoft Access that used to create
a very simple database but you do have more complex database systems like Microsoft SQL or structured query language systems project management software like Microsoft Project that's going to be used to manage a project all the different task it takes to complete a project business specific applications it's not uncommon to have a business with their own custom application here at Tia we created our own custom application to manage our schools so this is something that's very specific to your business you're only going to get in that business and then accountant software I'll show you one of
those like QuickBooks QuickBooks is very uh P powerful and popular accountant software he's going to allow you to take payments it's going to allow you to invoice your customers it's going to allow you to pay your bills and track all your account and task QuickBooks Peach Tree our popular small business accting software now I do have a few of the software here to demonstrate and it's really you know if youve used computers before it is very very basic um very basic because I'm pretty sure that all of you guys have used at some point all
of you guys have used Microsoft Word Excel PowerPoint so let's go take a look at this here let's take a look where oh here we go so the first thing up I want to show you guys is going to be let's take a look at a word processor so this is Microsoft Word right I'm pretty sure you guys are familiar with this this is where you can type type if I could spell type would be helpful type a document right and you would save this I did this already for you the other one here you
have this is a spreadsheet this is Microsoft Excel so spreadsheets allow you to run calculations and manage large data and then know big part of excel is not just storing the numbers in here but it's the ability to make a function such as a sum function and add up the numbers now this is not Excel class to teach you what I did there but this is basically a function that adds these two numbers but whatever I put in here it adds it here if I go in here and to change six continues so this would
be considered a spreadsheet the other one here I have to show you guys is your presentation software so this is creating slides like I have as I'm presenting the course to you you can go in here you can add slides make a new slide put a title add bullet points Point number one and so on and so on um the other one here we have is going to be this one I want to point out to you people have gotten questions on this one you see in the exam objectives there's something called diagramming visual diagramming
software this is Microsoft viso Microsoft Vio is a diagram and software it allows you to create what you see here things like basic Network diagram but it allows you to create like flow charts functional charts uh organizational charts and it used this by utilizing a variety of different block diagrams that you can put together when you create a good diagram you can then save it as a what they would call a stencil and you can then reuse this stencil so let's say you make a a network diagram and you save it as a stencil you
can then reuse that stencil to make a new network diagram building off of that one so you can make like a default one and then just keep adding to it as time progresses or keep changing it so that would be called a stencil is used on like a Microsoft Vio document when it came to collaboration here's your email right you guys should be using Microsoft Outlook um to send and receive emails good collaboration software another one I have here is going to be now we're going coming into business software I do have a couple I
have the this is Microsoft Project this is tracking all my task so in this one I'm setting up a network I have to purchase the equipment takes me 5 days to do that I have to remove the old equipment I have to install the new equipment and so on so this is tracking all the task and how long the project will take to get done um this is project management software this is Microsoft Project is the name of this software I also have in this one here this is QuickBooks this is one of the most
popular we have in terms of uh billing uh or accounting software in a software like this I can go in here go go to my customer center and you can manage your customers from here um now QuickBooks is also known as one of the world's most slowest software so I can go in here and I have customers here I can go in here and create invoices for these customers I can receive payments from them I can go to my vendors and receive Bill enter bills from them and pay your bills and it of course manages
all your bank account so this would be considered a banking software an accounting software the last one here we'll take a look at is going to be an a database now we're going to come back to this much more in specific when I get to database management but Microsoft Access basically allows you to manage your databases and this is going to allow me to store data it's a really simple database software that you can use to make a very simple database instead of going through something complex as SQL as you can see there are many
many software that we use when you utilizing a computer remember something an operating system doesn't really have much features you can't really sit and do much with it it's there to be that interface between the applications we're spending time with and the actual Hardware so it's managing all that Hardware all that Hardware while also managing the application is really the purpose of this but most of the time as a user we spend almost all of our time utilizing a wide variety of applications when you are install an application on a computer you have to remember
that there could be a variety of different ways to get that application installed on the machine a lot of times we just download application right off the internet we double click the executable file and we just install it on our computer now what this is known as this is known as locally installed applications now locally installed applications means that there's no network required because you could have just downloaded it and it's on the the entire application installation is on your computer or some sometimes s we can be installing it uh from a USB stick or
if you have CDs or DVDs you just install it right off there onto your computer so there's no network required it exists only to you and you alone on your computer and all the files are stored locally like on your C drive or your D drive or something so basically the application is localized to you another way of doing this is local network hosted in other words there's a network within your business or within your office where the application is stored there and you access the application from one of the servers in there internet access
is not required for this type of local network hosted application because you're not going outside your network for you to go outside the network and access it from another person's Network then you would need internet some applications are going to be Cloud hosted and you've used quite a lot of these the whole concept of like Google Maps Gmail those are full-fledged applications LinkedIn is a full-fledged application a lot of these are just hosted by a third-party provider such as Amazon or Microsoft and these are going to be internet required applications uh you will need to
subscribe to a service or at least get it for free like LinkedIn would give it to you for free but a famous business software like Salesforce wouldn't you would need to purchase that all the files are stored in the cloud and all the data stored in the cloud think about how much data you have on LinkedIn you have your resume dat data all of it your certification information that's all that data stored in the cloud if you're using something like Salesforce all of your sales data is stored in the cloud now if they decide to
close it off or you don't have access to it you don't have access to your file another thing we want to talk about that really need to know for your exam as you should expect the question on is What's called the architect models and this is how application is installed so let's say you have the application installed local Al if you have the application just on your computer and no one else can access it this is called a one tier model in other words it's just one computer there that has the application you install it
locally this is the equivalent of downloading it putting on a CD and just download installing it or having it on a CD and just using it on your computer but in bigger networks okay in bigger networks we're not going to have that in bigger networks what we're going to do we're going to eliminate this all right and bigger networks what we're going to do put back on our pen in bigger networks we are going to have a server hosting it so you have a workstation you have a server hosting the application so in that situation
you would have to go to the server to grab that application whether this is a web application or just a full-fledged client application is being hosted on the server this would now be as you can imagine a two-tier design the other one is called a three-tier design in this one that server that's hosting this application would need some kind of database this database would hold the data all the records would be stored in this database the server would then access it and you would access the server this is called as you can imagine a three-tier
design so a single teer remember it's locally installed a two-tier design is being hosted on a server three-tier design is when that server has to then go to another server to get it ENT here end is just a variable this could be means one two three even four tiers for more complex setups and it's just telling you it could be any amount of tiers needed to get the app to work when you're working at home mostly your applications are probably going to be stored locally but don't be surprised that when you go to work or
in business environments the application are generally going to be stored on some kind of server or maybe even in the cloud where you're going to need to have internet access to access it in this video I'm going to be talking about configuring your web browser the web browser is a place we probably spend most of our time on especially in today's internet age whether you're surfing social media you're doing work on something like LinkedIn or some kind of software as a platform software as a service web service like Salesforce or some kind of accounting like
QuickBooks Online in other words you're going to spend a lot of time whether you're at work at home you're just doing it for pleasure on your web browser so there are a couple things that we should be familiar with number one with you use any web browser they're going to keep a cache of all the websites that you've been to every once in a while you may want to clear that cash or clearing the history of the web browser client s side scripting there are settings that we can put in a web browser that's going
to allow us to disable certain scripts from being run sometimes you go to certain websites and they may execute a certain script on the browser to make the website work well but sometimes those scripts contains malicious software and can infect your computer in big administrative networks and big Enterprises they utilize certain software to disable that but you can also do it with local options on your computer browser add-ons you can add remove and enable and disable a variety of different extensions that you could have extensions such as very popular popup or script blockers a lot
of people install pop-up blockers and you can just go to Google and look for Popup lockers for your browser and you would install them that way when you go to a website it doesn't pop and it you don't have a bunch of popups all over the place you know people go crazy when they see popups on their machines and pop-up blockers is a great way to stop that from happening or script blockers too one good thing is Chrome now has Incognito browser every time you browse it stores every time you browse the using we browser
normally it stores everything about you it knows everything about you it knows where you've been it stores where you've been it tells all the websites who you are but in certain web browsers you're going to have Incognito or private browser what this does is that when you go out on the internet it hides who you are and nobody could see your identity on the internet so I think this is pretty cool especially when you're using it in fact something I use a lot I'll show you how to do it in a minute certificates when you
go to a website okay you should look to see if the certificate is valid and if it's not the browser is actually going to tell you we covered https if you remember from earlier in HTTPS I told you if you don't see the S at the end it's not secure but sometimes you go to a website and it is the sdn but the certificate is expired or it's not trusted this means that somebody installed their own certificate and your browser doesn't trust it if you ever see an error that says this certificate is not trusted
don't go to that website the certificate is not valid and your browser is not trusting that website so it should be valid don't make it invalid uh proxy settings proxy settings is what you're going to set on your browser in order to go through a pro proxy server now a proxy server you've probably seen this before you ever been to like a university or a business where you try to access like yahoo.com or google.com and it redirects you to a whole another website that says hey you can't go there proxy servers are used to control
internet access it used to limit websites on browsers and as technicians we sometimes configure the proxy settings I'll show you how to do that in a minute too uh compatible browsers for applications certain apps may need certain browsers back days was very popular that certain applications would only run on Internet Explorer nowadays A lot of the applications work across many the browsers but once in a while you may find an application or a website that works best in one browser over the next now there are many many browsers out there from Firefox to uh Chrome
Google Chrome Microsoft edge browser inter older style Internet Explorer Safari and so on many browsers you just have to make a choice on which one you want to use you could be on a Mac right now and be using uh Chrome when I use my Mac I use a Chrome browser I don't use a Safari browser it's more of a preference so in the rest of this video what I'm going to do is I'm going to show you a couple of settings on your browser that we just spoke about and I'm my favorite browser is
the Chrome browser so here here I have my Chrome browser I'm actually going to go to the little dot dot dot there open this up and the first thing I want to show you is incognito so this is the Incognito so when you are browsing here uh anything that I look for anything that I search for is going to be cleared it keeps you as private as possible so this is known as private brows so people can't see your activities this is good uh the other thing here I want to show you a couple of
options if you go to history and we go to history here you can see all the things I've been on YouTube here looking at the Tia channel uh you should be clearing your browser this is going to be clearing the cache on the actual browser um let's go back here to settings couple other options here that we that was mentioned uh what else where we have so let's go to extensions and extensions if you have any um third-party extensions that you downloaded maybe some pop-up blockers or anything you can go in here disable remove them
if needed uh the other one here is going to be proxy settings so we're going to go to settings and if you're a technician you're configuring a proxy for your organization you would just go to system you would click right here and then if you have it if you have it set automatically or if you want to manually enter it you can do that here too this should have to get from like your system administrator what those settings would be okay so this here are some of the settings that you can do in a browser
every browser is going to be a little different of configuration uh Edge is going to be a little different in Safari but they're all basically going to support all the different things that I spoke about when you purchase software you're going to want to make sure that you understand that licensing requirement and in this video I'm going to talk about those licensing requirement you see when you go out and you buy a software from the store for example you buy it only for you to use and it's a single use you can only install it
on one computer and you can use it on that particular machine that's called a single use software now when you purchase software like this let's say you go out and you buy a game or you buy Microsoft Office for your computer only it's basically just for one computer and it's more than likely a lot of software being sold today is what's called single platform single platform is software that can only be installed on one platform like it's only for Windows or it's only for Mac things like Microsoft Office has Office for Windows and Office for
Mac now there are some software that are crossplatform compatible in other words you can install them on Windows or Mac but this creates some compatibility sometimes installing a software on Windows and then installing that's that's the application make a makes it for the Mac it may not work as well or vice versa maybe something was made for for Macs but doesn't work too well on Windows now going back to the licenses you have a single license in other words you can install it on one machine and just one machine sometimes organizations buys what's called a
