CSMA/CA with and without RTS/CTS
32.02k views1869 WordsCopy TextShare
MrBrownCS
The wireless protocol CSMA/CA (Carrier Sense Multiple Access/ Collision Avoidance) is really importa...
Video Transcript:
hello I'm gonna be taking you through the protocol csma/ca which stands for carrier sense multiple access with collision avoidance which is a absolutely horrible sounding protocol it's really not as bad as it sounds this is a very dramatic name for is quite a simple in essence protocol so make sure you remember what this is because you might be asked to expand the acronym in an exam so carrier sense multiple access with collision avoidance and the right path in because there is a version of this for Ethernet which is sash CD collision detection but this is
for Wi-Fi so why fight is a group of protocols this is one of the protocols which Wi-Fi uses one of the most important ones in wife over nodes were connected to vanilla is said to have random access to the channel the channel being where were actually pushing related food in this case is V air because we're dealing of wireless communication so this means the term random access means for the nodes that are connected can transmit whenever they need to they're not allocated a time of day to be able to communicate why don't they need to
transmit something they'll do it without restriction this does produce an issue which was whole protocol was about avoiding which is the fact that if you transmit at the same time someone else is transmitting quite possibly you're going to interfere with their signal and boasting those are going to get corrupted they're gonna it's going to result in data loss that sounds quite serious mrs. B's term is a data collision hence why for collision in the name here but it's not as serious as it sounds what happens all the time the protocols are designed to deal with
this photos retransmitted the data happens all the time the only issue is if it's a very busy network this is likely to happen a lot and it will kind of further slow down by network by having to we transmit to the data when it gets lost so it's better to avoid as many collisions as you can the forward slash here helpfully splits his protocol up into two aspects the first of which is we see SM Ava carrier sense multiple access and so this has sort of two tenets the first of which is for the nodes
will listen to the share channel they have access to they can receive with a network interface card they can receive for wireless communications they can listen to a channel that's where carrier sense part of this and if a medium is not idle if the channel was not either of someone else's transmitting they won't transmit this is fairly common sense if you want to avoid a collision don't transmit when someone else is transmitting because that's just gonna call this one having said that collisions can still occur if two nodes are transmitting at the same time they
will have both waited for the channel to be clear and transmitted at the same time so that is obviously a slight issue but it's better than if they transmitted without checking first the second part of a protocol was see a bit is trying to counter this and services collision avoidance and what this does is to avoid the collisions it'll wait for a random amount of time when the channel is busy otherwise as soon as we tap so if all these devices are waiting to transmit and they're waiting for the channel to be clear we're going
to send at the same time unless they are waiting for random amounts of time so if we can put this in a flow chart it's really useful if seen an exam question which asks you to do this in the exam so it's useful to be able to do it so you start off this process and what you're doing you're checking to see if the channel is idle you're doing with sensing and if it is idle if it's free they'll just transmit the data that's fine and we can finish up if it's not idle it's gonna
wait for a random amount of time before checking again if it's as I say if they are all waiting at the same time and all transmitting at the same time we're just gonna get an infinite loop of at our not being idle and also just collisions occurring such is the nature of computer science here quite a few ways to optimize this avoiding step for back off time one of them might be if you get stuck in a loop where you keep going round you might instead wait for slightly longer amounts of time just to try
and give the network a chance to get free of its congestion that might be a good idea but as long as you know it's random that's gonna be fine for now if it was say wait for five milliseconds all of the devices are gonna wait for five milliseconds and then transmit that exact same time but do you see me so we talked about before so it's really important to random but part from that this is as detailed as you need to know just to try and throw in another slightly different term which is often packaged
with this topic by examples in particular the fact that for Wi-Fi over Wi-Fi protocol part of the protocol is when you send a message to a receiver the receiver will then send you back acknowledgement message when they receive it and it's written as ACK or ACK for sure why don't you send a message the stopwatch is kind of starting and it will wait to receive the acknowledgement if hasn't received in a set amount of time then the date will be retransmitted because a collision has occurred and this amount of time might be dynamically calculated it
might be calculated based on how congested the network is again it's another kind of optimization to make this as efficient as possible I ran out of space because another decision box saying has been lodgement been received yes that's fine if it hasn't we're going to go back to the start and wait again and do be so process you can't jump back in here because it might be busy and that'll cause another collision in its current form where this protocol does have another issue which is for hidden nodes problem and this is all about the fact
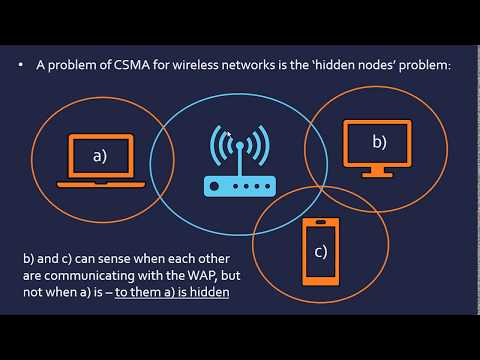
that we're sort of in a way orbiting this wireless access point which is providing the wireless network so we're going back and forth for this maybe this is a wireless router and the issue here is that C and B can both see each other they're both within the same range of each other and so they can communicate for wireless access point and also they can view when each other is communicating so they can both sense each other but when a is communicating they have no idea that it's communicating even mode is in range with the
wireless access point they can't view its communications because their range isn't far enough this means two B and C AE is hidden and vice versa - a B and C a hidden which means when they try and sense to see if the channel is idle they're not going to be able to know if the other person is transmitting but soon as the data enters this range it can start to collide a way to counter at this problem is to add another aspect onto a protocol which is RTS CTS request to send clear to send so
the title becomes even more convoluted but we see what the concept is is quite simple one of the six that once we notice determined for for channel is clear it will double check by sending a request to send message to the wireless access point and then if a channel is clear it all gets a clear descent message back so we'll get the all-clear back from for one seconds point and it will transmit and so if we just look at this in terms of the entire flow charts this bit here is just the same as before
we've still got the core protocol underneath but once it has got so before we just transmit the data once we determine that it's clear but because of a hidden nose problem we're now gonna transmit first of all in RTS just to request access just a double check in other words and I'll get one back and we can transmit it if it doesn't get one back you might get a negative or it might not actually receive one it'll go back and just wait for a random our time and start with process again so if we look
at how this fixes for hidden those promoted and safe fixes but makes it better it's because even if a node is hidden from another node it can still receive at least one of these messages because for wireless access point is for core of its whole network it's all-seeing it's all-knowing it knows where the channel is ID or not because it has access to all the devices that are connected to it so if this device here is sending a message to the wireless access point it will first of all send the ready to sent message which
this device here can't see but that's ok because it can sievert clear to send message that's it within its range and then the packet can be sent with less risk of collision occurring so you may be reiterate without this additional step if both devices wanted to communicate at the same time they'll both fall over csma/ca part and waits for the channel to be clear or central it's clear because in their point of view is and the wave transmitting at the same time and this may cause a collision in this part of a network and obviously
if a wireless access point can't process both messages at the same time so one of them is gonna have to retransmit if not both if the collision does actually occur so this step is good for avoiding the collisions but it does it does add an overhead to each packet because you have this additional back-and-forth which has to occur before the packet sent so more time is taken and the now of yourself may get worse for congestion may get worse because you're having to send all ways of messages these messages ourselves could get they could collide
so it just makes the whole problem slightly worse and in that case so it is relatively common to deactivate this part for small packets because we're small packets if they do have to be resent that's not really a big deal it's very quick to resend them by large packet it might be worth adding this additional overhead to make sure if it doesn't have to be retransmitted
Related Videos
8:52
The Internet and the World Wide Web
MrBrownCS
101,564 views