group license or a site license if they have a whether it's 10 users or 200 users in that location they can install as many times as they like only in that site or that building so if they have $10 buildings they would just buy 10 of these licenses this would probably be cheaper than buying one license for each user sometimes you want software to run multiple instances at once so I install a software and I'm using it you install a software you're using it at the same time sometimes we must purchase concurrent licenses in other
words have the software run multiple times at the same time uh open source versus proprietary when you sell software when they say open source you should notice term for your exam when they say open source the source code that onlines of software is known to the public everyone can see the source code proprietary software like Windows versus Linux Linux is the open source Windows is proprietary proprietary software no one consider source code Microsoft owns it they compile it you don't see it if you look at Windows all you see is ones and zeros you don't
see the actual codes itself open source you can see the code now open source software is generally free there's was a free version of it that you can see a lot of times vendors that have open source software they're charging you for the support and the maintenance of that software so remember with open source software you can actually edit the source code if needed this has ups and downs think about this if you have access to the source code and there's a problem you can fix it and because a lot of people can see it
there may be less errors and bugs and security flaws but it also works the opposite way if everyone can see the source code they can discover error bugs and security flaws faster than they would in Windows right so they do have they do have their ups and downs sometimes you can purchase offer one time onetime purchase like you would buy QuickBooks or $300 you're done virtues subscribing to QuickBooks and paying them $20 a month for the rest of time you would have to determine whether a one-time purchase is better than a subscription a good example
of this is Adobe Adobe Photoshop illustrator in design um Premiere and all these software that they make or thousands of or hundreds of dollars per software and then thousands for the entire Suite or you could just pick 30 bucks a month and as long as you keep paying them you can keep using them that's up to you whether you find one is better than the other it's the same software just depend how you're using it when you purchase software you're always going to get some kind of product key or serial key of the software to
run it's just a number that you're going to type in and get the software to be installed now softare installation best practices well number one a lot of times people install software you click next and you see a licen an agreement that says you agree to this I don't know if anyone have ever read that thing I know I haven't very much I don't think I've ever read a full one it's called the user ACC the user license agreement uh Ula it's called and uh you should read that to agree to what they're saying they're
going to be doing to your machine a lot of people just click I agree and click next how about if you read the instruction way too often do we install software by not reading the instructions the first thing you should do when you download or get software from the store and you want to install it read the read the directions right RTM read the manual remember that advanced options when you installing software may ask you would you like to install this would you like to configure this would you like to change this those are going
to be considered Advanced options in the software certain software has this some don't complex server software will definitely have this so as you can see installing software and buying software is not just as simple task as buying installing in the world in Corporate America there's a many options you can use whether it's a site license it's a number of license it's licens per processor per machine per server per workstation gets very complex as you can see all the different varieties and ways of purchasing and Licensing software every single piece of software that you have ever
used in your life whether it was turning on a TV or using an app on your phone was Cod Ed by someone or something and in this section of the course and in this video we're going to take a look at some of the programming languages that are out there that programmers or software developers use in order to code their software now coding is not going to be a major part of your exam but you may get a question or two on this particular topic you may have to read some if statements which I think
are pretty simple uh but there's some terminologies that you want to be familiar with maybe three or four questions on this entire section so let's get right into it and uh I'm going to be looking at different kinds of programming languages that are out there now you don't have to be a master of them or be able to identify them but you should be able to understand okay this is what an interpreted language is versus a compiled language so let's go take a look at this so right now I have a series of different kinds
of programming languages that are out there and the first one we're going to talk about is something called interpreted language interpreted language is this so when people write code line by line by line of codes I have examples of all of this I'm going to show you after this when you're write an interpreted code line by line the way the computer reads it is that it's going to read one line at a time it reads this line then it moves to the next line then it moves to the next line then it moves to the
next line those are generally what interpreted code is it doesn't have to be quote unquote compiled you see computers don't read human language it doesn't read alphabets it doesn't read ABCs and State ments what it reads is what's called machine language which is generally ones and zeros so and an interpreted code the computer reads the code line by line translates it into machine language and tells the computer what to do now in that there are two kinds of basically interpreted language you have what's called a script in language and a markup language script in language
are like JavaScript python or Ruby maybe you've heard of some of those JavaScript being incredibly popular so as python a markup language is when they use tags in order Tok mark up and tell you and tell the computer or tell the the instruction sets what to do with that particular command a markup language are things like htmls or XML now I'm going to show you guys again let me finish this slide and then I'm going to show you guys uh actual examples of what these things look like another one is called a compiled language now
compiled languages are things like C Java or C++ now compile languages what these are are basically you write them in you you write all your code it then has to execute all of it compiles all the code into one giant executable file and then it turns it into machine language and the computer to read it so it doesn't read line by line it basically turns the entire thing into machine language and then executes it so compil programming language is very famous for making giant programs like a lot of like Windows is programming C for example
another one we're going to have is what's called a query language so query language is mostly used on databases this is going to have the ability to go out and grab information from a database so database is a giant software that basically stores bulk information and a query language is what we're going to use in order to extract data manipulate data update data in a database like for example I have a structured query language or SQL the closest to machine language which is literally ones and zeros is called Assembly Language now Assembly Language isn't really
used too much in today's world it's a very complex language it's considered a very low-level language um and it's a very complex thing to learn so a lot of programmers actually don't use it it's as close as you're going to get to program in Hardware or program in the hardware to come to do a specific set of instructions now what I want to do is I want to go through some examples uh of this for you and I have a bunch of examples in it and I want to introduce you to a very popular website
that you guys should get to know and that's going to be a website called I forgot to put on my desktop this is going to be a website that was called W3 schools W3 schools is a great website if you're looking to learn coding or you're looking to get some commands going W3 schools is a great place to do because they have great tutorials and you can execute the code right there for now I just want to go through a few things here with you just to give you an idea of what these codes look
like so the first thing I spoke about well was what was called an interpreted language and here I am at JavaScript so I said JavaScript was an interpreted language and here's an example of what JavaScript looks like now don't get scared don't run away yet don't stop the video JavaScript all I want to show you is that the way the computer is going to read this is that it's going to read one line at a time so it's interpreted and it's reading this so there's an error like in this line it'll stop the code from
running so it's an interpreted language the other one I mentioned was called a markup language HTML is a markup language and you can see here they're making a table and in this table you notice all these tags open tags close tags open tag Clos so these are going to be the header of the table and these are going to be the values within the table when you execute this code when this code is executed it looks like this it turns into a table now you're pretty familiar with HTML because HTML is what powers up all
your web pages all the websites that you're going to today is in some form of HTML format with additional codes there so this by running this you would get this output the other one I spoke about was what was called a compiled language we said like C or Java or C++ here is C++ now C++ is going to be a compile language so in this one here you can see this is C++ and you know one of the most you know when you start learn programming the first thing you're going to do is output something
to a screen so here I have C++ now in order to run this code this code has to be compiled and they actually compile pil it on the website and when you run it you'll see that it'll give me the output so I'm saying output hello I am Andrew so that was the output that I'm put in there the other one that I wanted to tell you guys was what's called SQL so the structured query language so structured query language SQL what SQL does is that it extracts data from a database so in this uh
in in this example I'm showing you there's a database and in your database you have tables now we're going to come back to databases later on the class if we have a whole section on it but this is a SQL command what I'm saying is select the top three records from a table called customers so when I run this it basically gives me at the top three customers in a particular table so this what SQL languages or query language is used to extract data from particular databases or data sets we we can also say I
know coding and programming May Scare many people it's not everyone's cup of tea trust me I know it's not my cup of tea uh I don't I know how over my many years of doing it I have gone through and I've read many scripts I've written Python scripts I've manipulated javascripts I'm not the best programmer out there and you don't have to be in order to work in technology unless programming is what you do some of us like the programming some of us don't but as an IT technician you should at least understand what different
languages exist and how to read some of the scripts that you yourself may be write in in the future in this video we're going to be going over some interesting software development technique of when programmers are basically writing codes and I want to show you guys some pretty cool stuff that you're going to see on your exam and that's how to use what is called conditional statements or logic operations on code if you have ever wondered how does a computer make a decision I'll give you a brief overview of how that works because it's all
you need for your exam let's get into it so one of the things I want to mention right off the beginning is something called pseudo code pseudo code Concepts what the hell is pseudo code well pseudo code is what programmers write when they don't want to write the actual code word for word so let's say me and you are programmers and we're trying to write a program that well if the dog is Big then the dog is very nice if the dog is small then the dog is not nice you never seen no small dogs
make a lot of noise so pseudo code would look like this pseudo code would say something like if the dog is equal to Big then nice if I should be F there if not then bad that's a pseudo code I literally wrote the pseudo code for you so what the pseudo code is doing is that it's just the way programmers think it's not the actual code it doesn't have all the syntax needed it doesn't have all of the little tags that goes here and there and this and the open parentheses and closed parentheses basically all
the rules that are needed in a particular language the interesting part of pseudo code is that it's basically applied to any language whether you're going to whether this particular if statement we can use it to apply the logic we're thinking about to things like Java or JavaScript C++ Python and so on all we're doing is we're just writing out the code and easy to form easy to understand human languages that anyone can basically read so that's called pseudo code they're basically easy to read and they basically can be applied to any language and remember it's
just something you write basically on a piece of paper like I just did the other one is called a flowchart Concepts and sequence so flow chart Concepts is when programmers are writing they design little flowcharts they say say well if this happens then do this and if this happens then do this if it doesn't happen then do this there's basically creating the logic of the of the program using a variety of boxes and diagram I actually have a picture of that I'll show you that in a second the next thing we're going to be looking
at in real time is something we call logic components software has to make a decision and this is generally done with some kind of conditional statement it'll basically say something like okay if this person is doing this then you should do this if this person clicks this button then do this if this Valu is entered then do this for example if they buy this product charge a sales tax tax if they buy this product from this state charge this sales tax if they buy this product from another state charge this sales tax every piece of
software has to make some kind of decision some kind of logical operation this is mostly done with what's called an if statement uh the other things here we're going to take a look at is called branching and loopin I'll show you an example of a loop so branching is basically when you're writing the code and there's a lot of codes you're like a lot of this is using these if then statements so it's going to be like well if this is happening then jump down multiple lines of code so branching is like okay I know
there's a lot of code here but if this statement is true or false then skip down to this statement at the bottom because I don't need this code in the middle looping allows codes to be run over and over to form some kind of pattern if needed that is a variety of different Loops like f Loop and wild Loops I'll just show you an example of a fur Loop so let's get in here let's get in here to the example section uh of this so let's go back here to my desktop and the first thing
up I want to talk about is something called a fur Loop or basically a loop now you don't have to worry about all the different kind of Loops that are out there is fur Loop W Loops just know what is a loop and I'm just going to give you a brief example of one here now remember what I told you guys what exactly is a loop well a loop allows codes to be run over over and over for example here's here's something if I ever want to run if I ever wanted the code to Output
1 2 3 4 what do I need to do I would have to write a code that says output one output two output three output four or I could use a loop to tell the computer to Output as many times as as many numbers as I want in in a way that increments it so I want you guys just to I you don't have to okay just let me tell you guys something you don't have to be able to write this stuff for your exam you just have to understand what the hell it is so
I want to show you guys this is a Java okay this is done in Java we could have used JavaScript we could have used python I just use Java on this one uh so by the way I did study Java I took a Java class in college so I'm not the best at it but I understand a good set of it okay so this one here is basically going to print out so here's here's what this says it says we're going to set we're going to set the integer the integer being I itself to zero
now if the integer is less than five then increment all the way by one uh you see this i++ notice for your exams i++ means incrementing it by one when you run this code basically it's going to start at zero because it's equal to zero and it has to be less than five so you notice it goes 0 1 2 3 4 if I go in here and I say make this 10 you'll notice that now it goes 0 one0 all all the way to 9 because we're saying it has to be less than 10
but if I go in here and I say let's make it uh less than or equal to 10 now you'll get the actual 10 let's see if that executes the 10 and you know I mentioned the W3 schools website in a previous video because you can actually practice code here I remember study in Java uh for other classes and I use this a lot in demonstrations now what exactly was the Loop here you're probably saying okay this thing can output 10 well the loop allowed this code to be run over and over and over until
it hit its desired output that's what it is a loop basically allows a code to keep running over and over and over now a branch statement Branch statements a lot of these are going to be used in if then statements this allows the computer to make logical uh guess I should say or we or we can say make logical decisions if Den statements is something that is on your exam you may see one on the exam where you have to interpret the results and they're pretty easy and I'll show you guys what they are you
see if then statements is basically if this happens so if I am less than 200 PB then I am overweight I'm sorry if I am less than 200 lound then I am healthy weight if I'm over then I am overweight a computer will consistently make decisions and sometimes it has multiple if statements or multiple characteristics of the statements like it can do well if he's between this weight and this weight he's healthy if he's between this weight and this weight he's overweight if he's between this weight and this weight he is obese so this can
get very complex you don't need to know that for your exam but I do want to show you one of these statements where is our desktop here we go uh so I want you take a look at this this is basically an if statement look at this statement and I'm just going to read it for you again this is in Java you should be able to read this now I could have written this in pseudo code and made it easy for you but I written I'm showing you the actual Java code so if you ever
see this in real life you'll be able to understand it and then the exam will be a lot easier so look at the statement they're setting the integer of time is 12 so the value here is 12 they're saying that if the time is less than 10 now the way an if statement works the next part of it is generally going to be the true part so it says if the statement specify block of code is executed then this true so the condition and then the true part of it okay that's that's something you have
to remember so if this condition if time is Le less than 10 then output this this is the true part if not or if else if else is basically going to say well okay if it's not that that then then what it is okay then do this so then if it is less than 20 I'll put good day and this is the complete false part now if not everything else is just good evening so let's see this you see if I go in here now and I say the integer of time let's say is five
well five is less than 10 so it should return good morning let's see if that's correct good morning but it's also saying what well else if the time is less than 20 then good day so if we go in here we say let's say uh 15 let's see what it says I know this takes a while it always it's it's never the fastest thing on this website okay so we saying okay so that's executing this statement so it's less than 20 but it is greater than 10 now let's say time is 30 so we're saying
now it's out of the range of less than 10 less than 20 so what is it going to tell us it's good evening so this is the complete false section of it I don't need you guys to be able to write these types of code but you should be able to understand these types of statements if statements are used in a variety of different things whether you're looking at JavaScript you're and JavaScript is something we use quite a lot of especially Python scripts is something we use a lot of an it in fact many many
type of automation software are scripted it automation like configuring a router configure a server is scripted and a lot of them will use these kinds of conditional statements or branching statements in order for the systems to be fully automated in this video we're going to be taking a look at some programming Concepts that you might see show up on your exam just a few terms here that we just want to quickly review the first thing I I want to review is something as identifier so all the different values that you're going to be entering into
aod whether it's typing in a date adding a price selecting an item for example on an e-commerce site uh there's going to be somewhere to store this data in the computer's memory now there's two ways of doing this we have variables and constants a variable is a data items whose value can't change during the program execution versus a constant is the data items whose values cannot change during the execution so constants will stay exactly the same versus a variable can change as the program is being executed we're also going to take a look at a
container uh containers will hold these values that you have now in those values you're going to have something called an array or a vector uh vectors are basically going to be a dynamic array an array is going to hold a list of different variables now you're probably saying Andrew what the hell are you talking about I decided the best way to show this to you the best way to explain it to you is actually show it to you what it looks like uh so here I am I'm back here at the W3 schools and I
want to show you something if in in the normal programming world what you're going to have is variables and you can see that they're saying that car one is a variable car two they're set the VAR so anytime the program references car one they know they're talking about itself anytime it references Car 2 they're talking about a Volvo so this here now if you want to call car one car 2 you could literally just write this entire code out so let's say you have 15 different cars you can write 15 different lines car three car
four car five equals this car 5 equals this car six equals this car 7 equals this this you're going to keep you're going to keep what's called declaring the variable over and over the easiest way to do this would actually be just to create an array so in the array you're going to say that that cars this is an array is Saab Volvo and BMW so when they call the array or they extract data from the array they can call any of these variables so a container is a way to store these particular data now
the other one here was called a vector and a vector is basically a dynamic array it's it's an array that can change be manipulated it size basically can be changed all right these are some basic programming concept you might see on your exam in this video I'm going to look at a few more programming Concepts before we leave this section and that's going to be something called functions and object-oriented programming I want to give you some basic definitions of this and we're going to start by taking a look at a function so what exactly are
functions well in software develop sometimes programmers just makes up their own particular sometimes mathematical functions that they want to calculate at certain times so instead of using what's there or having to recall certain programming codes they just make up their own functions and in this section I want to show you what that looks like as I have one that I made so here is a function that I made and this is done using JavaScript so you can create your own function in JavaScript by literally using the function so the script is called function I created
a function it's called Andrew you what in this one I'll just call it Andy it's called The Andy function what the Andy function is that is that it has two variables p and P2 and basically what this function does is that it's going to multiply these two numbers so anytime I am going to run this function it's not Android anymore it's Andy anytime I run the Andy function I have to give it two numbers and it's going to just basically multiply these two numbers so if I go in here and I say this is let's
say five and this is 20 then to run this function I get 100 now anytime the function is called so if I'm coding the software I'm coding the software every time I need to multiply two numbers I don't have to write it out all I have to do is say Andy give it and give it the the two numbers and boom it calculates it because it knows that this function is basically going to multiply the two numbers within the brackets within the parentheses themselves so this function is something that we can reuse over and over
and over now when it comes to reusing code over and over there's a class of programming that you should be familiar with and that's called uh objectoriented programming the most famous one of this is going to be like Java what it is is that instead of having code that instead of rewriting code so let's say you're programming a piece of software and every time you want to print you have to write out a code function for print in in object oriented programming basically you write blocks of code store them as object and then you can
call the object back when you do this there's two things you should be familiar with something called properties and methods so properties is basically the variables within the function let's say you have a cat for example the cat has two eyes it has four legs and it has a tail that would be the properties let's say that's your object the cat and and it has fur so that that would be your object now methods is what can you do with this particular object well this object method should be like it can run it can jump
it can eat and it can save meow that would be methods so methods is basically how you're going to be using these objects and the properties is what the objects are about don't expect a ton of questions on this topic but as you work through your it career you should be familiar with some of these terms in this video I'm going to be going over databases so if you have ever used any application before that pulls up data or stores your information that's being stored in some kind of database a database is basically a a
piece of software that does what it says it does it stores data it's a base of giant amount of data almost every software you buy so are used so if you go to Amazon right now Amazon has a giant database of all the different products that it sells it also has a giant database of customers information if you go to Hotmail it has a giant database of all the emails you receive and all the user accounts so all software basically that we use has some kind of database that powers it up a lot of times
the database is separate from the application software so the database is stored on one server and the application is stored on another end so what's known as the front end and the back end so if you ever hear from front end and backend front end is just the application interface itself and the backend is where the data is actually stored a lot of times these two are even separate tasks as the application programmers programs the application front end makes user interface does all the code and database administrators makes the database to store the data in
all the fields and all the records that the data will have the application will then utilize the database to present a nice beautiful front end like you would have on amazon.com so what I did in this video is I actually made a database and I actually want to show you a really simple database using a relational database called Microsoft Access which is a very simple database software to use and you'll see that in a few minutes now you don't need to know how to make a database you don't need to know how to write SQL
commands for this exam but what you should do is understand hey this is a database and just some characteristics about it so the first thing we going to take a look at is what is the usage of a database well we want to be able to First create databases there's a wide variety of database software that are out there from something as simple as Microsoft Access to complexity of Microsoft SQL or you guys probably heard of Oracle uh that's also very famous MySQL um no SQL and a variety of different databases that are out there
so we're going to take a look at all of these different things in this section but what a database is basically going to do is allow me to store data it stores data in what is known as tables and I'll show you that in a minute we can input we can import data from other databases or data sources or we can type it in ourself once the data is in the database you can then query the database and extract useful information from the actual database itself reports are then able to display information that the database
has given us all information stored in a database are called records records are the individual data sets so for example in Amazon right now your your record would be your first name your last name your address your credit card information the a record of the product would be the product name the product price when the product is available for ship so records are the individual data sets that are there databases are stored on large servers uh a database can be something that's a few megabytes all the way up to terabytes of data for giant data
sets so you're going to need massive storage and of course the bigger database the more processing it requires now databases there's a variety of them you could store instead of having a specialized piece of software to store your data such as a database some people store them in flat files this is going to be like storing data in a text file it's probably not the best option as it may not allow multiple people to use it at any given point think about this when you go to Amazon there's millions of users using that database at
any given moment it's not scalable text files as they become bigger they become slower to work with and adding data just becomes cumbersome so a database will give you good speed good scalability and allows a lot of users to use it and it can store a wide variety of data versus its flat text file that won't so let's take a look at everything I just covered in a easy to understand format and what I'm going to do here is I'm going to show you guys m Microsoft Access you don't need to know Microsoft Access for
your exam at all okay this is just a demonstration to make you get an understanding of what it is so this is Microsoft Access it's access 2019 and in Microsoft Access it has tables remember something for your exam when you store data in a database it's stored in the tables so right now I have two tables this database is very simple this database is a database of students on what class they took it's a very simple database so I have a table for my student and you notice my database has a table with it has
a table and has two students Bob and Bob and Mary so Bob Jones is student number one Mary is student number two this is their address this is their age these are called records okay these are the records within the database so I can go in and add a new record let's add a record for Chris so Chris let's say his last name is Ram like me his address is 333 Street and can't spell street now that's fine uh Chris is 18 so we just added a brand new record into our database now all databases
has tables that's where the data is stored you can continuously type and type then you see how it's storing this information for me now you're thinking to yourself hey doesn't this look like Excel it kind of does look like Excel but it's vastly this is not a spreadsheet where you can just execute formulas on this is just a place to type information in there so this is where you would store the data another good part about this is that you see if I go into this one here I can show classes that was taken by
some of my students remember student one was who student one was Bob this is student one his ID is number one and Mary was two so if I go into class table I can see student number one student I id1 took Excel and Word student number two took PowerPoint one good thing about a database is that it allows you to query the data extract useful information so I have a query right here you see if I open let's close this table close this table if I open this query right here you can see it's telling
me that Bob took Excel Bob took word and Mary took PowerPoint it's given me that useful information that I want out of a database it's great to have data but if you can extracting CD information it's not very useful the other thing here I have is a report so if I go here to reports I can double click on this and I can see a nice display of all the students that took information from took classes from us and you can see it's a nice printable format um and it looks good so I can go
to print preview and this is what it would look like if it prints out so this would be considered a report now if you're wondering so this is a database and what's a flat file well a flat file is basically like a text document like this so this is just data in a flat file it's not very scalable it's not fast it can get cumbersome to use you don't want to store data in flat files although a lot of data in today's world especially in specialized application is still stored in flat files okay this is