6:14
CSMA/CD and CSMA/CA Explained
PowerCert Animated Videos
633,328 views

10:02
Hidden / Exposed Terminal Problem -- RTS/C...
ComNets Bremen
1,313 views
15:37
WiFi | CSCMA CA with RTS & CTS
Lazy EDU
1,080 views

13:48
How To Learn Any Skill So Fast It Feels Il...
Justin Sung
1,393,884 views

1:24:02
The Basics of Wi-Fi 7
Devopedia
2,123 views
16:38
WiFi | CSMA/CA with Backoff Timer | Example
Lazy EDU
1,902 views

13:01
7 FATAL Wiring Mistakes Most DIYers Don't ...
How To Home
9,018,118 views

13:09
Captain Steeeve Analyzes Near-Miss Inciden...
Captain Steeeve
132,087 views

17:19
How WiFi Works - Computerphile
Computerphile
203,153 views

25:06
Bernie Sanders Dismantles Elon Musk, Mark ...
electron media group inc.
1,050,596 views
5:18
CSMA/CA - Wireless Medium Access Control P...
Sunny Classroom
78,993 views

31:11
Ethical Hacker: "I'll Show You Why Google ...
Top Master
1,996,954 views

12:38
Even EU Shocked by Germany’s Bold Move Aga...
PPR Mundial
2,040,244 views
27:57
2 2 CSMA CA
CIS UOD Videos
17,509 views
7:37
Network Types and Performance
MrBrownCS
86,396 views
24:52
The Most Useful Thing AI Has Ever Done
Veritasium
6,945,252 views
5:24
Hidden Terminal Problem (CSMA/CA) RTS-CTS ...
HowTo
70,224 views
8:33
Wireless (WiFi) Frames - Three Types to Un...
MetaGeek
28,431 views

5:59
CSMA/CD and CSMA/CA || Simply Explained
Waqas Tech Videos
15,083 views