a brief introduction to databases let's keep going I'm going to show you more information and some more complexity within this database in this video I'm going to be talking about different structures of data databases that you should be familiar with for your exam and predominantly we're going to be talking about relational databases as those are the most popular ones you probably heard of things like Oracle MySQL Microsoft SQL and I just showed you Microsoft Access in the previous video so let's get into it so when it comes to relational databases there's a few components that
you want to be familiar with something called the schema now the schema of the database is basically going to be the actual layout the design of the database the tables we mentioned is where you're going to store the actual data in the database so we store data in tables and tables is made up of what is known as rows and columns or records and Fields and I'll show you guys that in a few minutes and then constraints there are certain constraints that we can apply to a database that's basically going to limit the type of
data that we want to input for example you may have a A feeli in the database where there's phone numbers and you don't want anybody typing letters in there or you have a field that has numbers it's like someone's age and you don't want somebody putting in the ABCs in there so what I'm going to do here is I am going to show you guys uh I am going to show you guys where is my database I'm going to show you guys Microsoft Access that I have here now in Microsoft Access what we're going to
have is basically a relational database and I want to show you guys these tables so if I open up the student table you see first name last name and address so first name last name and address all of this here would be considered Fields if we go Bob Mary and Chris those would be considered records so we have fields and Records now in a database in order for the database to uniquely identify every single record that is out there it needs to have a very unique feel and that field is called a primary key you
see if I look at the design of this database so I'm going to click on this here this is called design view this is the design of the when I'm making the table this is what it looks like you'll notice that next to the ID field is's a little key there you guys see that it's hard to see that it's a tiny little key there that specifies that this field is known as the primary key now the primary key is a unique field that identifies each record in that table every table should have that so
look if I go in here and then this one for me is an automatically generate a number so if I go in here and I add Tom and so Tom Hanks lives on 555 Street you notice how it automatically added this in here you can't have repeated numbers and these numbers are unique are unique to that record you can't have two two people with the same primary key or two records with the same primary key as it uniquely identifies those particular records it's like when the databases when the United States government is ready to call
you they don't call you by your name they call you by social security number when the database is call calling Tom Hanks it's not going to call Tom Hanks The Record it's going to call the number five it knows okay that's Tom Hanks so you can't have a repeated value there one of the things that people should understand about a relational database is that it's called relational for a reason because the data is actually related to each other and uh the tables are related and I want to show you something they call the schema of
the database I'm going to go to database tools I go to relationships and this is basically the schema of the dat database this shows me that there's two tables you have a student table and we have a class table and this is what's known as a one to many relationship so one student can take many classes and they're basically relating this primary key the student ID that I showed you to a student ID field in the class table this is known as a f key this student ID in the other table and the primary key
is the one in the student table so to better illustrate this you see if I go into the class table and I add so Tom Hanks is what number five right so let's say Tom Hanks took an Excel class let just put this day uh he was number five so I can just put that in there notice this student ID is not a primary key on this table it's the foreign key of the of the relationship between students and classes so that's the difference between P primary keys and foreign Keys um the next thing we
want to talk is constraints so you notice that this age this age field here if I come in here and I didn't put one for Tom Hanks but what if I put ABC or ABV it doesn't take it it's like hey this field only accept let's say he is 50 it only accept numbers so there are constraints that we can apply in this now when you're looking at these kinds of relational databases they can get a lot more complex the good thing about Microsoft Access it's very easy to use you don't have to use database
commands which I'll show you in the next video there are database commands are known as SQL commands used to manipulate the database but in in Microsoft Access it's doing it for you it's writing all the commands in the back end to create that database for you uh the other term here I want to mention in this video is going to be uh structured versus semi-structured versus non-structure when data is stored in a database it is somewhat it's structured and depending on the database it could be semi-structured in other are semi-structured is the data has tags
it has fields in it non-structured data is everything else if on your computer right now you have pictures you have text files all over the place you have emails uh stored on your on your email system you have music file and movie files this is data on your computer that doesn't really belong anywhere it's just there and this is called non-structured Data so that type of information would be considered non-structured data other types of databases we have here is going to be known as key value and documented database let's take a look at what these
are so one of the most popular implementation one of the most popular implementation of these databases are called No SQL all right no SQL now I'm not going to get too much into that but I do want to show you key value pair databases so a key value database basically it's less it's not relational it's basically data that is stored in what is known as a key value pair and oops this is AWS and this is an examp example of it it's just storing data it's saying okay this is basically a primary key and here's
the data that's assigned to it key value paer is very popular because it allows you to extract data very fast another one is called a documented database documented database basically stores data as documents quote unquote but they use a specific for example a specific one adjacent file so this here would be like a document that's stored in adjacent file and Json by is so JavaScript object notation and it's able to extract and retrieve data from this so there are a variety of different databases that are out there the most common one you're probably going to
coun is a relational database although we have things like nosql databases that are becoming popular such as those key value systems But as time is moving on relational database are still the most popular in this video I'm going to be taking a look at SQL commands now anytime you use a SQL database any type of SQL database whether it's MySQL Ms SQL Microsoft Access there's actual commands that you have to put in there to make it work your prodct you didn't put any command when you use the Microsoft axis because it actually writes the commands
for you that's more of a utility with the Microsoft Access has a beautiful interface that makes it really easy to use and create tables but in actuality there are actual SQL commands that are being run for your exam you should be familiar with some of these commands I'll start out right here at the bottom the data definition well this this is going to be about manipulating the actual database file itself for example the create would allow you to either create an entire brand new database or it can also be to create a brand new table
in that database alter it would be able to alter a table so for example you may have a table with three columns but you want to add another four or five columns to it drop you can delete a table or you can delete an entire database using the drop command permission would be used to edit permission on the database so this guy can have access but that group can't or that group code and this guy can't now when you're actually using the tables themselves and adding a removing data you're going to be using these commands
here at the top select will be able to extract data or select certain records from a particular table uh insert will be able to add records to a table if you remember we had add Tom Hanks to that table that's the insert command the delete will be able to delete a record in a table and up update will be able to update a record such as if we go in and we want to change Tom hanks's address or his age delete if you want to delete the entire Tom Hanks record insert is maybe we want
to add Tom Cruz now to our database and select would be to extract or just pull certain information from our database I actually want to show you guys I want to show you guys a couple of these commands here that that is working so look I have the drop command so we said drop table uh you can also drop the entire database this one here would be used to drop delete an entire database but I'll show you guys here drop table so I'm going to run this try this myself you notice that we have um
so you notice that we have a couple of tables here we have shippers suppliers products if I run this command called drop table look what happens you see shippers is uh shippers is right if I run it you'll not the shippers is gone it's not there all right why because it just deleted it so when you run that command it deletes that particular table the other one here I'll show you guys is what's called a select statement so this is was one of the ones I said you can use to grab data from a database
so let's try this one so in this one we have a table so this one is select the customer name and the City from customers so if we look at the customer table we have the first name their contact the address but if I run this command run SQL oh hold on one second let me restore this if I say run so I just want the customer name of the city this time so when I run this now I only get these two uh these two Fields so the select is able to extract certain data
you want from that particular database um there's a the other commands here you need to understand what they are you don't need to go about and being able to write them or even do what I just did there I just did that so you have an easier understanding of what these are now when it comes to managing these relational databases you have to understand access methods we have what's called director manual access this is when a programmer sits in front of the actual database itself the database software and sends commands directly to the database saying
hey create this table using the create command drop this table or delete this database you have programming methods in which case you have software and this is more than likely how you're going to access dat dat bases you have software like a website anytime you go to a website and you let's say you go right now to Amazon you create a brand new user you create a new account to buy something it's an insert command being sent to the database so that would be a programming way databases have a variety of interfaces like I use
Microsoft Access interface there's a variety of different interfaces like if you use Microsoft SQL Studio you'll be able to access database create tables using something similar to how I used in Access and you can also build reports from there there now export um export and import sometimes you dump the entire database to like a flat file or to another database that would be called a database dump this is exporting the database sometimes we import data from other databases also a backup I'm not sure what to tell you here other than you must have a backup
you know there's an all saying an it no backup no restore it's not if your system will die it's when it will die make sure you always have a back backup now backups can range from something as simple as just copying it to another hard drive or an external hard drive to complexity as storing it in the cloud and dependent on incremental or differential backup which you'll learn about in another course but the point is you must back up your database because if you ever lose your database you're going to lose all of your data
in this video we're going to be talking about the CIA and no not the Central Intelligence Agency but it security CIA which is something you're going to hear a lot a lot of us your it career progresses in the world of cyber security CIA stands for confidentiality integrity and availability it's the Pinnacle of all security it is what we try to accomplish it's the main goal of security keep data confidential keep it from being altered in any malicious way integrity and making sure the data is available when needed so in this video I'm going to
be going through the definitions of these terms and some attacks against them and it's really important that you know these terms and the attacks for your exam now it security is of course a a RedHot Topic in today's world you should expect a good portion of your exam if not one in five questions I think this is 20 or 22% of your exam so expect a good set of questions from this section so let's get right into it so the CIA confidentiality integrity and availability let's start off with the first one of confidentiality confidentiality is
really keeping private data private only authorized subjects should have access to the data subjects versus objects subjects are users objects are basically things they're trying to access for example file and folders subjects are you logging into Amazon website the object you're trying to access is that true that you're taking a look at confidentiality is to ensure that only the authorized subjects has access to the authorized objects so for example only you should have access to your account information only you should have access to this file on the server only people only the people in the
accounting department should have access to the accounting database so that's these are all examples of where confidentiality is needed most of the time when people are thinking confidentiality they're thinking privacy they're thinking oh that's my data and only I should have access in fact most of the time when you guys think of security you're probably thinking confidentiality now there are some attacks against confidentiality that we should be familiar with the first one is snooping or ears dropping now snooping and E dropping is basically listening to conversations as data is going by the network hackers can
listen in sniff the data sniffing sniff the data and then if the data is not encrypted they'll be able to read that data in front of them snoopin can be things like you're typing data on your keyboard and somebody's behind you and they're watching you type data on your keyboard you may type in in some sensitive information go to Amazon right now type in a type in your credit card and I'm standing behind you I can basically steal all of your credit card information another one is called wir tapping so wir tapping is basically listening
to your conversation wiretapping they do this to phones so if the government suspects you of doing some crime they may wiretap your phone and listen to your conversation this is an unauthorized entity listening to your conversation some people may wiretap you for illegal reasons sometimes you may have a jealous boyfriend or girlfriend that wiretap your phone and is listening to your conversation and you don't even know about it that would be an illegal version of wiretapping social engineering is a giant topic social engineering for your exam just remember it's more humans trying to hack or
steal data from humans social engineering is somebody manipulating you into giving them a password let's say I call you up from the help I call you up and I say hey I'm Bob from the help desk and I'm trying to reset your password can you give me your password um or can you give me your password to install a new update it's them somebody calling you over the phone and say well we're calling from American Express and your card has been hacked let me have your credit card number to verify that you are the the
person uh it's me calling you from Social Security Administration and telling you that something is wrong with social security number let me have it so social engineering is manipulating people actual emotions it's manipulating people themselves to gain data all types of subsets of this would be like fishing emails not with an F with a p fishing with a p and in this particular one they would send you an email to click on a link to go to a banking website to reset your password and then would steal it or put your credit card number in
dumpster diving people still do this dumpster div is going through the actual trash going through somebody's uh trash that they put in front of their house and get data from it for example people may not shred they should be shredding bank statements and credit card statements so what happens is they put it in the garbage they go away and before you know somebody's stealing that information somebody opens up your trash what can they find Integrity Integrity is the unauthorized manipulation of data anytime you think Integrity think alteration of information remember that word integrity is alteration
one attack that we should be familiar with against Integrity is what is known as a man in middle are now called on path of that so here's the thing with Integrity Integrity is when I send you data you're 100% sure that data wasn't manipulated when you send data your credit card number to Amazon no one intercepted the data and changed your credit card numbers when Amazon is sending you back information same concept no one intercepted the data so that means that let's say there is the Amazon webs server and there is you a user so
Amazon web server and you and you're sending data back and forth but what if right here there is a hacker what if there's a hacker there and that hacker is listening to all of the conversation this on path attack is basically listening and could manipulate the data on path which means the data is on path from Amazon to you or you to Amazon so these kinds of attack would generally be fixed by generally just encrypting your data a replay attack so a replay attack is going to be similar to this a replay attack is when
you authenticate to Amazon it authenticates you and it saves what's called a token that token lets Amazon know okay we got his password um he's all good and it gets you back a token so you can keep using this to keep accessing Amazon but what if the hacker grabs the token and it can then replay it against Amazon so when you go away it replays it as Amazon it says hey I'm I'm Bob and let's say let's say your name is Bob and then Amazon is like oh really okay Bob keep coming keep shopping and
it's interesting because what happens here is that you actually don't know that somebody logged into your account replay attack this forms a type of impersonation in other words they're impersonating you and stealing your information unauthorized information alteration somebody logs into a to a web server somebody logs into a file server manipulates a file that you shouldn't have access to this is lack of Access Control by the administrator availability is the data available in a timely timely and efficient manner in the world of security a lot of people don't look at don't look at availability as
an important concept but it is because it doesn't matter how much security you have how much good confidentiality Integrity inovative uh Integrity you have if people don't have access to the information it's not very useful to them so we have to put things in place to ensure the data is always available to them remember if the company doesn't have access to the data they can't actually do their work so what can cause problems well what happens if there's a power outage in your part of the country no one can access anything you might need to
put in UPS's on aable power supplies big batteries so if the powers does go down have multiple power providers gener generators Hardware failure there's a server with the hard drive died oh well if the hard drive is dead then no one can access the machine you should have redundancy built in here denial of service is an important one for your exam denial of service is when hackers don't want you to access a website what they do is they send loads of false traffic to a website let's say you have a small web server with important
data hackers would then send thousands and thousands or millions and millions of requests against the webs the web server drops because there's too much request no one can access it the hacker group Anonymous is famous for this they flood your web server with traffic and before you know it no one can access so it's denying the service of your website to others hinted name deny a service destruction somebody coming in destroying machines or destroying data would make it unavailable service outages what happens if your internet service goes out then no one can access anything in
the organization and if you own servers then no one can get to your servers these are going to be some of the important Concepts that we need to know for exam you want to be able to understand CIA confidentiality Integrity innovability now I can expand these topics greatly as your as your knowledge of security grows and your understanding of it and all the great things that we do in security such as ethical hacking uh you're going to enjoy this field I hope that many of you continue in this field as security and join me for
classes such as certified ethical hacker where I'll show you how to actually conduct some of these attacks and maybe some of you will become pentesters maybe some of you become security analysts or firewall administrators to me security is the most exciting part of this industry in this video I'm going to be going through some device practices or best security practices that you guys should be following when using a computer and all users should be following now some of these are going to be pretty much common sense and you're probably heard of set of them before
but we're going to iterate them because they may be showing up on your exam let's go take a look at it so let's get into it the first thing up is you want to secure your actual desktop your mobile workstation let's say you have a laptop let's say you have a desktop at work what are some things that we should be doing to secure them the first thing is we want to have antivirus installed on our machines that's out a beer minimum some kind of antimalware software so what are examples of this this is going
to things like Norton Internet Security Maca Windows comes with Windows Defender that's you should have on your computer you never know when you click on the wrong file or you open the wrong email and your machine might get infected sometimes we just go to websites that we aren't too sure about and they try to inject malware into our computer another thing we want to have is a firewall on our machine so your computer has ports it has 65,000 logical plus ports and what can happen is malware can get in a firewall would block those ports
up and stop malware from getting into your machine now if you're using a Windows box they all come with firewalls they also all come with anti-malware Windows Defender is an anti-malware and a firewall that stops things from coming in and infecting and destroying your computer changing default password you guys would be surprised to know how many hacks are done because no one changed the password so when you buy a device out the box for example I remember buying wireless routers back in the early 2000 like a linkis router and the password would be the username
admin password admin uh printers username admin password password so popular sometimes you're just trying to hack in or hacker trying to hack into a device and you just try a default password and it works because the administrator didn't change the default password you want to enable passwords for example on your wireless network I should you want to enable some kind of key on there you want to put a password on it if the system can take one you should have one for example on your phone do you have a password or a passcode setup or
can they just put it on and they can access your data that would be terrible You' want to make sure you have that on there safe browsing practices what are you going to do with safe browsing practices as a user we have to know where to go you have to be clicking on trusted websites you have to understand things things like if the browser says the site's not trusted don't go don't surf the Internet and click on random links know where that link is taking you know the website you're going to when people sends you
link don't click on links the number one way to get a virus is through the internet and it's through emails um way too often we go down rabbit holes where we click on this link you click on this link and before you know it you're 20 links in you don't even know where you are going to forums and reading people's comments and saying oh this is great you click on it you get your machine infected with malware users shouldn't do that one of the main things we can do is update our computer we should set
our machines to do automatic updates now all of these things here by the way it's in A+ I'll walk you through the steps of installing these things and setting up passwords for this exam you just need to know what you should be doing so understand this about an operating system when Microsoft or apple makes a product an operating system they they write all this code and they send it to you as time moves on people find holes in the code they find literally okay this is this is a hole that we can inject malware through
okay so it's a hole so worm comes through the hole if you want to remove the hole even if you install and you put a firewall the hole is still here if you put antivirus the worm gets in or the malware gets in and then the virus cleans it but if you want to get rid of the hole completely Boom the hole is done you have to patch your machine patching automatic patching an update in machine is it security 101 it's security you must do that way too often do I see people don't enable automatic
updates because they said oh it's too long or it's a pain to do if you want to keep your information secure and your system secure make sure to put patch in or updates on now when you're using your device okay you're you know this could be your laptop this could be your your phone there's some best practices here we want to do number one software sourcing when you get software when you download software for example to your mobile phone where are you getting that from is it from a legitimate Source did you validate that source
to be a legitimate there's a lot of apps that might be out there people sending you links to apps did it come from a legitimate Source did you research where that app came from is it from an oem website or a third party website is it from the manufacturer or is it coming from some other manufacturer for example if you're using a driver you want to install a driver to make a pro to make a hardware work remember what drivers do to make the hardware work where did you get the driver from did you go
to the manufacturer's website and download the driver or did you actually go and get some thirdparty driver to install there's third- party drivers may be a virus always get it from the original equipment manufacturers OEM website research where you're getting your software just don't install randomized software anytime you get a computer I do this all the time computer or phone or whatever the first thing I do before I install anything is I'm going to remove what's called bloat wear know that ter for your exam bloat wear is all the unnecessary software that phone manufacturers and
desktop manufacturers like Dell install on your computer first thing I do is I go to control panel I open up the thing and I start uninstalling everything we want to remove unnecessary software all right they may be a ton of unwanted unnecessary software that's just not there antiviruses with small licenses that I don't need I prefer just to use Defender when you want to remove malicious software you're going to need some kind of malicious software removal like antivirus antimalware like Windows Defender or NN Internet Security for that having these types of software like internet security
is critical for the protection of your machine because you never know when your machine might be infected remember something guys if they ever infect your machine they can manipulate the data and of course steal the data and make your life a miserable hell one of the biggest topics in it Security today is privacy privacy is a giant topic and it's a topic that's talked about so much as more and more of us utilize the innerwebs in order to for for pleasure or do business transaction we are basically giving away our data and this becomes an
issue many people are hooked to things like social media in which case they're posting on Facebook or LinkedIn or they're watching things like Tik Tok and giving away their what type of data that they're using or watching privacy is a big concern in today's world and when we're looking at privacy we we got to have some good expectations of it first of all on the internet when you're taking a look at the internet and you're using things like social media sites if you're using things like social media sites there something you must understand about it
this is going to sound harsh really harsh and I don't want to upset you or make you or make you feel bad that I always tell people this people complain about using Facebook now I'm assuming you all know what Facebook is using Facebook uh on other social media sites or Twitter in which case I'm not sure if you know this but people like Facebook resell your data so when you use Facebook and you post and you like things Facebook knows okay he likes this she likes this he likes this she doesn't like this and they
start to display ad they're selling your data they're selling your information to advertisers so they can advertise and hopefully sell you something on their website so what is Facebook doing Facebook is selling your information Facebook is selling your activity across their platform now people complain about this and I tell people this I said listen guys yes Facebook is a social media sit that resells your information but always remember how much did you pay to use Facebook Facebook is a free service to us and always remember this is the harsh part if you're not paying for
it you're the product means they're selling your activities they're selling your data so if you're not paying for it then something you're doing is the actual product itself Facebook is a giant operation that needs to pay its bills they have giant data centers and they employ tens of thousands of people and somebody's got to pay them and you're going to be pay and you're paying for it with your information that's the expectation when using social media sites we want to educate people on this we want to educate people don't post stuff on Facebook that's private
to them it can go to the world so things like that needs to be known email on the on the internet of course you're going to be using email you shouldn't be sharing information email by its native form it's not encrypted file sharing a lot of people may be downloading illegal files and instant messaging be careful who you talk to with instant messenging because if there's something instant messenger it can easily be impersonated somebody can claim to be someone someone else and you're not sure if that's the right person when it comes to privacy mobile
application especially can be grabbing your private data without you knowing a lot of times we install mobile applications and the the end user license or the user access license that's on there when you click I agree can actually be telling you that that that hey we need to look at your GPS and know where you are we need to grab your information from your phone and your contact information you want to make sure that you read these information before actually saying I agree to it that's going to be the same with desktop software business software
also corporate networks can grab a lot of the information now corporate networks is a whole different bu game when you sit down in a corporate Network the employer has the ability to monitor your phone call monitor everything you do on your computer from reading your emails to looking at your screen to tapping your phone it's fully legal if you knew about it now a lot of us may go to work in a big company where they give you something like an employee manual which list all what they're doing you never read it you signed off
I agreed to it and you just started the job and it's fully legal for the employer to do it because you agreed to it you just didn't even know about it that's why it's important to read those employee manual in the organizations you're going to have policies and procedures no I've never went for a company that just didn't have policies and procedures that's going to tell them how they're going to handle Pol how they're going to have handle privacy the organization should have policy written for example if they're going to be checking your email or
wir tapping your phone they should have written policies of how they're going to secure your private data don't forget the organization got your Social Security number they got your name and your address and all that good stuff they should have policies protecting that kind of information now when it comes to handling of confidential information passwords should always stay in an encrypted what's called hash format so no one can get it don't ever share your password with people Common Sense 101 never tell anyone your password under any circumstance no one needs to know it but you
your personal information should be encrypted companies that stores them such as Facebook such as your your Corporate Offices should be encrypting your personal information personal information is going to be things like your credit card number your height your weight your name your address even your health information one term that you might see show up on your exam is something called pii or Phi Pi is personally identifiable info your name your address your phone number your your email address personal health information Phi diseases you may have medications you may take it's going to be Phi these
a bold private information that needs to be encrypted and protected by the organizations that collects that customer information that we get from our customers like Amazon grab my name my address my credit card number should be encrypted companies confidential information this one here companies store a lot of research and development that new iPhone that's coming out that we haven't heard about yet that new phone Samsung is making that new car Ford is making company's confidential information needs to be encrypted and protected the company is going to have tons of information on its customers and its
employee all of that needs to stay secure you know when it comes to privacy it's a big topic lots of new laws and regulations are being passed whether it's laws such as payment PCI payment card industry DSS that's a very famous law to protection of credit card um gdpr which is used in Europe to protect personal information the world of privacy is changing and organizations such as Facebook is become is becoming more and more larger in terms of how much data they're getting get in those companies are going to maybe even start to be regulated
at some point let's see but your private information be aware when you're surfing the internet using social media sending out an email working in a company be aware what's happening with your private data anytime you go to a computer you're going to have to identify and prove that identity to a computer every time you walk up to your phone at least I hope so and your your computer at least I'm hoping it's going to prompt you to enter a password or a pin or put your thumbprint or something like that this is called authentication authentication
is when you're going to prove who you are to this machine the computer is like who the hell are you oh you're Andrew okay well then prove you're Andrew to me do you know something only Andrew knows do you have something only Andrew has are is there something unique about you that makes you Andrew there are the three types by the way to authenticate authentication is when you prove who you are so it's proven the identity of the subject subject is you the identity that you're proving is generally your username and how do you prove
it well that brings me to authentication so before I get into this I want to talk to you about three types of authentication what are the three ways to authenticate to a machine well let's take a look so type one now this is going to go by the way what I'm about to teach you is beyond the scope of this class but I think it's important to know and you're going to learn more about it in your other certifications so the first way type one is something you know something you know is going to be
a pin or a password answers to security questions you ever logged into a thing it's like oh where was you born what was your name of your first girlfriend what was your name what was your first car that's something you know something only you or specific people around you may know so but generally type one authentication is is your password or a pin type two is going to be something you have something that you're physically imp possession of this is going to be something like an RSA token which I'll show you a picture of uh
it could be a bank card or a credit card that only you have so only you should have your bank card and number three is something you are this is something a unique trait to you think Biometrics what's unique to me my temp print only I should have this thumb print and no one else in the world uh my facial facial recognition like you would have on an iPhone ey scanners or retinas Iris scanners hand geometry scanners so you have all of these different authentication types that are out there so they're basically three types something
you know pin or password something you have like a like a bank card or smart card RSA token or something you are think Biometrics let's go back to this now a single Factor authentication there's basically when you're authenticating you're either going to do a single or multiactor most systems today unfortunately are still single Factor single factor is when you only have to show one of the things so if you come up to your computer and you only have to put in a password that would be considered single Factor authentication in other words all you have
to do is just type your password in and you're done uh also if I come to my phone and I just put my thumbprint in here oops wrong Thum print put my Thum print in here and logs me in with my Thum print this is also a single Factor remember there was three types it's only using one of those types multiactor though so in single factor it's generally one of the types I explained multiactor is two or more two or more could be up to three right so for example multiactor is maybe you're going to
come out and you're going to use a password and a a temp print to log in so you go you put in your your your your username you put your password you press ENT then it says enter temp print you put your temp print and you login this is a more secure System multiactor Authentication is always more secure than single Factor authentication some systems are really complex you need to have three things they may say okay give you a password you put the password in insert the smart card you put the card into the system
now put your Thum print that's a three- Factor authentication right really multiactor when it comes to factors passwords and pins some systems has a one-time password you see this sometimes when you log into a system it may send you a code to your phone sometimes or it may give you a password that needs to be reset tokens now when you're talking tokens there software and Hardware tokens so a hardware token is one of these things this is like an RSA key certain Banks and organizations may give you out this there's a number on that key
that keeps changing all the time when you're login it's going to tell you hey give me the number on the key so you'll need to give them that a software token is basically this hardware token on your phone basically it's an app on your phone that displays the numbers Biometrics I mentioned already things like your facial recognition your thumb print uh I scanners and so on secure a specific location some apps wouldn't log you in unless you are get this right you are in a specific geographical region for example let's say you're work in an
organization they only allow United States people in the United States to access this data or to be authenticated to that data well it checks your IP address and if you're not in the United States not letting you in sometimes to log in you may need to answer a security question I mentioned these in general when you create the account you do this what was your first car what was the name of your first girlfriend or boyfriend what was the name of your third grade teacher security questions okay here's a hot topic for your exam something
called single signo this is referred to as SSO when you go to an organization all right when you go to an organization uh they have many servers they have a database server they have a file server they have an email server okay when you want to access a an application that Us in the database you want to access files you want to access a specific uh web page what do you have to do you have to memorize 100 username and passwords right I got to get a username and password for the email I got to
get a username and password for the database and the web application and so on maybe have 10 web applications what are you going to memorize all these passwords single sign on is a technology where it utilizes one username and password to log you into everything so you just log into this particular system and then you can access all of these different applications from your emails to your websites to your to five different websites to different devices on your network this single username and password can give you access to your email to your websites your databases
and all your files this is single sign on single sign on you find them on the Internet you log into to this one website because you log in here the credentials uh this is going to be using what's called saml talking about that another class the then can use that to log into a variety of other websites we don't have to put back your using name and password so single sign on is what it says it is you sign in once single sign on sign in once and able to access lots and lots of resources
or all resources on that Network in this video we're going to be talking about authorization accountant and non-repudiation three important terms you can need to know for your exam so the first thing up I'm going to talk about is something you all very familiar with it's authorization in the previous video I talked about authentication authentication is proving your identity to a system but when you log into the system system what can you access can you access this file can you access that folder can you access this application or that email what you can access is
dependent on what you are quote unquote authorized to access generally this is going to be set by your organizational policies and configured by systems and network administrators so let's go into this what is authorization well authorization is the permissions to what you have access to so if you can log into your network right now and you can double click on this file or that folder that gives you have permission to that but if you double click on a folder and it says access denied then you don't have permission to that so authorization is the permissions
we have to these things now there's a variety of different configurations on different systems beyond the scope of this class as your career grows in it you're going to see more of them the least privilege model so here's what this is the principles of lease privilege it security 101 we call this when you set up authorization in a network you have to follow the least privilege model in other words only give people the least amount of privilege they need to do their work so let's say Mary comes to work in the accounting department and all
she needs to do is make checks for bills all right so as the bills come in Mary makes the check does this is called accounts payable right because she's paying out all the bills of the business does Mary need to have access to all the customers information no Mary doesn't need that because Mary never deals with the customers so if the administrator configured it and gave Mary access to customers information that would be pretty bad in other words What's Happening Here is Mary has too much privileges she has too much permissions she should only have
what's needed to do her job and nothing more every organization should follow the least privileged model in other words give a minimum amount of access another way we could do this is what's called Ro based access based on a user account so role based access is this when you come into the organization you're play dependent on the role is dependent on what you have access to so what you're authorized to access so for example when you come into the organization you are you're you're in the accounting department or you're in the sales department or you're
in the finance or it what department you're in will determine what you're authorized to so people in the accounting department can access accounting database people in the sales department can access the customer relations management or the CRM but people in the accounting department cannot access the CRM and the sales can't access accounting this is people putting people into groups and assigning the permissions to the role this is how most organizations work this is how we always configure it this is best practices there are also a variety of user types sometimes you log in as a
normal user if you go to an organization and you try to change the system time or install software and you can't would you have a normal user account type another user cont is like power power users which they can install software but they can't really manipulate system settings or administrators on the machine in which case they can install software manipulate and change all system settings rule rulebase access control is controll and access into systems based on a specific set of rules so this is mostly used on routers or firewalls your firewall sits in front of
your organization's traffic all traffic come in has to get past this device this device has rules it's only allowing certain traffic if the administrator wants to allow certain types of traffic in maybe they're hosting an email server behind it and you want to allow email traffic in or out you have to configure that firewall that firewall is configured with rules this is called rule-based access control the other one is mandatory and discretion atory Access Control when you log into a computer can you change the permission of the file can you the user has the discretion
to give people permission to that file or that folder that's called discretion atory in other words the user has the ability to set the permissions on the files itself versus mandatory the system and system administrator sets that up in mandatory only the system or system administrator is going to have the ability to set permissions on the files in when you create it you don't own it doesn't really this it has a system owner not a user owner and only the system can set permission when you use a system okay every single thing is loged this
is called counter every single thing that you do on that computer every click you make every file you open everything you deleted is generally going to be logged in log files on those machines system administrators and network administrators will now have the ability to examine the logs on the systems on your machines on routers and switches and extract them for useful data maybe they have analytical data login is really important because it allows them to find errors or problems on the machines themselves it allows them to track specific trends that may be happening oh the
hard drive is becoming full oh users are going to websites they shouldn't be this includes web browser history every website you go to you think you go to uh the browser settings and clear your browser if it's in an organization they probably already tracked that and store that somewhere else you deleting the data now wouldn't really help you now non repudiation remember accountant means loging of data non-repudiation is a really important term you might you more than likely will see this on your exam here's what non- repudiation is repudiation is the ability to deny that
an event has taken place non repudiation is when the subject cannot deny an event has taken place what do I mean by that so let's say I'm a thief okay and I saw this big beautiful desktop on this on this on this desk so when nobody's looking I came in the room I stole the desktop and I ran out ran out ran out the office okay somebody stops me on the road and says hey did you steal that desktop the cops come did you steal that desktop and I said nope wasn't me I didn't steal
it what am I doing I'm repudiating this so repudiation is when the subject or the hacker or the bad guy is basically saying they didn't do it they're repudiating it they're saying it wasn't them so non repudiation is when they can't so the cops come to me and says Andrew you stole that desktop and I said I didn't steal anything wasn't me I'm repudiating that statement then the cop says well you know Andrew we have footage we have footage of you this video footage of you picking up that desktop and walking out the organization oh
crap really you have that footage okay you caught me I did it you got me obviously I can't lie now because look the footage is there now I cannot repudiate it you see non repudiation is really important in an organization if every action you do you will be held accountable for your action because the organization can always prove you did it they do this by doing a variety of things for example like what well they're going to videotape you on everything that you do there's a bunch of cameras around you they're going to ensure that
they that when you log in it's only you that could have logged in so let's say somebody stealed the data and your user your account was attached to it and you're saying well I wasn't me even though it was my account maybe somebody stole my credentials but how could they it's Biometrics no one has your thumb print maybe there's an electronic signature attached to it or there's a receipt that you took the information so non-repudiation is when the subject can't deny the action in the world of it security this is something you really want because
if people know they're going to be held accountable for any any and every action they take they're less likely to commit malicious action if you know you're going to get caught speeding every time you go over the speed limit you're probably not going to speed okay but if you know okay you may or may not get taught you might just speed that's the concept of non-repudiation it's a really important concept because with non-repudiation you're more than likely to get less attacks towards your organization let's talk about passwords in particularly how do we make secure passwords
and what are some password settings that we need to know first of all passwords are probably the worst way to ever authenticate to a machine but it is the most used way to authenticate onto today Biometrics is not something that we're going to utilize a lot especially on the internet we may use it to log into our phones and mobile devices and even our desktop but most of the websites and apps we use on these devices are basically password base so we have to understand some information about passwords let's get to it the first thing
up is the password length this is really important the longer a password the more harder is it to crack you see in order to crack a password one thing that hackers do is called a Brute Force attack in which case they guess every single combination Within the alphabet itself hackers now nowadays can guess millions of combination every single second so let's say you have a password that is out of the dictionary well there's only 300,000 words in the dictionary they will crack your password like that so because they can try millions of combinations a second
the more longer your password the more longer it will take to crack you see there's one thing I want to make you guys understand no password is on crackable a computer sitting sitting calculating different variations of password will eventually guess every single combination of every single letter on a keyboard it's just a matter of how long some complex password that's maybe let's say 16 characters that's has uppercase lower case in it symbols numbers in it may take 30 million years to crack at that moment it's un it's not really feasible but it will so in
theory every password is crackable what you want to do is you want to make it as so hard to crack that they don't even try so a password length in today's world we want to say that a good length in today's world would be at a minimum of eight characters and 10 is probably going to be a good one 8 to 12 I would say 10 is probably a good number in today's world in fact a lot of applications you know you read older password manuals it would have said eight nowadays a lot of apps
and websites specifies 10 you also want to make sure your password is complex you see if you don't have complexity enabled these are settings by the way on password when administrators configures their systems they should enforce a minimum length you don't want people with six characters with password complexity they're going to have to have some things like a symbol a number they might have to have a lowercase a uppercase a they're going to have to have all the different combinations on your keyboard this would increase the complexity so let's say your password is all lowercase
dog dog it'll crack just like this because there's no complexity to it and it's very small another thing we want is password history so password history and expiration are two terms that are very confused password history is how many times you can reuse the same password a lot of times password expires let's say it expires in 60 days in other words every time you log in you got to change your password every 60 days the problem is if if you do password expiration and there's no password history people just keep reusing the same damn password
it's not uncommon for users to use the same password over and over and over we don't want that so password history we may say 12 so in this case they can't reuse the last 12 passwords so every time they make a password they have to make a different password so that's password history password reuse across website don't do it okay don't do it because this is what this is you have one password you use across every single website I get if I ever break that password or crack that password I know everything about you you
use the same password for all your banking website and your Amazon and your email so if I crack that password or it mistakenly gets pushed out in the while they can literally find everything about you and bring you down don't do it there's a variety of password managers out there so I use last pass I'm literally telling you that this dash lane these are password managers where they store the password for you I know it is impossible to remember the amount of passwords because of the amount of sites out there every every site you go
to wants you to put in a password password managers things like last pass will create password stores the password for you and when you go to the website it'll type it back in I have last password my phone and my desktop I don't remember passwords I have some crazy complex password like 16 digits for all the websites I go to and I don't remember any of them because the password I just go there I select the site password manager puts it in for me my phone and my desktop once in a while people will forget
the password there is a process to reset in these password what is the process well the process to reset a password you might have to click password reset you put in your email you'll click next and they'll send you a link to your email that's one way in organizations you may have to call the the help Des support line they'll authenticate You by asking you unique information be an employee ID they'll send you a reset link maybe to your phone or to reset it and give it to you over to form there has to be
a way to reset the password it is a given that people will forget their password at some point and there has to be a way to reset your password before I use last pass you know how many times almost every time I log into most websites I have to reset the password because I try to make complex password then I forget them so make sure you get a password manager because even though it's the least way to authenticate it's still the most Ed in this video let's talk about encryption so encryption is of course you
know when you think of it security you think of encryption it's of course the most talked about topic without the world of encryption there would probably wouldn't be Security in fact when you think of securing your data you're probably thinking about oh no unauthorized access or confidentiality right when encryption is the way we're going to make this happen when we encrypt data plain data data that's not been encrypted that anyone can read that's called PL text so plain text is data that you can see the other one we have is something called Cipher text so
Cipher text is the encrypted data so when what is known as an algorithm an algorithm is a mathematical calculations on your data that outputs garbage data data that you can't read I can't read unless you know how to decrypt it with what's called a key so plain text is readable Cipher text is the encrypted version of the data that hopefully no one can decrypt unless they have a certain key now encryption is used all over we're going to use encryption when we're going across uh from you to Amazon Amazon uses the SSL or TLS transport
layer security to encrypt your data this is going to ensure that the data Traverse in the line what's known as data in transit is fully encrypted now encryption is basically going to apply to data two ways data add rest and data in transit data lies in three states by the way add rest in transit or in use that means the data is actually being used now encryption mostly applied to data at rest and in transit so let's talk about this the first one is data at rest so when data is at rest it's basically being
stored on your computer it's on your dis it's on your hard drive it's a file of itself could be even be stored on your mobile device in order to do this we utilize certain forms of encryption where we call file system encryption this is like when Windows would encrypt files on an NTFS partition you can also encrypt it by utilizing Hardware chips something called TPM trusted platform module this is a chip that's installed on your computer that carries an encrypt that carries encryption keys to actually Hardware encrypt the data itself now data add rest encryption
is very important because if somebody let's say say my phone I have some seriously uh secret data and somebody steals the phone takes out the driver tries to analyze the drive can they get the data off no because it's fully encrypted on the phone itself they would have to have the decryption key data in transit so data in transit is when Amazon is sending a user information this data right here has to be in C PT encrypted how is it doing that but Amazon is sending the data using HTTP right hypertext transfer protocol this transfers
web information but they're using https https specifies that it's using TLS also known as SSL TLS is the upgrade testl secure socket layer or transport layer security learn about more of these in security class but this means that it's fully encrypted between Amazon and the user you can also use encryption for things in emails this is software called pgp that would encrypt emails when you send emails to people you may have confidential data in there you want that encrypted when you are working from home no this term for your exam when you are working from
home let's say you have a home user or a Home worker and you have a company the company has a big land a network by itself the user is connected to the internet so is the company for the user to access let's say you're a home worker right you're you work from home you're one of those employees you want to be able to access the company's information their database their files um their emails and so on what you're going to do is you will connect through a VPN a virtual private Network a virtual private network
is basically an encrypted tunnel between the home users and the company's information what this does is that all information being passed between you and the company is fully encrypted and that's what you want all right so vpns are really important when it comes to vpns are really important when it comes to working from home or accessing company resources sometimes we use vpns between sites between this site and this particular site also we'll use a VPN mobile applications mobile applications are basically going to use https or some form of uh SS based encryption in order to
encrypt the data from them now the world of cryptography is a massive World massive world I teach massive levels of cryptography and certification such as cisp CH and a little bit in Security Plus if you're interested take those certification but trust me you can't have Security in the world of it without encryption I've always told every it manager and system administrator and Network administrator the same thing it's not if a disaster is coming it's only a matter of when it's not if you're going to have a major weather event such as a hurricane flood it's
just when it's not if you're going to lose power in your city one day it's just when it's not if the server is going to hard driver is going to blow out or its power supply dies it's just a matter of when and in the world of it you should be expecting this when you go to work every day the beautiful thing about it is you never know what the hell happens you could be leave your network functioning perfectly one day and you go to work or you go home that night and boom the whole
thing drops because a system died a switch died a router died there was a power outage the system got flooded the AC broke and broke the flood the server all types of weird things happen we have to be prepared to handle quote unquote faults a fault is when the system gets hit it's when the system drops how do we build quote unquote fault tolerance systems systems that are capable of taking a fault it has a tolerance of basically being broken and in this section I'm going to go over some of those things here which we're
also going to talk a disaster recovery Planet so one of the things here we could do is replicate systems systems replications means this what Data Centers do is they have one Data Center and they replicate it to another one so for example Amazon all the Amazon servers are not just just in one building CU if that building ever drops then the whole thing dies they're probably going to replicate that to another building so replication all the data that's here is being replicated here that way if this building drops this one stays up replication of this
like cyto side replication is not going to just be in in one city they're going to replicate across different cities so for example they may have one in New York and have one all the way in Texas that way weather events in Texas is definitely like there going to be different weather events in in New York and so on redundancy well things will drop redundancy is having more than one of something for example power just don't have one line of power if you have the main line of power from your power provider you may have
a generator or a UPS generators machines that generates power from gasoline or natural gas in case you lose power from your main power provider networking and data lines so for example you may have internet lines instead of having one inter one type of Internet line from Verizon you may have a line from Verizon a FiOS line from Verizon but you may have a satellite internet from another provider notice two different providers two different types of lines that we want when not if when one goes down hopefully the other one still works if it's the same
type it may not work when it comes to backup I mentioned something earlier in the class no backup no restore you should be backing up your data at all times all data should be back up the files that we use pictures movies music files in organization might be data files text files spreadsheets Word documents critical data maybe that new research project you're working on maybe your company's pii of of employees and its customers the personally identifiable information databases that stores Mass amounts of customer information or organization processes OS backup you should have a backup of
your different operating system in an organization don't think you're going to just use 1os you're going to have Windows 10 but you may have different version of Windows Server you may have different configurations of these operating systems for different machine the way um the way um you configure an accting machine is different than how you configure the sales machine the accountant machines don't have QuickBooks or accountant software but it does have a CRM back up your data when you're thinking about backup when you're thinking of well where do we store these backup just don't have
a backup that's stored locally have a backup that's stored offsite not just onsite but offsite uh store it in the cloud this is very famous put it in things like AWS or Amazon web services a lot of people now including TI we store our backups in the cloud back in the days people when there was no cloud storage you would make a backup up of this data center and stored in another data center so let's say you only have two data center one data center stores the backup of the other the other one stores the
other of the other if that make sense so you would basically have offside backup what if the whole building Burns one day and if all your backups are in that building not only did you just lose all your machines and your data you also lost your backup it's good practice to keep your backups off site uh in if you don't have a physical off site put it in the cloud contingency plan when things break what is the plan what is the plan of how we are going to rebuild these systems how are we going to
continue working while the systems are being rebuilt do we have another data center that data was replicated instead of just talking about it and having a set of different uh processes here and processes there this is how you recover this this is how you recover this this is how you recover that server this router put it together in a big plan called a disaster recovery plan in it you're going to have that contingency plan in there now Disaster Recovery plans is going to talk about data restoration how are we going to do that how are
we going to prioritize the data restoration and restore an access to users you should have plans in place for this now let me go into some examples when there's a disaster okay when there's a disaster and the whole network drops what is the prioritization of what's restored first you restore your website first let's take everything is dead phones websites email access to data what do you restore first the website the data access the email or the phone every organization is different every organization has different prioritization this needs to be determined when you're restoring access how
do you restore that access is there a method or a procedure that has been documented God forbid what if the it security person died in in the accident or the disaster what if the building burned and no one knows how to restore access how do we restore access in what prioritization do we restore access and is there a procedure on authorization document such as do we need a sign off to give this person access now that this person has passed away or is not available and then how to restore data and where to restore it
in the world of Disaster Recovery I'm going to go a little farther than your exam would the whole concept of Disaster Recovery plan and the whole concept of how do we build a plan that if the organization gets hit with a major disaster hackers breaking in weather weather phenomena our events how do we respond and make sure that organization keeps running and people don't even know that our systems were down these are plans that need to be put in place and we need to have good full tolerance systems UPS's and generators clusters in case servers
drop another one can kick in called fail of clusters data replication between buildings this topic can get very big very fast just keep in mind that when you're working for an organization it's not a matter of if you're going to get a disaster is just when and you always want to be prepared
Related Videos

10:31:38
CompTIA IT Fundamentals (ITF+) FC0-U61 Ful...
Tech Gee
359,271 views

10:37
Why Cybersecurity Training is a SCAM
Technical Institute of America
361,249 views

17:35
I Quit my $175k Cybersecurity Job ‼️ | The...
TechTual Chatter
122,181 views

2:11:49
100 Network+ Practice Questions, Exam N10-009
Technical Institute of America
68,259 views

4:08
CompTIA A+ vs. Google IT Support Certifica...
IT Edge with Asim
3,373 views

13:48
How To Learn Any Skill So Fast It Feels Il...
Justin Sung
1,825,524 views

14:30
How I Passed Network+ N10-009, Exam Tips a...
Technical Institute of America
27,449 views

1:10:03
Security+ Certification SY0-701 50 Practic...
Technical Institute of America
227,351 views

1:27:06
CompTIA A+ Full Course for Beginners - Mod...
BurningIceTech
367,502 views
11:32
The Ultimate Network+ N10-009 Study Guide ...
Technical Institute of America
19,891 views

22:16
A+ 30 Day Study Plan - Free Download
Technical Institute of America
9,796 views

2:47:53
CompTIA IT Fundamentals Full Course for Be...
BurningIceTech
25,499 views

8:17:18
CompTIA ITF+ (FC0-U61) - Full-Length Train...
Certification Cynergy
71,404 views

15:32
How To Pass the CompTIA Security+ 701 Exam...
Symoné B. GovTech
119,208 views
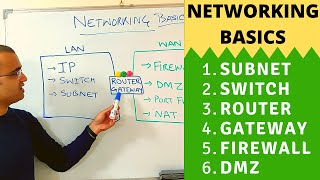
14:58
Networking Basics (2025) | What is a switc...
IT k Funde
5,586,708 views

1:34:48
50 CISSP Practice Questions. Master the CI...
Technical Institute of America
215,554 views

4:33
Cyber Security is Not Hard
Lerna Courses
8,561 views

3:18:32
CMD - Command Prompt Training for IT Profe...
Jobskillshare Skills-Based Platform
1,609,999 views

30:00
How to Get an IT Job Without Experience
Professor Messer
467,904 views

16:55
Cybersecurity Trends for 2025 and Beyond
IBM Technology
398,276 views